Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
The Best Network Security Auditing Tools

UPDATED: February 28, 2024
A vulnerability in your network will leave your entire business exposed to threats. You need to audit your network security.
You know you need network security but how do you know that it’s good enough? How do you know that secure working practices are being followed and all of your security settings are protected against tampering? You need to check your network security systems constantly. You also need to assess the efficacy of those systems periodically.
Network security auditing provides those periodic assessments and it has two aspects: potential vulnerability and historic performance. Data protection standards demand security auditing, not only to ensure that the strongest security is in place but also to identify whether successful attacks have taken place.
Here is our list of the best network security auditing tools:
- SolarWinds Access Rights Manager – EDITOR'S CHOICE An access control system that helps protect the user accounts and device access. This tool also includes extensive network and system auditing tools. It runs on Windows Server. Start a 30-day free trial.
- Intruder – FREE TRIAL A cloud-based monthly vulnerability scanner with an on-demand scanning function, software inventory analysis, and the services of a pen-testing team. Start a 14-day free trial.
- ManageEngine ADAudit Plus – FREE TRIAL Analyze user access accounts, log user activity, and audit the system for data security standards. It runs on Windows Server. Start a 30-day free trial.
- Papertrail – FREE TRIAL A cloud-based log manager and audit archiving service that includes data searching and analysis features. Register for the free trial.
- ManageEngine Log360 – FREE TRIAL This SIEM includes log management for an audit trail and also provides compliance reporting. Runs on Windows Server. Start a 30-day free trial.
- LogicGate A cloud-based IT governance, risk assessment, and security standards auditing tool.
- Splunk Enterprise Security A network security system that includes incident response auditing and standards compliance auditing.
- Netwrix Auditor A network security auditing tool that includes configuration management and protection. It installs on Windows and Windows Server.
- Acunetix A suite of software testing tools that focus on the vulnerabilities in Web applications. It is available for Windows, macOS, and Linux.
- Nessus A vulnerability assessment tool in free and paid versions that includes auditing reports. It is available for Windows, macOS, and Linux.
Data security standards bodies don’t blacklist businesses that have been hit by an intruder and suffered data disclosure. This is because the unlucky business that is the first to be the victim of a new attack strategy can’t be blamed for the unpreparedness of all cybersecurity systems in the world. In these cases, the victimized business is expected to admit the security breach and inform all of those individuals and businesses whose data has been compromised.
The knowledge that auditing requirements are eventually going to reveal any security breach drives the demand for businesses to spot successful attacks as quickly as possible and implement mitigation procedures – even though the data leak has already occurred.
So, there is a close link between network security systems and network security auditing tools. While network security processes survey the network, they simultaneously record all conditions on the network second by second, laying down the necessary data stores that network security auditing needs. When you look into network security auditing tools, you also need to consider the audit-related features of network security systems.
The Best Network Security Auditing Tools
Our methodology for selecting network security auditing tools and software
We reviewed the security auditing market and analyzed the options based on the following criteria:
- Speed of the audit
- Customization of reporting and monitoring features
- Ability to automatically audit networks and schedule scans
- Graphical interpretation of data, such as charts and graphs
- A free trial period, a demo, or a money-back guarantee for no-risk assessment
- A good price that reflects value for money when compared to the functions offered
You can read more about each of these options in the following sections.
1. SolarWinds Access Rights Manager – FREE TRIAL
The SolarWinds Access Rights Manager gives you an interface to Active Directory (AD), SharePoint, and Exchange Server. These three services can have many implementations within one company and the access rights systems operating on different sites or for different departments might need to be unified or kept separate, according to the business’s security policy. The complexities of different access rights strategies can be difficult to manage, so a specialist tool, such as this can help you track and control access rights more effectively.
Key Features:
- Access Reports: These reports help administrators understand user permissions and track access activity to ensure compliance and security management.
- Permission Analysis: Permission Analysis allows administrators to analyze and audit access rights across their IT environment, such as over-privileged users or unauthorized access.
- Active Directory Management: This makes administrative tasks more easier and ensures efficient user lifecycle management.
- File Server Management: you can manage your file servers, protect sensitive data, and ensure compliance with regulatory requirements.
Why do we recommend it?
SolarWinds® Access Rights Manager (ARM) assists in delivering customized Active Directory (AD) and Azure AD reports. These reports reveal who has access to specific resources and when they accessed them. Additionally, ARM helps manage Active Directory and file servers, providing administrators with tools to oversee access permissions and ensure security efficiently.
While letting you coordinate issues such as replication and backup, the Access Rights Manager also lays down data sources for network security auditing. As well as logging all actions taken within the AD environment, it stores records of user account activity and device access events. These activity log messages are all timestamped. This enables you to quickly trace through and see which account was accessing which resource at the time that a security incident took place.
The log files that the Access Rights Manager creates are useful both for internal network security auditing and for external audits. These records need to be archived over a long period for access by compliance auditors. Implementing a log archiving strategy for these Access Rights Manager records will enable you to demonstrate compliance with GDPR, PCI-DSS, HIPAA, and other data security standards – passing any standards audit with ease.
Who is it recommended for?
SolarWinds® Access Rights Manager (ARM) is recommended for IT and security administrators. Experts in these fields use this tool to efficiently provision, manage, and audit user access rights to systems, data, and files. By doing so, they can safeguard their organizations against potential risks such as data loss and breaches.
Pros:
- Excellent integration with Active Directory: Access Rights Manager seamlessly integrates with Active Directory, providing comprehensive access management capabilities tailored to AD environments.
- Change tracking in Active Directory: you can track in detail the changes made in Active Directory to ensure robust security with audit requirements.
- Access approvals for different group memberships: it has a feature for managing access approvals, which allows you to control and monitor user memberships efficiently.
- Process improvement: it provides insights into user permissions so that you can enhance processes and strengthen security measures.
Cons:
- Email generation could be improved: Some users find that emails generated by Access Rights Manager need to be more readable like it shows errors in HTML or RTF formatting.
The SolarWinds Access Rights Manager runs on Windows Server and it is available for a 30-day free trial.
