Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
The Best Privileged Access Management Tools for 2024

UPDATED: January 10, 2024
Protect the elevated portions of your network infrastructure with these PAM tools.
By employing Privileged Access Management Tools (PAMs) within your network, you can effectively control access to elevated portions of your infrastructure. These products are typically targeted towards larger businesses, where access control can be a concern where you have multiple groups with individual access levels. These systems function by integrating across your network and validating individual user access, limiting privileged accounts to their proper areas, and denying them access to sections they should not be able to access.
Here is our list of the Best Privileged Access Management Tools:
- Heimdal Privileged Access Management One of Heimdal's safe solutions aimed at protecting your network is the PAM solution, which also features integrated zero-trust execution and the de-escalation of user permissions in response to threat detection.
- JumpCloud Directory Platform JumpCloud Directory Platform provides a single cloud-based PAM with smooth integration options with numerous applications, including Active Directory, G Suite, Salesforce, Slack, and hundreds more.
- Delinea Secret Server With Delinea Secret Server's excellent on-premises or cloud-based PAM that is scalable, you can manage accounts for a variety of databases, programs, network devices, and security technologies even in enormous, remote systems.
- BeyondTrust The BeyondTrust Endpoint Privilege Management solution is identical to the other offerings from the firm in that it provides a top-notch PAM system of corporate quality that is integrated throughout your whole network infrastructure.
- Symantec PAM Regardless of your environment, Symantec PAM provides a privileged access control solution that is simple to deploy. To increase security, it aggressively enforces permission requirements, preserves administrative login details, and monitors and tracks privileged user behavior across all IT resources.
- One Identity Safeguard One Identity provides several tools under the “Safeguard” heading, each of which is designed to offer the many capabilities one may assume from a PAM software solution.
- Arcon This enterprise-grade PAM solution provides granular access control, enabling you to build your security infrastructure however you see fit. The system's least-privilege access control, which is implemented across all target platforms, allows only users with designated access to read/write data.
- Visulox A PAM that has been on the market for about 20 years and has a consistent and long-lasting structure that has persisted throughout its lifetime and beyond.
These tools employ several specialized features to achieve their goals, here are some functions you need to be aware of to understand exactly what you’re getting out of the available solutions:
- Integrations
These solutions are useless if they cannot properly integrate with the products you use daily. When choosing the right product for you, make sure that you check the available integrations. This might mean relying on an API to handle the integrations—in these cases, research how well you can arrange for bespoke API access to be created. - Behavioral Analysis
Behavioral analysis systems are tremendously useful for avoiding external risks and work by comparing previous patterns of activity to current patterns of activity, and if there are any significant differences, they flag them as potentially malicious. They can efficiently monitor whether an account has been compromised, which is quite useful in the larger scheme of security problems. - Least privilege enforcement
The Principle Of Least Privilege (POLP) refers to enforcing the lowest degree of user privileges, or clearance level, that permits the user to perform his/her task. Enforcing the least privilege is an important best practice for reducing security risk and minimizing business
Our methodology for selecting Privileged Access Management tool:
We've broken down our analysis for you based on these key criteria:
- Compatibility with existing IT infrastructure, ensuring seamless integration.
- The ability to perform real-time behavioral analysis for enhanced security.
- Enforcement of the Principle Of Least Privilege across all user levels.
- Scalability to accommodate the growing needs of large businesses.
- User interface simplicity and ease of use for administrators and users.
