Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
Domain Password Policy – How To Configure & Setup!
UPDATED: February 6, 2023
Having strong passwords in an Active Directory (AD) network ensures that hackers can’t crack user’s passwords with methods such as brute-force dictionary attacks.
By default, in an Active Directory domain, users will be required to change the password every 42 days, and they will not be able to use the same old password, at least for some time.
Their password would also need to be seven characters or more, and contain a combination of characters, such as numbers, uppercase, lowercase, and non-alphanumerics.
These password settings are good as a starting point, but they might not align with the requirements of your Active Directory organization.
In this post, we’ll learn how to configure and set up an Active Directory domain password policy.
What is the Default Domain Password Policy
The Active Directory domain comes with the “Default Domain Password Policy,” which helps to improve security through password hardening.
The policy is intended to enforce passwords to have enough complexity, to be longer than usual, and to expire after some time.
This policy works great with other policies like the “lockout policy,” which lets you prevent brute force attacks by limiting the allowed number of incorrect logons.
To view and edit the requirements of passwords in the Active Directory Domain, you must use the Group Policy Object (GPO) Settings.
How to View the current Domain Password Policy
Password policies are associated with the root domain and are configured through a group policy. To view the current AD domain password policy, follow the next steps:
- Open the Group Policy Management console using the “gpmc.msc” command.
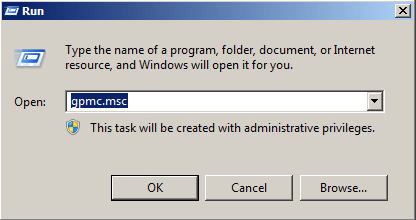
- The domain password policy is under Group Policy Objects (GPO).
Browse through the right-hand window pane, expand your Domains, and then open the Group Policy Objects.
Find the GPO with the name “Default Domain Policy,” right-click it, and select Edit.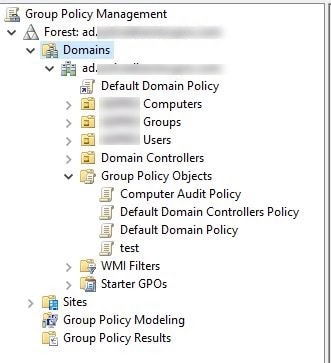
- The Group Policy Management Editor will let you view and configure the password requirements.
Find the “Password Policy” node, which is under the
Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Password Policy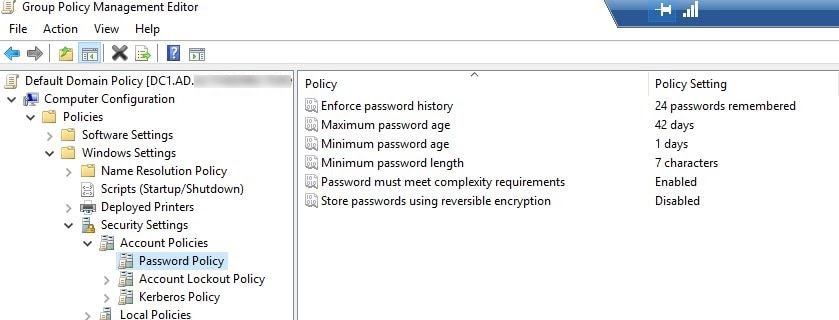
- The Password Policy node that is shown here has the default configuration, which is:
- Enforce password history: Remember the last 24 passwords.
- Maximum password age: Expire after 42 days.
- Minimum password age: One day.
- Minimum password length: Seven Characters.
- Password must meet complexity requirements.
- Do not store passwords using reversible encryption.
5. There is another way to get the default password policy for the Active Directory domain using the Powershell, command-line shell. Open the Windows PowerShell command line as an administrator.
6. Enter the command: [Get-ADDefaultDomainPasswordPolicy]. The command output will show you the current Password Policy along with the Lockout Policy settings.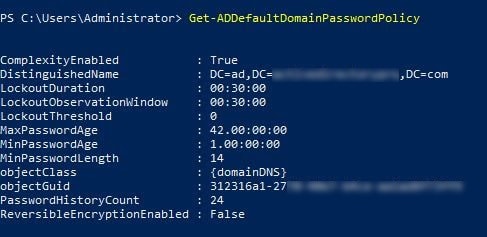
The Password Policy Settings
There are six different password policies that you can configure.
1. Enforce Password History
The “Enforce Password History” specifies the number of previous passwords stored in Active Directory.
The setting enforces users to create unique and new passwords by preventing them from reusing old passwords too often.
The default value of this setting is 24, which means that the user won’t be able to use the current password only after 24 new passwords have already been used.
2. Maximum Password Age
The “Maximum Password Age” defines the number of days that a password can be used before it needs to be renewed.
It gives the password, an expiration date.
Once the password has reached its maximum password age, the system will request a password change.
3. Minimum Password Age
The “Minimum Password Age” determines the period in days that the password should be used before users need to change it.
This setting helps the “Enforce Password History” by denying users to change passwords too often and quickly, to get back to an old password.
It is good to configure this value but keep it to a minimum, in case the password gets compromised. The default value is one day.
4. Minimum Password Length
The Minimum Password Length determines the number of characters in the password.
The default for this setting is seven, which means that all passwords will have to be created with at least seven characters.