EDITOR'S CHOICE
SolarWinds Access Rights Manager is our top choice because it effectively manages access permissions and reduces security risks. It helps minimize the impact of insider threats by monitoring user activity. By detecting changes swiftly, it ensures compliance with regulations. Access Rights Manager also provides quick insights into who has access to what resources, aiding in efficient security management.
Download: Get 30 days free trial
Official Site: https://www.solarwinds.com/access-rights-manager
OS: Windows Server
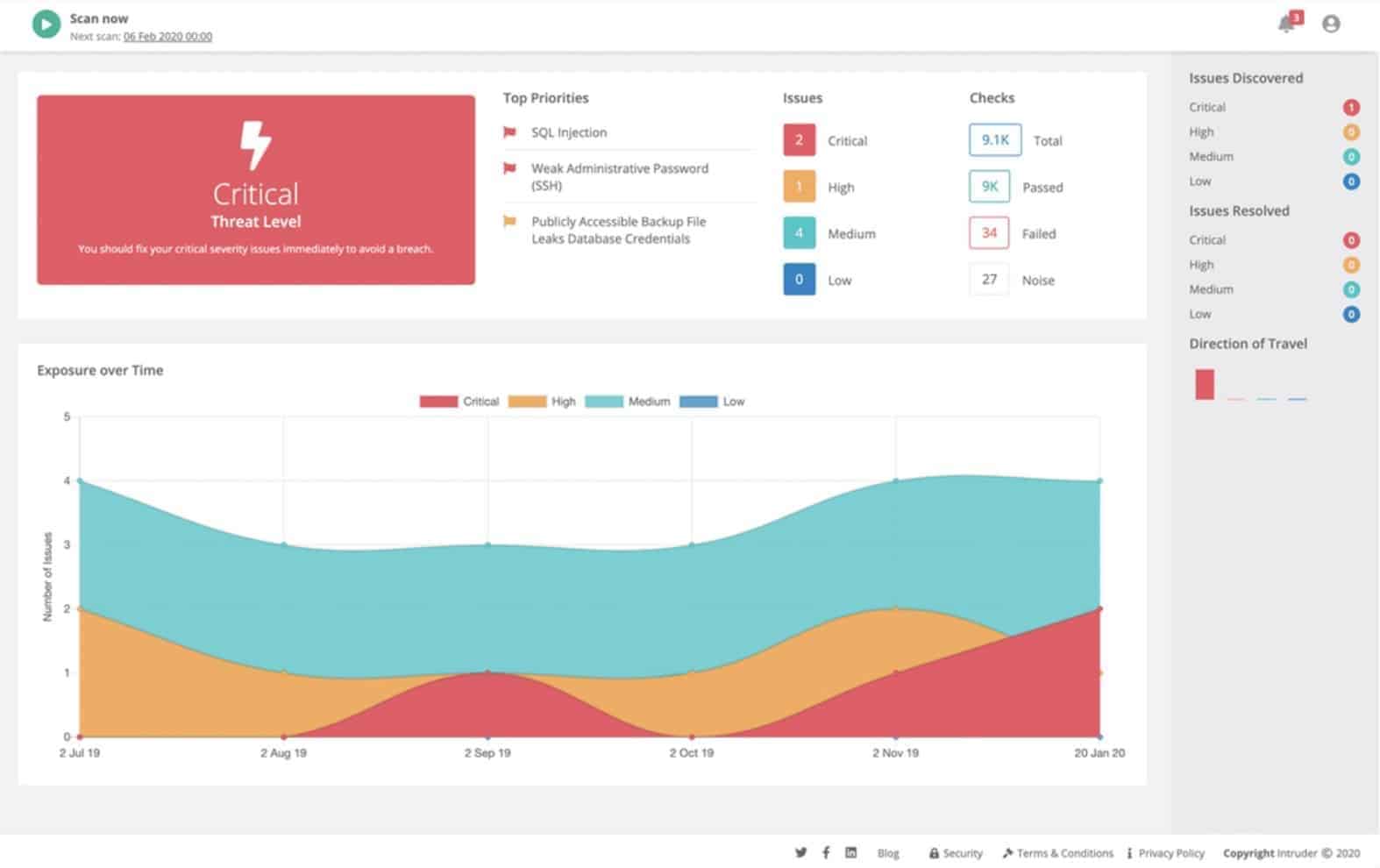
2. Intruder – FREE TRIAL
Intruder is a cloud-based security tool that performs vulnerability checks on a monitored system. On opening an account, each customer gets a total system check, which looks for a list of known vulnerabilities. Thereafter, Intruder will perform a vulnerability scan once a month.
Key Features:
- Continuous Scanning: The intruder conducts continuous scanning of networks, triggering vulnerability assessments whenever there is a change or emerging threat.
- Cloud-Based Operation: As a cloud-based platform, it simplifies deployment and management while offering scalability and flexibility to adapt to varying workload demands.
- Comprehensive Vulnerability Assessment: The tool checks for vulnerabilities across various aspects of IT infrastructure, including web applications, databases, and operating systems.
- Actionable Insights: you can optimize your resources with the help of actionable insights prioritized by context and critical vulnerabilities first.
Why do we recommend it?
We recommend Intruder because it's a cloud-based platform for scanning and managing vulnerabilities. It offers external scans to find security gaps hackers might exploit and internal network scans to detect misconfigurations and software weaknesses. This helps prevent unauthorized access to keep the network secure from potential threats.
Scans are launched from an external location and from within the network, through an agent program. In total, a typical scan looks for 140,000 vulnerabilities.
Who is it recommended for?
The intruder is recommended for network administrators and cybersecurity experts. These professionals use the tool to continuously monitor their networks for vulnerabilities, conducting scans triggered by changes or emerging threats. Intruder provides real-time insights into the attack surface, combining network monitoring, automated scanning, and proactive threat response to prioritize and address vulnerabilities effectively.
Pros:
- Comprehensive scanning: it scans all new devices for vulnerabilities and recommends patches for outdated machines.
- Cloud-based operation: Its cloud-based nature eliminates the need for on-premise servers, simplifying deployment and management.