The Best Privileged Access Management Tools
1. Heimdal Privileged Access Management
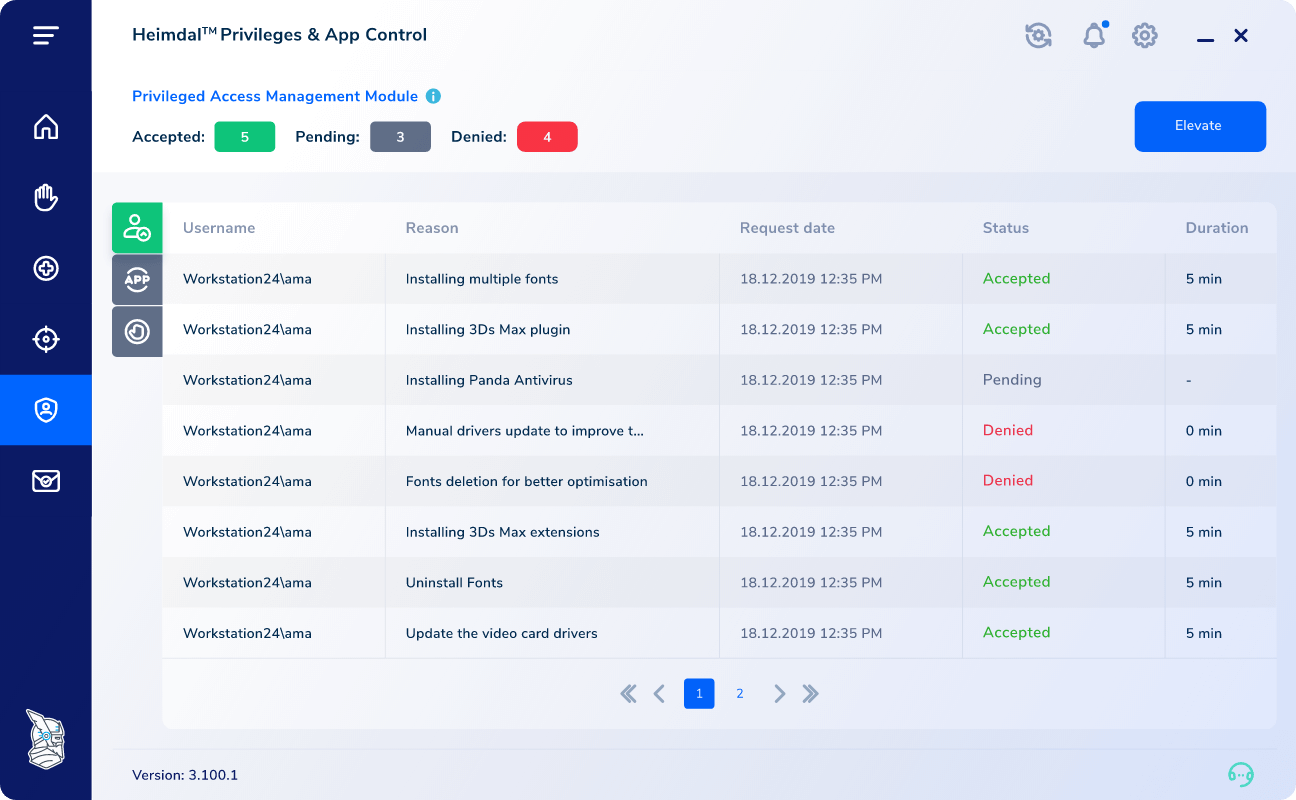
The PAM solution from Heimdal, which also includes integrated zero-trust execution and the de-escalation of user rights in response to threat detection, is one of the security solutions focused on securing your network that Heimdal offers. You have complete control over the user's elevated session with Heimdal's PAM's clean, lightweight UI. You can monitor user sessions, block system file elevation, live-cancel admin access for users, and establish an escalation time.
Key Features:
- Automated security failsafes
- Mobile support client
- Escalation control
- Auditing tools
- Compliance features
Why do we recommend it?
Heimdal Privileged Access Management is recommended for its robust security features, including integrated zero-trust execution and the ability to de-escalate user rights in real time. Its intuitive UI and comprehensive control over elevated user sessions make it a top choice for network security.
Data analytics are incorporated into the system to help with incident investigation and regular security assessments. You may easily obtain reports with a lot of images on subjects like hostname details, the typical escalation time, escalated users or files, files or processes, and more. The system uses a network-wide failsafe to immediately terminate the user session once a threat is discovered on the user's device. You can easily escalate or de-escalate an alerted scenario from your mobile device from anywhere in the world.
The contact page offers a free trial of the software, that includes a full feature demonstration. You must get in touch with Heimdal directly to receive a tailored price quote since the company doesn't provide any pricing information on its website.
Who is it recommended for?
This tool is ideal for organizations looking for an advanced PAM solution with capabilities like session monitoring, automated security failsafes, and escalation control, particularly useful in environments with high-security needs.
Pros:
- Advanced security with zero-trust execution.
- Comprehensive user session control.
- Automated response to threat detection.
- User-friendly interface for easy management.
Cons:
- Pricing information not readily available.
