Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
What is ICMP? The Protocol, Port Number and PING!

UPDATED: December 4, 2023
Internet Control Message Protocol (ICMP) is located at the Network layer of the OSI model (or just above it in the Internet layer, as some argue), and is an integral part of the Internet Protocol suite ( commonly referred to as TCP/IP).
ICMP is assigned Protocol Number 1 in the IP suite according to IANA.org.
Designed to act as an error reporting and query service, it plays a crucial role in the host-to-host datagram service in network communication. It is the part of the IP service that acts as the feedback system in network IP communication, making sure that undeliverables packets are reported to the sending host, such as the router or the gateway.
Any IP network device can send ICMP datagrams, including network interface cards and other devices that are commonly used in your environment.
What is ICMP?
What is ICMPs role?
ICMP’s role in network communication can be likened to a team that is assembling an automobile using parts being sent from the manufacturer. The manufacturer is sending the parts one by one, assuming that they are being received by the assembly crew.
Handling Missing or Delayed Parts
Occasionally, though, a part does not arrive as scheduled, or parts are being slowed down via their usual delivery method and a faster way of getting parts to assembly exists. The assembly crew needs a way to notify the manufacturer to resend the missing part or to send the parts via a different, faster shipper or route.
ICMP as a Messenger
ICMP plays the role of the messenger that relays information from the receiver to the sender. This protocol is a fairly complex. Not only does it report undeliverable packets and unreachable hosts, it also sends redirect messages, echo, and echo reply messages and others discussed below.
Echo/Echo Reply Messages and ICMP Feedback
(Echo/echo reply messages are used by the well-known PING command, which allows a user to send an echo to a receiving host, which sends an echo reply if an echo is received). ICMP messages provide the system with a way to notify the source host if the remote host is not receiving the transmitted packets. ICMP does not help IP be more dependable and it does not receive or send any actual data. It simply exists as a feedback system, a resource to identify problems with lost packets and broken data routing.
Destination Unreachable Message
One of the most well-known and useful messages in an ICMP datagram is the Destination Unreachable message. Destination Unreachable messages are generated for several reasons, including being unable to reach a network, a host, a port, or a protocol.
A router sends these Destination Unreachable messages back to the host, which then usually sends it to the application that generated the original packet. The error messages let the application know to try again and, if needed, the host application can generate an error message to the user of the application, notifying them of network connectivity problems.
Overview of ICMP Messages
It is important to know that even though Destination Unreachable messages are the ones that people know best through the PING utility, they are not all that there is to ICMP. Other important messages include the Redirect message, which a gateway uses to let the host know to send traffic to a different router. Time Exceeded is used by a router to tell the host that a packet has exceeded its Time to Live (TTL) and has been discarded; when a host starts receiving Time Exceeded packets, it may be an indication that a feedback loop exists somewhere downstream.
Router and Host Communication
Source Quench messages are sent from a router to a host, letting it know that its buffering capacity is full and to briefly pause transmissions to allow it to catch up. Other types of messages include Parameter Problem, Address Mask Request & Reply and Timestamp, among others.
Avoiding Feedback Loops and Network Flooding
ICMP will not send messages about ICMP messages; if this were to happen, it would create a feedback loop – a returned ICMP message would generate an ICMP message back to the other side, which would generate another message, and so on, creating a storm of ICMP packets that would quickly flood a network. For this same reason, ICMP will not reply to broadcast or multicast addresses. Unlike other IP protocols such as TCP and UDP, ICMP does not exchange data between hosts.
User Interaction and Diagnostic Tools
As a general rule, end users do not interact with this protocol except for a limited number of diagnostic tools, such as ping and traceroute, used to troubleshoot network and Internet connections.
Security Concerns: Attacks and Prevention
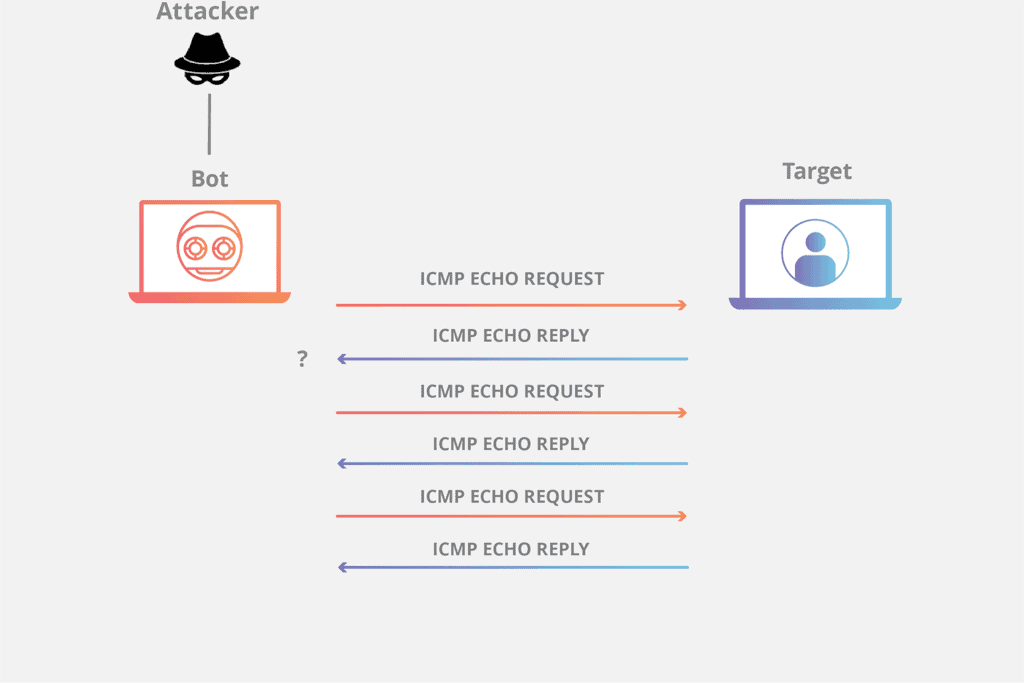
ICMP can be exploited to attack computers with what is known as the “Ping of Death”, which is a common Cyber attack that can cause Denial of Service issues in your networks. An IP packet designed to overflow a target computer’s buffer is sent in an attempt to crash its system. Another attack consists of floods of ping requests that prevent normal traffic from getting to the targeted computer. These attacks are relatively simple to prevent by implementing checks of IP fragments in the reassembly process.