- Versatile vulnerability assessment: It helps assess vulnerabilities in web applications, databases, and operating systems for comprehensive security testing.
- Flexible pricing: With three-tiered pricing, you can easily access this tool, which is suitable for businesses of all sizes.
Cons:
- Limited report detail: Some users find reports could contain more detailed information, potentially impacting the depth of analysis and actionable insights provided by the tool.
There are three plans for Intruder’s services and all are charged for by subscription. These plans are called Essential, Pro, and Vanguard. The Essential plan gets the automated monthly scan. The Pro version allows users to launch scans on-demand whenever they want as well as provide the scheduled monthly system sweep. The Vanguard also includes the services of a human team of penetration testers.
Intruder is available on a 14-day free trial.
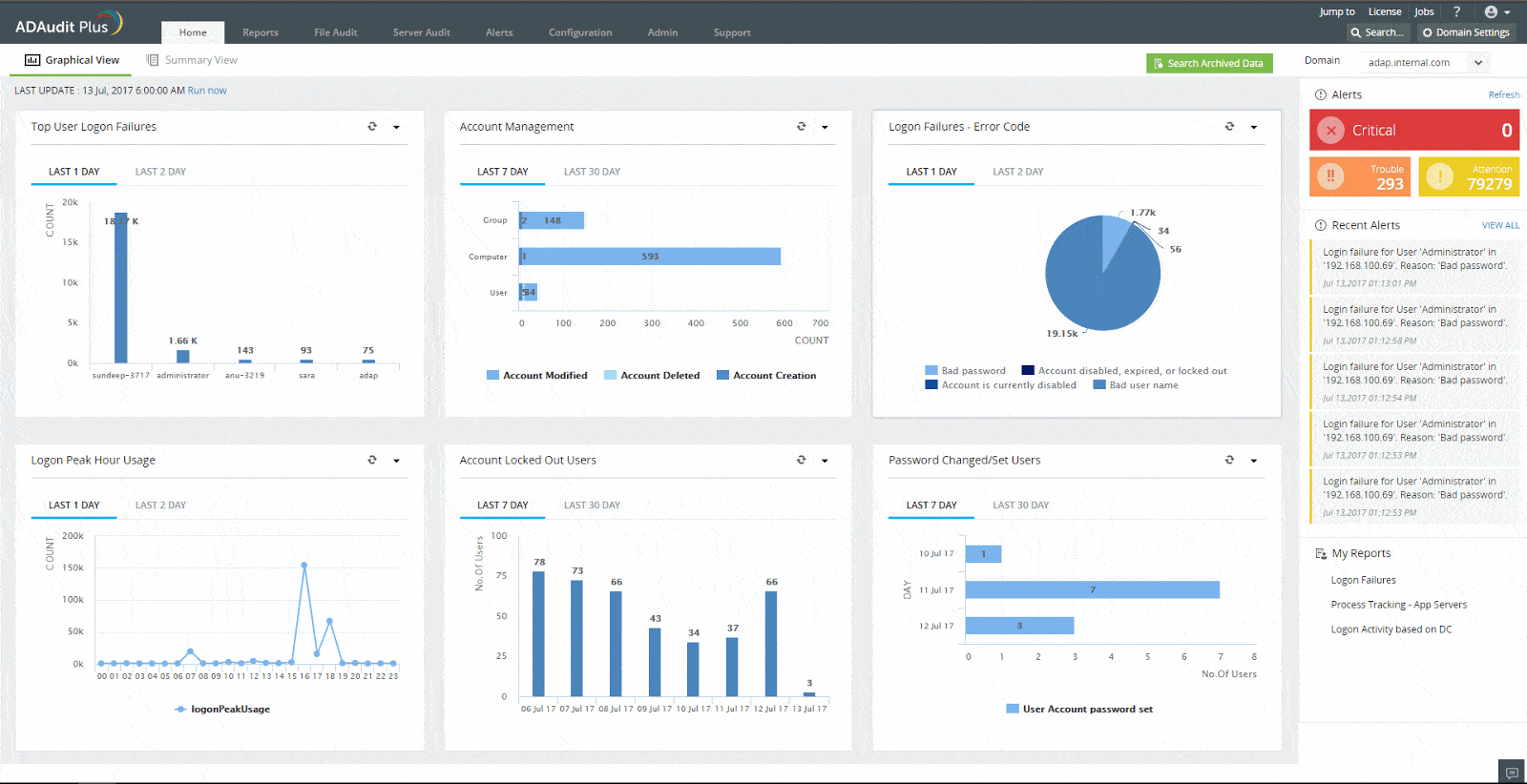
3. ManageEngine ADAudit Plus – FREE TRIAL
ManageEngine ADAudit Plus is a specialized auditing system for access rights management issues. This ManageEngine software package assists towards compliance reporting for a number of data security standards, such as GDPR, HIPAA, and PCI DSS.
Key Features:
- File Change Tracking: This feature helps organizations maintain a comprehensive audit trail of file activity for security and compliance purposes.
- Permission Monitoring: The tool monitors folder owner and permission changes, offering insights into modifications made to file access rights. It also provides before and after values of permissions, enabling administrators to detect unauthorized access and ensure data security.
- Real-time Alerts: ADAudit Plus offers real-time alerts for critical events such as unauthorized file access attempts or changes to sensitive permissions.
- User and Entity Behavior Analytics (UEBA): ADAudit Plus leverages UEBA capabilities to detect anomalous behavior patterns, such as unusual file access or permission changes.
Why do we recommend it?
We recommend ManageEngine ADAudit Plus for its User and Entity Behavior Analytics (UBA) driven change auditing capabilities. It ensures Windows Server ecosystem security and compliance by offering complete visibility into all activities. With accurate records of Azure AD user logon activity, it identifies successful, failed, and suspicious sign-in attempts and examines changes made across various aspects of Azure AD.
The main purpose of this tool is to log all security-related events that occur on the network with respect to user accounts and resource access. It tracks logon failures, changes to user accounts and resource permissions, and alterations to the settings of Active Directory instances. It monitors AD implementations for SharePoint and Exchange Server as well as Windows user accounts systems.