EDITOR'S CHOICE
Heimdal Privileged Access Management is our top Privileged Access Management tool because it offers a comprehensive solution for network security. Its integrated zero-trust execution and capability to de-escalate user rights in response to threats set it apart. The clean, lightweight UI allows for effective control over elevated user sessions, including session monitoring, system file elevation blocking, live admin access cancellation, and escalation timing. The incorporation of data analytics aids in incident investigation and security assessments, enhancing the overall security posture.
Download: Heimdal Privileged Access Management
OS: Windows, Cloud-based
2. JumpCloud Directory Platform
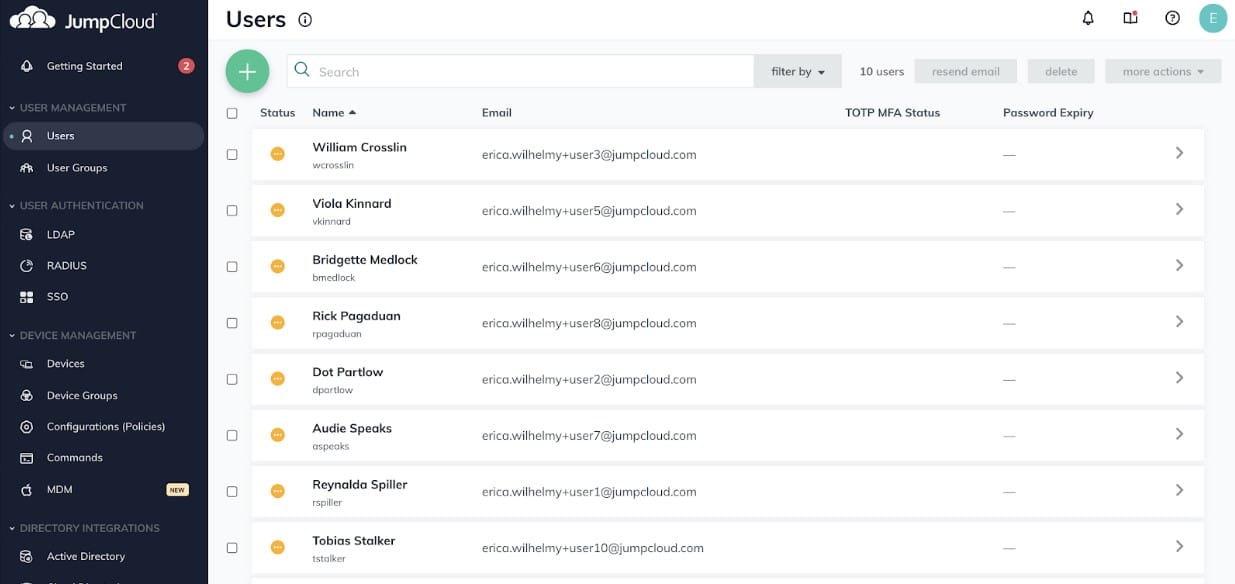
With seamless integration possibilities with several services, including Active Directory, G Suite, Salesforce, Slack, and hundreds more, JumpCloud Directory Platform offers a unified cloud-based PAM. By extending the default authentication to include all IT resources under one overarching system, the platform enables you to connect all devices, applications, servers, and cloud-based infrastructure. You can give end users the option to update their JumpCloud password on their own, either online through their User Portal or instantly from their device, to prevent future phishing attacks.
Key Features:
- Unified Identity & Device management
- Multi-Factor Authentication
- MDM
- Network-wide SSO
- User provisioning control
Why do we recommend it?
JumpCloud Directory Platform is favored for its seamless integration with a wide array of services and its unified cloud-based PAM approach, making it a versatile and efficient choice for modern IT environments.
User identities can be quickly provisioned, unprovisioned, and maintained across your whole integrated network using SAML SSO, Just-in-Time (JIT) provisioning, and SCIM identity management technologies. The solution is created to make it simple to add multi-factor authentication. With the aid of a dedicated admin console, users may be rapidly imported or created. It is also simple to integrate push-based, time-based one-time passwords, hardware keys, biometrics, or other mechanisms to ensure safe access to apps, devices, and other services.