Structure and Protocols of ICMP
ICMP messages are datagrams encapsulated within IP packets, and is used by both IPv4 (ICMPv4) and IPv6 (ICMPv6) protocols. These packets start with an IP header, followed by the ICMP header, type and code, checksum, and data. The data depends on the type and code fields, which identify the ICMP message being sent.
Importance of ICMP in IP Network Communication
One of the most important parts of the Internet Protocol suite, ICMP serves a crucial role in IP network communication. It ensures that a transmitting host knows if its packets are not being received by the remote host, providing crucial information regarding network problems as well as helping hosts transmit data more efficiently. Network technicians and administrators also use it as a diagnostic tool to help identify points of failure in the network. An ultimately indispensable tool in our constant, endless flow of billions and billions of IP packets sent around the world every second of every day.
What is ICMP used for?
The Internet Control Message Protocol, or ICMP, is a basic unit of the Internet's communication infrastructure. ICMP is responsible for providing internet operations, diagnostics, and solving issues. These aspects are usually ignored by users in their everyday usage. Though it offers unique features, it is still risky because it is sometimes breached by cyberattacks like distributed denial of service (DDoS).
ICMP acts as a means to communicate with devices sharing the same network. It helps in transferring important data about the status of the network, diagnostics, or error messages. The primary function of ICMP is to report errors that occur while transferring information. Consider this example to understand: in case a router finds a data package that it can’t transfer, it will convey an ICMP message to the starting point of the IP address, giving it information about the problem. ICMP makes the ping command easy and enables devices to check connectivity by dispatching an ICMP Echo Request and acquiring an Echo Reply. This helps in identifying network issues and estimating latency.
How is ICMP used in DDoS attacks?
ICMP offers so many benefits but still has a risk of DDoS attacks. In a DDoS strike, a large number of infected devices bombard the target network or server with an enormous bulk of traffic, causing a service outage. ICMP flood attacks caused the worst ICMP exploitation by attackers. The attackers sent a large volume of ICMP echo requests to the target servers; they also ate up all their resources and blocked legitimate users from accessing them. These kinds of attacks are hard to handle as they hit at the heart of ICMP functions.
To take care of these threats, strong cybersecurity actions are important. The administrator of the network usually installs a prevention system or intrusion detection system that can filter out or identify unusual ICMP traffic patterns. Also, limitations on the rates can limit the number of ICMP requests a server has to react to in a particular timeframe, which will also mitigate the negative impacts of flood attacks.
Conclusion
ICMP is the most important protocol that allows efficient diagnostics and communication on the internet. It should be used responsibly to ensure network health and resolve connectivity issues. Although strong cybersecurity actions are of utmost importance due to the potential threat of DDoS attacks. We can safely use ICMP, enjoying its benefits along with protecting the digital infrastructure from the threats of DDoS attacks, by taking the necessary preventive measures.
ICMP FAQs
Why is it that an ICMP packet does not have source and destination port numbers?
ICMP, the Internet Control Message Protocol is part of the TCP/IP protocol suite. ICMP relates to the Internet Layer, whereas port numbers are only found in the Transport Layer, which is the layer above.
What is ICMP protocol?
ICMP stands for the Internet Control Message Protocol. It was designed to provide administrative functions to Internet transmissions. Examples of its role include status checks and error messages passed between two devices across a connection.
What layer is ICMP?
ICMP is part of the TCP/IP protocol stack and it is found at the Internet Layer. This is actually the second layer up in the stack. ICMP is referred to as a Layer 3 protocol. This number comes from the Network Layer in the Open Systems Interconnection (OSI) protocol stack. The Network Layer in the OSI model is the thirds up and it equates to the Internet Layer in the TCP/IP stack.
Does ICMP run over IP?
Yes, ICMP sends messages to a source IP address. All IP-based network devices have the ability to send and receive ICMP messages. However, ICMP can be turned off, eliciting an error or failed response. This common tactic is used to limit an environment's exposure to ICMP related attacks.
Can hackers use ICMP?
Yes, hackers can use ICMP for a variety of attacks. Many of these attacks can be prevented by limiting ICMP traffic volumes and destinations in your firewall. In some cases, it may be appropriate to disable ICMP. Many content delivery networks can automatically block these attacks.
Ping sweeps
Hackers can use the ping command to scan a range of IP addresses and determine which ones are active. This can help them identify potential targets on a network.
ICMP redirect attacks
This type of attack is used to manipulate routing tables on a network, allowing the attacker to redirect network traffic through a device under their control.
ICMP tunneling
Hackers can use ICMP to create a tunnel through which they can transmit data, bypassing firewalls and other security measures.
Smurf attack
A Smurf attack is a type of denial of service attack in which the attacker sends a large number of ICMP echo request packets (ping packets) to the broadcast address of a network, with the source address spoofed to be the address of the intended victim.
ICMP flood attacks
This type of attack is similar to a Smurf attack, but instead of sending a large number of ping packets, the attacker floods the target with a high volume of ICMP packets, overwhelming the target and causing a denial of service.