As well as generating log files for auditing use, this service protects those files from tampering. It also monitors and protects the permissions of the folders that contain AD audit log files. These measures, together with the monitoring of accounts and settings within AD, block attempts by intruders to hide their presence.
The ADAudit Plus system includes logfile management services that create archives of older directories. These archives can be stored for up to three years and it is possible to bring them back to current availability in the event that they are needed for an external standards compliance audit. The system also includes report formats and query templates that are tailored to a range of network security auditing requirements, including those needed for standards compliance reporting.
Who is it recommended for?
ManageEngine ADAudit Plus is recommended for IT administrators and cybersecurity experts who need to monitor and track file changes and permission modifications within their organization's network. These professionals rely on the tool to provide detailed insights into file modifications, failed attempts, and changes in folder ownership and permissions for enhanced security and compliance.
Pros:
- Activity Reporting: ADAudit Plus offers comprehensive reporting on user activity, providing valuable insights into file access, permission changes, and other critical events.
- Alerting on Anomalies: The tool generates alerts for anomalies and unexpected events, enabling administrators to respond to potential security threats promptly.
- Ease of Deployment: ADAudit Plus is known for its ease of deployment and configuration, simplifying the setup process for administrators.
- Excellent End User Support: The platform provides excellent support services, assisting users with any questions or issues they encounter during deployment or operation.
Cons:
- Difficulty in Writing Custom Alerts: Some users may need help to write or configure custom alerts, requiring a deeper understanding of the tool's capabilities and syntax.
ManageEngine ADAudit Plus installs on Windows and is available in four editions. The lowest of these options is Free – this has limited capabilities. The three full versions are the 30-day Free Trial Edition, which is active for 30 days and then automatically converts to a limited Free Edition, the Standard Edition, and the Professional Edition.
4. Papertrail – FREE TRIAL
Papertrail – from SolarWinds – is a log management service that is particularly useful for those who need to store and archive network security logs for auditing purposes. This system will store log messages from a range of applications and also gather Windows Event logs and Syslog messages. The management of these records is essential for your network security auditing strategy.
Key Features:
- Aggregate Logs: Papertrail aggregates logs from various sources into a centralized platform, providing a comprehensive view of system activity.
- Tail and Search Logs: The tool offers real-time log tailing and intuitive search capabilities. It allows users to monitor logs as they are generated and quickly search through log data to identify relevant information.
- Receive Instant Alerts: Papertrail provides instant alerts for predefined events or custom triggers, notifying users of critical issues or anomalies in log data.
- Analyze Logs: With Papertrail, users can analyze log data to gain insights into system performance, identify trends, and troubleshoot issues effectively.
Why do we recommend it?
We recommend Papertrail because it's user-friendly, easy to implement, and provides instant visibility across all systems within minutes. As part of SolarWinds Cloud, it offers full-stack monitoring capabilities, making it ideal for monitoring cloud-native applications and infrastructures, ensuring efficient and comprehensive monitoring solutions.
Log messages get collected by Papertrail agents, which need to be installed on your servers. These messages are then uploaded to the Papertrail server for processing. The first thing the log manager does with these messages is to convert them into a neutral format so that they can be stored in the same location. This unifying step also makes it possible to search through one source of data when analyzing log messages for signs of a security breach. The Papertrail dashboard includes a viewer that enables you to load in log messages for analysis.
Papertrail includes an archiving mechanism that can revive those files, and bring them back into a live status when required for external audits. This is an essential service for compliance auditing.
Who is it recommended for?
SolarWinds Papertrail is widely used by engineers and IT professionals who need simple yet powerful log management. It supports various log types and offers real-time log tailing, intuitive search, and filter capabilities for troubleshooting. It's designed to simplify the troubleshooting process and reduce Mean Time to Repair (MTTR).
Pros:
- Live View of Logs: Papertrail provides a live view of logs, allowing users to monitor system activity in real-time and respond promptly to events as they occur.
- Filtering and Custom Views: The tool offers robust filtering and custom views, enabling users to tailor log displays to their specific needs and focus on relevant information.
- Historical Information: Papertrail retains historical log data, allowing users to access and analyze past events for troubleshooting, compliance, or trend analysis purposes.
Cons:
- Better JSON Search Support: Some users may find that Papertrail could improve its support for searching and analyzing JSON-formatted log data, enhancing the platform's capabilities for handling structured log information.
The data processing and storage capacity and file availability period are dictated by the plan each customer chooses. The service is charged by subscription with a monthly fee. There are six editions available and the first of these is Free – which has an initial throughput allowance of 16 GB, which is topped up by 50 MB per month. The five paid plans have successively larger data allowances. The top plan includes a throughput allowance of 25 GB per month with a two-week period when data is available for searching and a one-year archive period. All of these limits can be altered on consultation with the sales team to create a custom package. You can register for the free trial.
5. ManageEngine Log360 – FREE TRIAL
ManageEngine Log360 is a log management and SIEM service that runs on-premises. The package includes a central log server that includes the SIEM and a series of endpoint agents. The log manager runs on Windows Server and there are endpoint agents for all major operating systems plus cloud platforms.
Key Features:
- Custom Log Parser: Log360 offers a custom log parser feature, allowing users to parse and interpret log data from diverse sources and formats.
- Support for Multiple Environments: The tool supports multiple environments, including on-premises, cloud, and hybrid setups.
- Over 750 Log Sources: This extensive log source support enables comprehensive monitoring and analysis of IT infrastructure, enhancing visibility into security events and operational activities.
- Integration with Ticketing Tools: it easily integrates with ticketing tools, enabling automated ticket generation for detected security incidents or operational issues.
Why do we recommend it?
We recommend ManageEngine Log360 for its ability to detect database leaks, monitor file shares, and reduce malicious communication to command-and-control (C&C) servers, helping prevent data exfiltration and enhance security. Additionally, its integrated Cloud Access Security Broker (CASB) feature enables control over sensitive data, discovery of shadow apps, and enhanced visibility into cloud activities.