The platform is free for up to 10 people and 10 devices, and it comes with all the premium features that are promoted. This practically amounts to an unlimited free trial of their services. You can sign up and sample JumpCloud for free, or you can arrange a demo to get a detailed explanation of how the platform can meet your company's needs. Beyond those 10 users/devices, the full platform costs $3 per user per month or $24 for a full year.
Who is it recommended for?
It's best suited for businesses that require a comprehensive identity and device management solution, especially those utilizing diverse applications like Active Directory, G Suite, Salesforce, etc.
Pros:
- Integrates with numerous applications.
- Offers Multi-Factor Authentication and MDM.
- Network-wide Single Sign-On and user provisioning.
Cons:
- Limited to 10 users/devices in the free version.
3. Delinea Secret Server
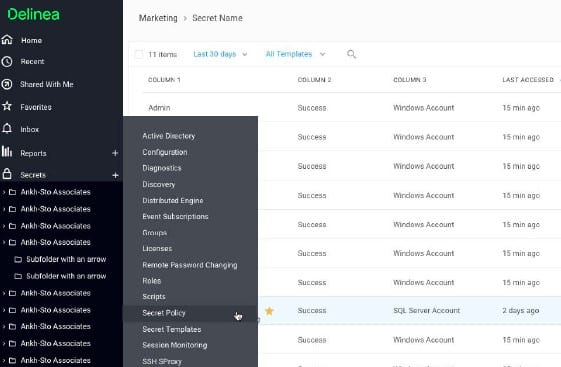
You can manage accounts for a range of databases, programs, network devices, and security technologies even in huge, remote systems thanks to Delinea Secret Server's superior on-premises or cloud-based PAM that is scaleable. The system can also be used to create and change the login credentials for the entire system and to ensure a specified level of password complexity. DevOps process extends protection to development and operational teams while discovering privileged accounts that are unmanaged across your company.
Key Features:
- Privileged credential control
- Behavioral analytics
- Session recording
- Auditing and reporting tools
- Wizard-based installation
Why do we recommend it?
Delinea Secret Server's scalable, on-premises or cloud-based PAM solution is highly effective in managing accounts across diverse databases and systems, making it an excellent choice for large, remote systems.
Installation and integration are made simple to comprehend by wizard-based configuration and deployment processes, and you may modify Secret Server to precisely suit your requirements by using available scripts and APIs. SIEM and vulnerability scanner integration provide incident response visibility, and machine learning combined with behavioral analysis is utilized to identify odd user behavior. Real-time session management includes security features including keystroke logging, monitoring, proxying, and session recording.
You can join up for a 30-day free trial of Delinea Secret Server on the website by providing information about your company. The complete product is offered in two bundles; the Professional edition includes several basic capabilities that may be expanded upon by purchasing additional features separately. The Platinum package is ideal if you require a comprehensive, powerful package because it combines nearly all extra features and standard capabilities in one bundle. Regardless of the solution you choose, you must speak with Delinea directly to receive a personalized price quote.
Who is it recommended for?
Ideal for large enterprises needing robust privileged credential control, session recording, and extensive auditing and reporting capabilities.
Pros:
- Comprehensive privileged credential management.
- Effective behavioral analytics and session recording.
- Integration with SIEM and vulnerability scanners.
Cons:
- Complex configuration may be challenging for some users.
4. BeyondTrust
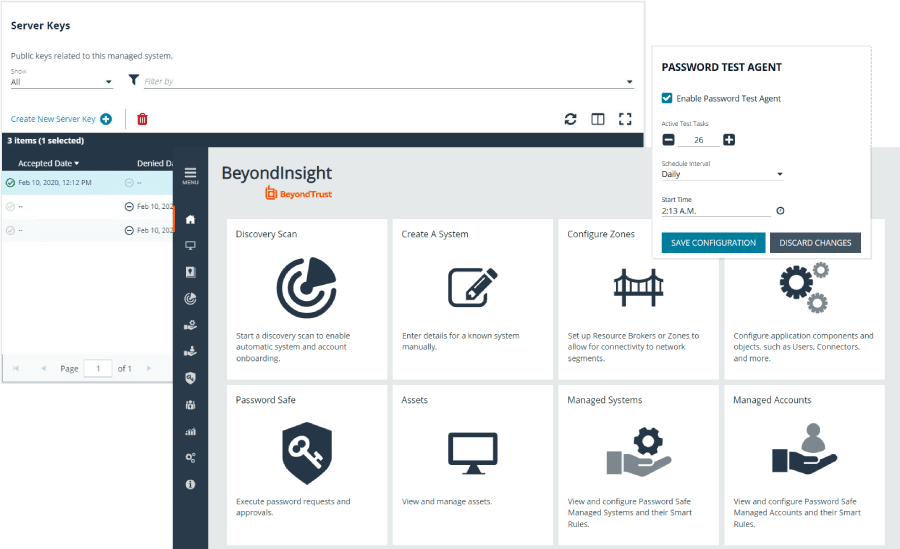
The Endpoint Privilege Management solution from BeyondTrust is no different from the company's other solutions in that it offers a top-notch enterprise-quality PAM system that is integrated throughout your complete network infrastructure. The system offers trusted interfaces with full insight and access control for SIEM products, vulnerability management scanners, and respected help desk software solutions.
Key Features:
- Least privilege enforcement
- Fine-grain policy controls
- Broad integrations
- Audit trails
- Behavioral analytics
Why do we recommend it?
BeyondTrust stands out for its enterprise-quality PAM system, offering extensive policy controls and broad integrations, ideal for organizations seeking a sophisticated access management solution.
With the aid of BeyondTrust, you can obtain a thorough audit record of every user action and compare user analytics to security data, both of which can be crucial in accelerating forensics and, ultimately, greatly simplifying compliance. BeyondTrust excels in applying fine-grained policy-based controls to Windows or Mac apps to provide regular users the access they need to complete a task, eventually preventing malware dangers brought on by overly privileged access.
On the BeyondTrust website, you can submit a price request to get customized pricing. They also offer the ability to set up a one-on-one demonstration of the solution during which you may ask pointed questions to have a thorough understanding of the product's salient features and setup requirements.
Who is it recommended for?
Best for large enterprises looking for detailed audit trails, behavioral analytics, and fine-grain policy controls in their PAM system.
Pros:
- Extensive policy-based controls for apps.
- Detailed audit records and user analytics.
- Enhanced malware threat prevention.
Cons:
- Custom pricing requires direct contact.
5. Symantec PAM
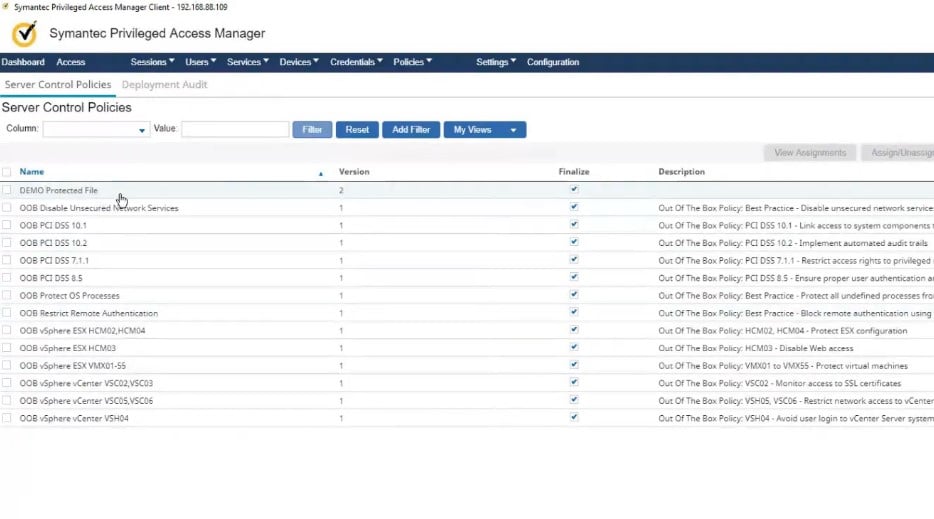
Symantec PAM offers an easy-to-deploy solution for privileged access control in physical, virtual, and cloud environments. It monitors and logs privileged user activity across all IT resources to improve security, safeguards administrative login information, limits privileged access, and actively enforces authorization rules. Once verified, Symantec PAM adopts a zero-trust policy and by default bars all users from accessing any privileged credentials or accounts. The system may additionally record videos of all privileged user activity to strengthen accountability and provide forensic evidence of harmful behavior.