The log manager converts all arriving log messages into a standard format. Log360 displays recently arrived logs in a data viewer that contains tools for analysis and auditing. The system also stores log messages in files.
The log files need to be kept for compliance auditing. You also get compliance reporting that complies with HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA.
Who is it recommended for?
Log360 is recommended for IT professionals and cybersecurity experts who need to address various security challenges, including log management, Active Directory auditing, public cloud log management, and compliance requirements. It's simple and user-friendly interface makes it suitable for a wide range of users seeking comprehensive security solutions.
Pros:
- Ease of Setup and Implementation: Log360 offers a user-friendly interface and straightforward setup process, hence you can easily deploy and start using the tool quickly.
- Comprehensive Log Capture: The platform seamlessly captures logs from across the network and server infrastructure, and gives a holistic view of IT environment activity for effective monitoring and analysis.
- Pre-configured Reports: Users appreciate Log360's pre-configured reports, which eliminate the need for manual log filtering and provide valuable insights into security events and operational activities.
Cons:
- Slow Support Response: Some users have reported slow support response times, with the vendor performing extensive tests and remote sessions.
The SIEM searches through arriving log messages in a process that is enhanced by a threat intelligence feed. This provides information on the latest hacker campaigns that are circulating around the world. If the threat hunter identifies suspicious activity, it posts an alert in the dashboard. Log360 is also able to channel alerts through service desk systems. Start with a 30-day free trial.
6. LogicGate
LogicGate is a governance, risk management, and compliance (GRC) tool. These features are particularly useful for businesses that need to show compliance to a major data security standard. The service can be tailored to suit the requirements of a specific standard, such as GDPR, PCI-DSS, and SOX. A business that operates a network security auditing strategy would benefit from many of the utilities in this service.
Key Features:
- Data Privacy: LogicGate provides tools to manage and ensure data privacy compliance. This feature enables organizations to handle sensitive data and implement data protection measures securely.
- Internal Audit: The platform offers capabilities for internal audit management, allowing organizations to plan, execute, and track audit activities efficiently.
- Third-Party Risk Management: This feature helps improve risk posture, expedite vendor onboarding processes, and ensure compliance with regulatory requirements.
- Cyber Risk Management: LogicGate includes features for managing cyber risks, enabling organizations to identify, assess, and mitigate threats to their information systems and assets.
Why do we recommend it?
We recommend LogicGate for its ability to provide real-time visibility into your risk landscape. It eliminates data silos, enabling collaborative decision-making with data-driven insights, dashboards, and reporting. LogicGate also helps link cyber threats to tangible business outcomes, prioritize remediation, and report critical information to key stakeholders, enhancing cyber risk management and compliance efforts.
You would use LogicGate at several points of your network security auditing workflow. For a start, you should set up a risk framework that charts the aspects of your IT system and business practices that could be vulnerable to attack. You should set up governance guidelines, using the recommendations of LogicGate to create policies. Your auditing strategy then has an ideal to check reality against.
The risk management parts of LogicGate help you search for system vulnerabilities that need to be tightened up. LogicGate will produce IT security audit guidelines for your big internal audit that will keep your network security in a state of readiness for any external standards compliance audit.
Who is it recommended for?
LogicGate is the best option for organizations seeking to enhance their Third-Party Risk Management processes. It is beneficial for risk managers, compliance officers, and vendor management professionals who aim to efficiently measure third-party risk, automate manual processes, and streamline vendor onboarding while ensuring compliance with policies and regulations.
Pros:
- Customer Portal: LogicGate offers a customer portal for secure and auditable data requests by third parties, ensuring transparency and compliance.
- Automated Alerts: The platform provides automated alerts to keep teams informed about compliance issues and breaches, enabling timely responses and risk mitigation.
- Custom Asset Inventories: Sysadmins can build custom asset inventories and apply personalized permissions, enhancing flexibility and control over data management.
Cons:
- Limited Reporting Functionality: LogicGate offers reporting capabilities, but huge organizations may find it limited depending on the requirements.
This service creates a risk framework tailored to your industry and the standards with which you need to comply. LogicGate can also produce IT security audit guidelines, which are useful for a pre-assessment check as well as a tool for those performing the audit itself. LogicGate is a cloud-based service.
7. Splunk Enterprise Security
Splunk Enterprise Security is an add-on package that is available for those who use Splunk Enterprise – the highest edition of the Splunk data analysis system. The security service of Splunk is based on log file collection. It is a SIEM system that checks on events on the network to look for signs of intrusion and data theft. This function also provides a recursive network security auditing service.
Key Features:
- Advanced Threat Detection: it offers advanced threat detection capabilities and uses machine learning and analytics to detect and respond to sophisticated threats.
- Real-dimension Visibility: This visibility enables proactive threat hunting, incident response, and compliance monitoring across the entire environment.
- Automated Response: Splunk Enterprise Security offers automated response capabilities, allowing organizations to orchestrate responses to security incidents and enforce security policies in real time.
- Customizable Dashboards and Reports: This feature facilitates data-driven decision-making, collaboration among security teams, and communication of security insights to stakeholders.
Why do we recommend it?
We recommend Splunk Enterprise Security to tackle tough security and observability challenges. It allows you to stream, collect, and index data of any size, enabling comprehensive analysis. Real-time alerts help you respond quickly to threats. Plus, you can also customize your app with its free pre-built apps according to your business needs.
The log files that Splunk Enterprise Security collects and files are stored so that they can be available for analysis and system auditing at any time. The Splunk system has its own internal auditing function, which keeps the system secure from insider threats.
Both the log collection and management and the internal auditing service of Splunk Enterprise Security are necessary assistants for those businesses that need to prove compliance to a data security standard. This system is a good choice for those who need to prove compliance with PCI DSS, GDPR, HIPAA, FISMA, and ISO/IEC 27001.
Who is it recommended for?
Splunk Enterprise Security is recommended for IT professionals and cybersecurity experts who require visibility into their digital systems. By providing insights into all systems, it enables proactive incident response. With streamlined workflows, Splunk helps detect and respond to threats faster, minimizing business impacts and ensuring customer satisfaction.