Key Features:
- Automated Mitigation
- Least privilege enforcement
- Password storing
- Session recording
- Behavioral analytics
Why do we recommend it?
Symantec PAM is notable for its easy deployment and comprehensive privileged access control across various environments, making it a reliable choice for diverse IT landscapes.
The system may store passwords and other sensitive data in an internal database that is secure against viruses and hostile threats, such as SSH keys or AWS credentials. Additionally, Threat Analytics can be set up to assist companies in identifying and preventing privileged user account breaches by routinely analyzing behavior using cutting-edge algorithms and machine learning to match the behaviors of the current user with those of the account's previous users.
Similar to other Broadcom goods, you will need to get in touch with the business to get a personalized price or buy a license from one of the many accessible business partners. As a hardened appliance, rack mount device, open virtual appliance, Amazon Machine Instance, or Azure Virtual Hard Disk appliance, the product can be included in your network.
Who is it recommended for?
Suitable for organizations needing robust privileged access control with features like session recording and automated mitigation in physical, virtual, and cloud environments.
Pros:
- Easy to deploy across multiple environments.
- Advanced behavioral analytics and session recording.
- Effective password storage and threat analytics.
Cons:
- Interface may seem dated compared to newer solutions.
6. One Identity Safeguard
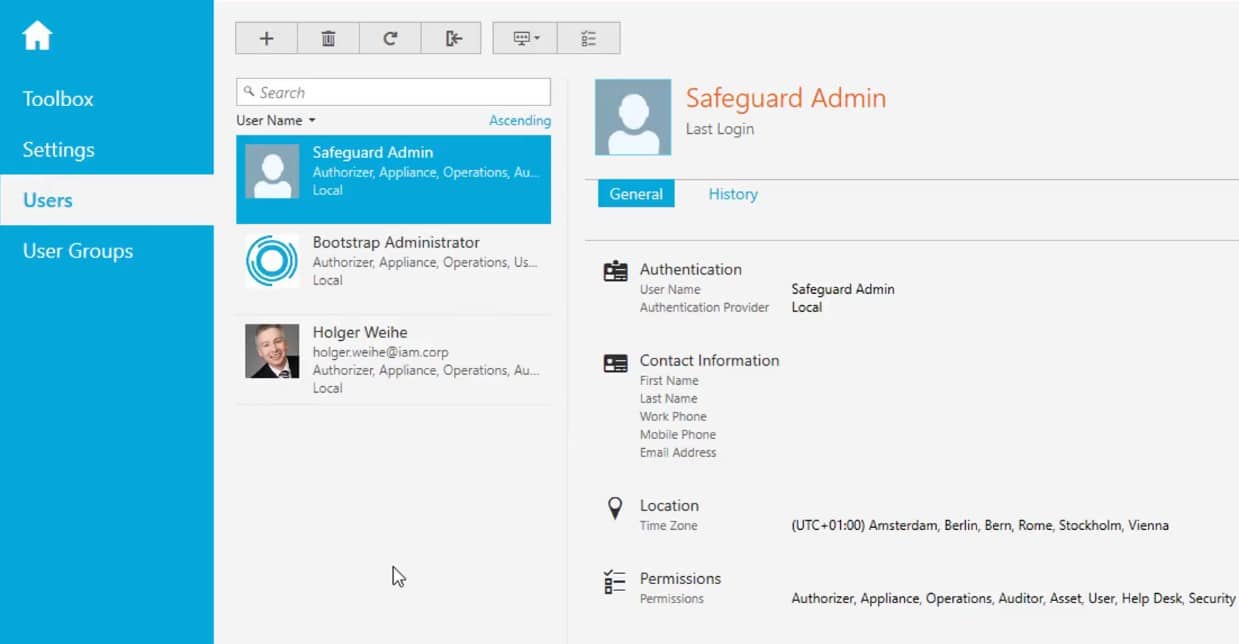
Under the umbrella of “Safeguard,” One Identity offers a collection of tools, each of which is built to provide the many features one may anticipate from a PAM software solution. With the aid of Safeguard for Privileged Sessions, you may control, monitor, and record the privileged sessions of administrators, remote vendors, and other high-risk users. The system evaluates protocol traffic at the application level in addition to serving as a proxy, and it can reject any communication that doesn't adhere to the rules.
Key Features:
- Password control
- Behavioral analytics
- Session recording
- Authentication services
- REST API
Why do we recommend it?
One Identity Safeguard offers a comprehensive set of PAM tools, providing robust session recording, behavioral analytics, and password control, ideal for diverse security requirements.
Safeguard for Privileged Passwords automates, controls, and secures the process of issuing privileged credentials through role-based access management and automated procedures. The solution features a comprehensive REST API for the most integration potential, allowing you to authorize password requests from any location.
Safeguard for Privileged Analytics involves monitoring suspicious activity and identifying dangerous threats that could be originating from both inside and outside of your organization. When these separate systems are merged, they offer the behavior analytics, session recording, and password management you might anticipate from a unified solution.
One Identity offers a 30-day virtual trial that is only accessible through their online platform but may help figure out the precise usability of each Safeguard suite component. You must get an estimate from One Identity's sales department to get the entire price; be sure to specify exactly which Safeguard suite components you are considering. You are given an additional level of customizability not provided by many other PAM solutions thanks to this breakdown of the components.
Who is it recommended for?
Recommended for organizations seeking a versatile PAM solution with advanced analytics and comprehensive session monitoring capabilities.
Pros:
- Comprehensive session recording and monitoring.
- Advanced behavioral analytics for threat detection.
- REST API for extensive integration potential.
Cons:
- Requires contacting sales for complete pricing.
7. Arcon
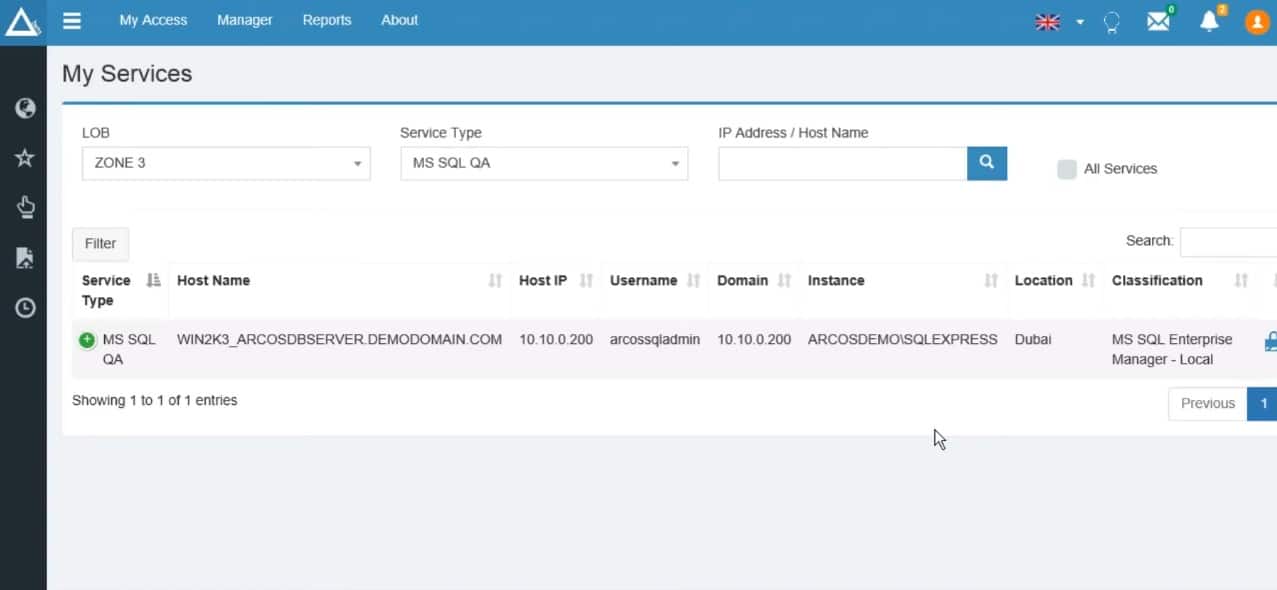
Granular access control is offered by this enterprise-grade PAM system, allowing you to configure your security infrastructure in any way you see fit. Only individuals with designated access are permitted to read/write data thanks to the system's least-privilege access control, which is implemented across all target platforms. SSO helps connect to a certain class of systems without requiring login information, while the virtual grouping functionality allows you to dynamically combine numerous systems into functional groupings. Through a single pane of glass interface, session monitoring provides a basic audit and real-time monitoring for all privileged actions.