Pros:
- Powerful Queries: Splunk Query Language allows highly customizable queries, enabling users to search and analyze data from various sources efficiently.
- Dashboard Abilities: Offers flexibility in building complex panels for dashboards, facilitating the creation of customized visualizations tailored to specific needs.
- Helpful Search Aids: Simplifies the setup of complex custom alerts and aids in threat hunting by providing useful insights, such as user frequency in specific events.
Cons:
- Dashboard Builder: beginner users need help with using the dashboard builder feature. It may require more out-of-the-box panels for beginners to learn and utilize effectively.
Splunk Enterprise installs on Windows or Linux and there is a 60-day free trial available. The service is also available as a SaaS system, called Splunk Cloud and you can try that on a 15-day free trial. Add Splunk Enterprise Security to either of these systems. The add-on is available for a 7-day free trial.
The total package of Splunk Enterprise Security, whether taken as on-premises software or a cloud service, will provide you with immediate security cover plus an audit trail for every type of network security auditing requirement.
8. Netwrix Auditor
Netwrix Auditor is a system-wide auditing utility that highlights vulnerabilities in network resources and other IT infrastructure. It is a particularly useful auditing system for businesses that need to provide compliance to data protection standards. network and servers from intrusion and accidental damage.
Key Features:
- Real-Time Alerting: The platform offers real-time alerting functionality, enabling organizations to receive notifications about critical changes or security incidents as they occur.
- Access Control Monitoring: it provides visibility into user access permissions and ensures proper access controls are maintained.
- Data Restoration and Rollback: The platform allows organizations to restore quickly and roll back changes that could potentially impact security or disrupt operations.
- User Activity Monitoring: It helps monitor user activity and behavior across their IT environment, providing insights into user actions and helping detect insider threats or suspicious behavior.
Why do we recommend it?
We recommend Netwrix Auditor for its robust network device auditing capabilities. It examines access accounts, permission levels, login attempts, and configuration changes, detecting security weaknesses or threats in real-time. Additionally, it logs its findings, ensuring comprehensive security monitoring and compliance adherence.
The Netwrix system has preset configurations for a range of security standards. Just nominate the standards that you need to follow in the settings of the system and all of the auditing functions, procedures, and reports will be reconfigured to comply with those requirements. There are specific adaptations available for GDPR, HIPAA, PCI DSS, SOX, NIST, FERPA, GLBA, FISMA, CJIS, NERC CIP, and ISO/IEC 27001data protection standards.
Among the activities of a Netwrix audit are checks on user account activity and resource access events. The system interfaces with Active Directory well and it is able to manage the backup process for all of your AD instances. This backup is then used as a default that can be restored to the live system if any unauthorized changes are detected in the access rights manager.
Who is it recommended for?
Netwrix Auditor is recommended for IT security professionals and administrators concerned with security and user productivity. It tracks Access Control Lists (ACLs) and critical changes, allowing prompt rollback of modifications to prevent excessive permissions or access removal. Its integrated MMC snap-in facilitates backup and recovery tasks directly from Active Directory Users and Computers (ADUC).
Pros:
- Detailed Auditing and Reporting: it helps in maintaining the chain of custody for sensitive files and ensuring compliance with regulatory requirements.
- Hardware and Device Monitoring: you can track device health alongside security measures and enhance overall infrastructure management.