Key Features:
- Granular access control
- Cloud or on-premises
- Session recording
- Password generation
- SSO and temp access
Why do we recommend it?
Arcon's enterprise-grade PAM solution is recommended for its granular access control and versatility in both cloud and on-premises environments, suitable for customized security infrastructures.
You may develop a unified access control and governance architecture to keep track of privileged identities, regardless of where they are located—on-premises, in the cloud, dispersed throughout a distributed data center, or in a hybrid environment. To eliminate problems with shared credentials, the system also offers the capability to automatically generate random passwords.
Arcon offers a SaaS business model with customized pricing based on precise company needs that may be ascertained upon request. Although a demo of the system can be requested to view it in use, the solution does not offer a free trial.
Who is it recommended for?
Best for large enterprises needing detailed access control and session monitoring capabilities across various platforms.
Pros:
- Detailed granular access control.
- Flexible deployment options (cloud or on-premises).
- Comprehensive session recording and monitoring.
Cons:
- Custom pricing models require direct inquiry.
8. Visulox
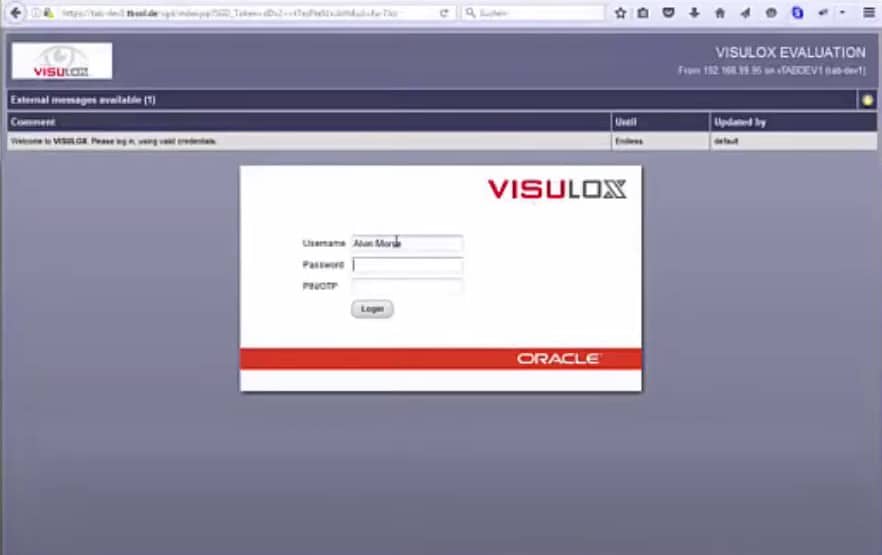
With a steady and durable structure that has lasted throughout its lifetime and beyond, Visulox is an industry-standard PAM that has been available on the market for almost 20 years. Even if the solution shows some traces of its age, particularly in the interface and general presentation, it competes with contemporary systems only because of its simple yet powerful features. Visulox allows you to view and document an application's output, giving you a complete picture of all system activity.
Key Features:
- Classic PAM solution
- Application data access
- Session recording
- Multi-factor authentication
- Host control
Why do we recommend it?
Visulox's long-standing presence in the market is a testament to its reliability, offering a classic PAM solution with robust session recording and multi-factor authentication.
Any program that can be accessed over a network and uses the widely used presentation protocols RDP, SSH, X11, Siemens S5, S7, Telnet, and 3270 can communicate with the platform without the need for extra software components. Visulox offers a wide range of functions, such as fully validated data transfer, and role-based access to several programs, including those that are running under Windows, Linux, or other OT components that can be accessible by TCP/IP. The system allows for the tracking of each access request's author and the time it was made for each application.
Although there is no free trial period, Visulox may provide pricing upon request, and you can ask for a demonstration of the features. Although it is more of a small annoyance, keep in mind that a significant portion of the website is in German but that it is still possible to translate it using tools like Google's built-in translator when researching the products.
Who is it recommended for?
Ideal for organizations looking for a stable and proven PAM solution with essential features like application data access and host control.
Pros:
- Proven reliability over two decades.
- Essential session recording and MFA features.
- Effective application data access and control.
Cons:
- Interface may appear outdated compared to newer systems.