- Automated Remediation: Allows sysadmins to implement automated remediation through scripts, streamlining response to security incidents and reducing manual effort.
- Integration with Help Desk Platforms: Integrates with popular help desk platforms for automatic ticket creation, facilitating seamless incident management and resolution.
Cons:
- Issues Supporting Cisco Network Devices: users reported that they faced issues in supporting Cisco network devices, which impacted the monitoring and management of network infrastructure.
Netwrix Auditor is a downloadable software package that installs on Window Server. It can also be run as a virtual appliance over Hyper-V and VMWare You can check out Netwrix Auditor on a 20-day free trial.
9. Acunetix
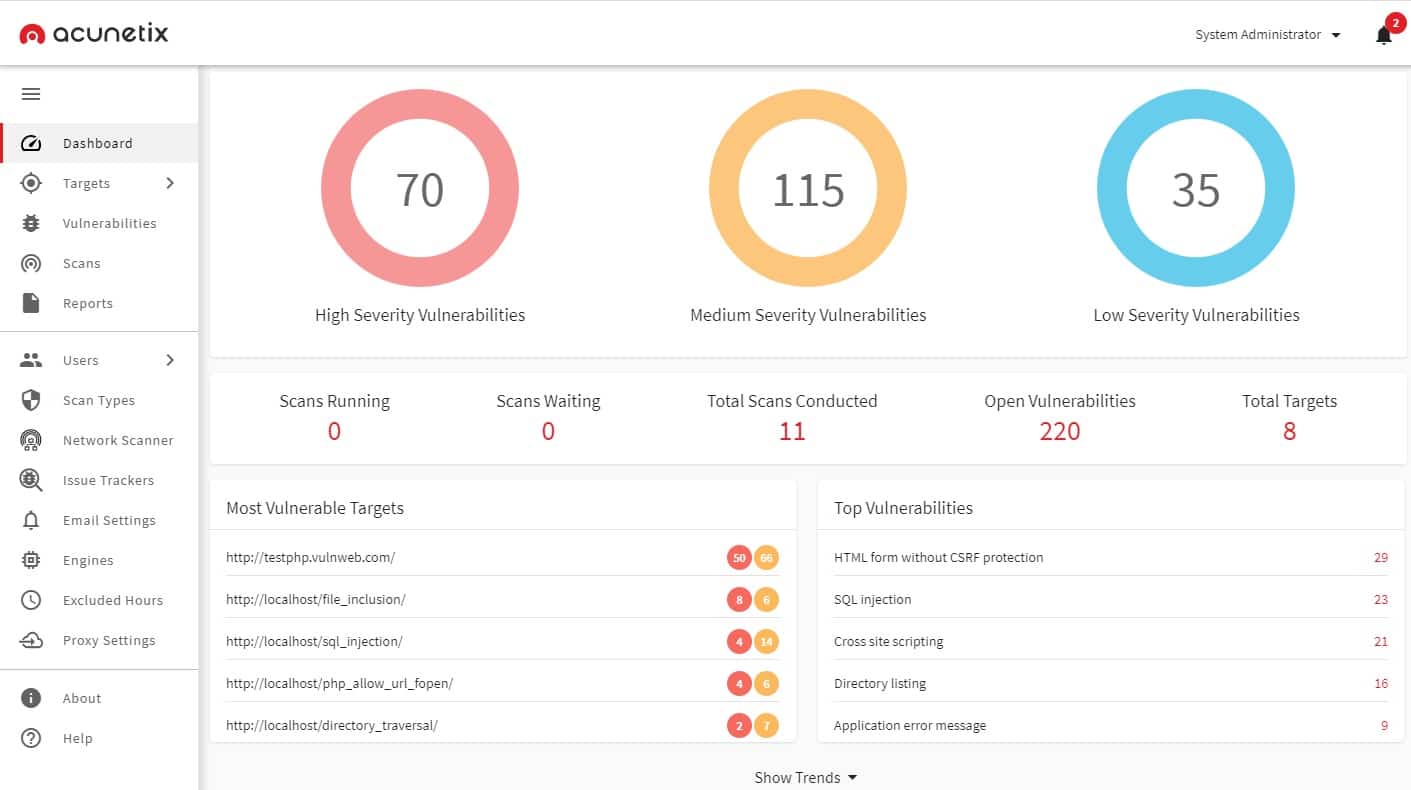
Acunetix is a vulnerability scanner for Web applications. If you operate a website, you need to make sure that it is secure against attack. If you develop websites, then you also need to ensure that vulnerability testing is integrated into your DevOps workflows.
Key Features:
- Tests for 50,000 vulnerabilities: Acunetix is equipped to test for over 50,000 vulnerabilities, ensuring comprehensive coverage of potential security weaknesses in web applications.
- Integrates OpenVAS: OpenVAS is an open-source vulnerability scanner that provides additional scanning functionalities and expands the range of vulnerabilities that Acunetix can detect.
- Interfaces to CI/CD tools: Acunetix offers interfaces to Continuous Integration/Continuous Deployment (CI/CD) tools, allowing for seamless integration into the development pipeline.
Why do we recommend it?
We recommend Acunetix for its versatility as a DevOps tool, capable of identifying vulnerabilities in code during development and serving as a web vulnerability scanner for operations teams. Its dashboard provides detailed OpenVAS scan results, including severity and vulnerability status, enhancing visibility and facilitating effective vulnerability management.
Acunetix monitors a list of 6,500 Web application vulnerabilities. It guards against system corruption and gateways in web applications that can allow hackers to break into your network. This is a form of system auditing for risk prevention.
Who is it recommended for?
Acunetix is recommended for IT professionals and cybersecurity experts dealing with single-page applications, script-heavy sites using JavaScript and HTML5, password-protected areas, complex paths, multi-level forms, and unlinked pages that many scanners may overlook. It's ideal for comprehensive web vulnerability scanning across diverse web environments.
Pros:
- Low Rate of False Positives: Acunetix has a low rate of false positives, minimizing the likelihood of incorrectly identifying benign issues as security vulnerabilities.
- Good Reporting Options: The platform offers robust reporting options, providing detailed insights into vulnerabilities discovered during scans.
- Authenticated Scans: Acunetix supports authenticated scans, allowing for comprehensive testing of web applications with user authentication mechanisms.
- Integration with Different IDEs: Acunetix integrates seamlessly with various Integrated Development Environments (IDEs), facilitating easy incorporation into the development workflow.
Cons:
- User Management: Some users may find the user management aspect of Acunetix to be lacking in features or functionality, potentially posing challenges in user administration and access control.
The Acunetix system is available in three editions. The first of these is Acunetix Standard, which operates tests against live websites. This is a full security auditing service that is an ideal fit for eCommerce operations. The developers of websites would need to pay more attention to Acunetix Premium or the Acunetix 360 edition. These two plans integrate with DevOps project management systems to build vulnerability auditing into the testing and acceptance phases of website development.
The downloadable software package for Acunetix is available for Windows, macOS, and Linux. You can get a demo of the system to assess its suitability for your business.
10. Nessus Vulnerability Scanner
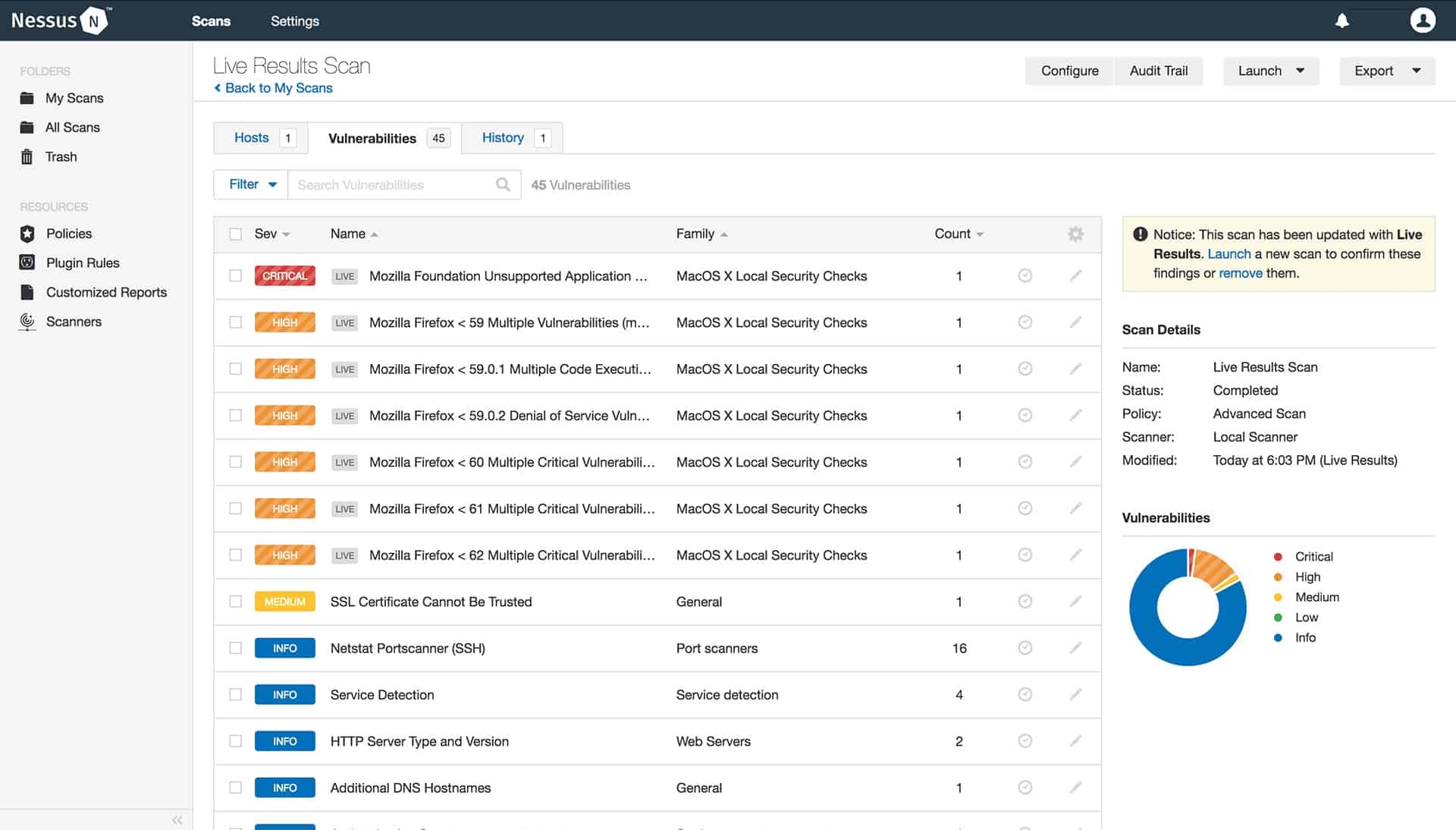
Nessus is a vulnerability scanner that offers network security auditing services by checking for more than 58,000 vulnerabilities on your entire infrastructure, including network settings, service functions, and user-facing applications and software packages. The activities of the system auditor extend to access rights management and user activities.
Key Features:
- Deploy on Any Platform: Nessus can be easily deployed on Windows, Linux, and macOS; it is also compatible with different IT environments.
- Web Application Scanning: This feature helps ensure the security of web-based services and prevents potential exploitation by malicious actors.
- Pre-Built Policies and Templates: These policies cover common security standards and best practices, ensuring comprehensive scanning and compliance adherence.
- Secure Cloud Infrastructure Before Deployment: it allows organizations to check the security of cloud infrastructure before deployment, identifying vulnerabilities and misconfigurations.
Why do we recommend it?
We recommend Nessus because it's trusted by numerous organizations worldwide, with millions of downloads. It identifies vulnerabilities on network devices and endpoints, categorizing them by severity. Nessus generates detailed reports, making it easier to prioritize and address security risks effectively across your network infrastructure.
There are two versions of Nessus. These are Nessus Essentials and Nessus Professional. The Nessus Essential edition is free to use and community-supported. This system is limited to looking at only 16 devices with IP addresses on the network. The Nessus Professional edition performs all of the same services as Nessus Essentials but it has no limit on the size of the network that it will check. Nessus Professional also includes a full, professional support service.
Who is it recommended for?
Nessus is recommended for mid-sized and large organizations seeking comprehensive vulnerability scanning. It's favored by cybersecurity experts who need to identify and prioritize security risks across their network infrastructure. Small businesses can also benefit from Nessus Essentials, which offers free vulnerability scanning capabilities tailored to their needs.
Pros:
- Accurate Vulnerability Scans: Nessus excels at performing vulnerability scans, providing accurate findings and assessments to help organizations identify security weaknesses.
- Multiple Scan Profiles: The platform offers various profiles and policies for different types of scans, including PCI-DSS, malware, web applications, and shell shock detection scans, enhancing flexibility and coverage.
- Risk-Based Vulnerability Classification: Nessus classifies vulnerabilities into risk-based categories, ranging from critical to informational, enabling organizations to prioritize remediation efforts effectively.
- Implementation of Best Practices: Nessus helps organizations implement best practices for vulnerability management, ensuring comprehensive security posture and compliance adherence.
Cons:
- Cost Restrictions: While Nessus offers a free version (Nessus Essentials), it has limitations, such as the inability to perform internal/external PCI scan policies and configuration audits.
Those who prefer to use Cloud services should check out Tenable.io. This is a SaaS version of Nessus Professional. Both versions of Nessus install on Windows, macOS, and Linux. Nessus Professional and Tenable.io are both charged by a fee for a 1, 2, or 3-year license. You can get a 7-day free trial of Nessus Professional or a 30-day free trial of Tenable.io.
Best Network Security Auditing Tools FAQs
What are the types of network security audits?
The types of network security audits include internal audits, external audits, and penetration testing.
What is an internal network security audit?
An internal network security audit is a type of audit that is performed by an organization's own security team to assess the security of its network infrastructure.
What is an external network security audit?
An external network security audit is a type of audit that is performed by a third-party security consultant to assess the security of an organization's network infrastructure.
What is penetration testing?
Penetration testing is a type of network security audit that involves simulating a real-world attack on an organization's network infrastructure to identify vulnerabilities and potential security threats.
What are the benefits of a network security audit?
The benefits of a network security audit include improved network security, reduced risk of security incidents, and better compliance with security regulations and standards.
What are the components of a network security audit?
The components of a network security audit may include vulnerability assessments, penetration testing, security configuration reviews, and log analysis.
What tools are used in a network security audit?
The tools used in a network security audit may include vulnerability scanners, packet sniffers, network analyzers, and penetration testing tools.