Be careful! If you set this policy with a value of zero, the password will not even be required.
5. Password Must Meet Complexity Requirements
You can only Enable or Disable this setting.
When you enable it, you’ll require users to create complex passwords based on certain guidelines. This setting is enabled by default.
The Requirements Are:
- Users can’t use the account name or name of the user anywhere on the password. It is not allowed to use two characters of the name in a row.
- Users must include three different types of characters from any of the numbers (0–9), uppercase and lowercase letters, and non-alphabetic characters (@, $, &, #).
- The password must be at least six characters in length.
6. Store Passwords Using Reversible Encryption
Active Directory encrypts passwords and stores them in the database.
Usually, the encrypted passwords can’t be reversed to “plain-text.” But in some cases, users will need to use their passwords with certain apps to gain access to the domain.
Most likely, the app won’t be able to decrypt the password, so you’ll need to enable the Reversible Encryption.
It is not recommended to enable this setting unless there is a specific need for the application. If you need to enable it, do it on a per-user basis.
Password Policy Setting Recommendations
Setting the password policy depends on the type of organization and applications that you are running.
Your settings can also be guided by requirements from compliance regulations such as PCI-DSS, HIPAA, SOX, NIST, and more.
A good starting point is the very same recommendations from Active Directory developers, Microsoft.
The following is a password policy setting recommendation by Microsoft’s Best Practices for Threat Protection.
- Enforce Password History:
Set it to the maximum, which is 24. Avoid password reuse at all costs. - Maximum password age:
Set it between 60 and 90 days. Microsoft recommends expiring passwords between major business cycles. - Minimum password age:
Set this value to 1 day. Microsoft recommends to not set this to 0, because it would allow immediate password changes. Users can change the password 24 times the same day and get back to the old password. - Minimum password length:
Microsoft recommends setting this value to at least 8. Eight is a good number to keep the password complex, and at the same time, it is not too long so that users would forget it. - Password must meet complexity:
Set it to Enabled. This setting, when combined with the minimum of eight characters required, will guarantee an impossible-to-guess password. - Store passwords using reversible encryption:
Set to disabled. Enable it only if you are using authentication services such as CHAP through remote access.
Configuring a Domain Password Policy
An Active Directory root domain can only have one password policy applied.
When you configure the Default Password Policy, it affects all the computers within that domain.
But if you have a group within the same domain that you want to apply a different set of password requirements, you can use the AD DS fine-grained password policies.
Although you could create a new GPO within the same domain, apply it with a different password setting, and assign it to a specific Organizational Unit (OU), the settings of the new policy will be ignored.
To change the domain password policy, you need to go back to the GPO “Default Domain Policy.” We already mentioned how to access and edit this policy, here is a summary.
- Open the Group Policy Management > Domains > “You Domain” > Group Policy Objects
- Right-click on the “Default Domain Policy,” GPO and click “Edit”. The Group Policy Management Editor will open.
- Go to Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Password Policy.
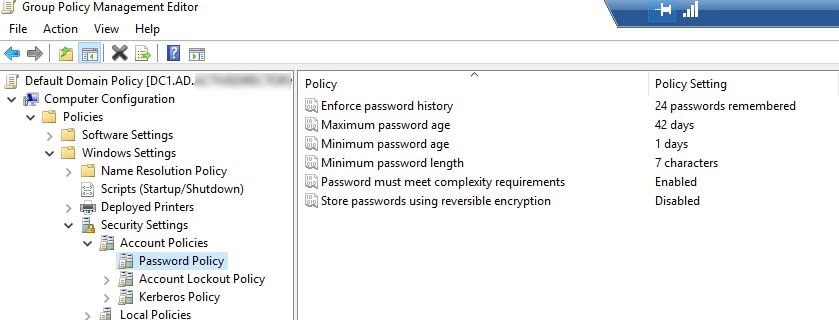
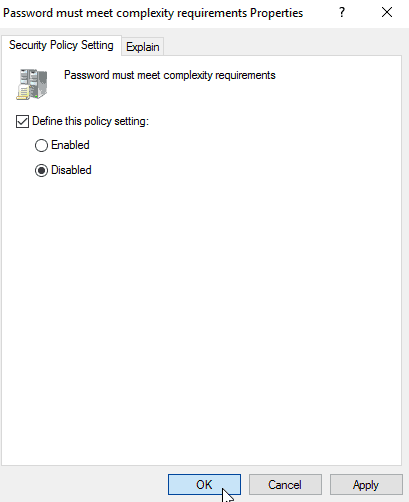
- To edit a policy, double-click on any of the settings. For example, if we want to disable the setting “Password must meet complexity requirements,” double-click on this setting and change your preferred settings, click “Apply”, and then “Ok”.
Other Password Setting Best Practices
Following the Windows guidelines is a great idea, but you can also use other settings outside the domain password policy. For example, the Domain Password Policy works better with the email notifications, account lockout policy, password audits, strong admin passwords, and other third-party tools.
- Email Notifications These can serve as alerts to warn the users when the password is about to expire. Email notifications can help users know when it is time to change their passwords before they expire.
- Account Lockout Policy Lockout policies go hand in hand with passwords. The lockout policy prevents intruders from gaining access to the network using brute-force attacks or dictionaries. If the attacker guesses the username (which most of the time is easy to guess), then the attacker can try many combinations of passwords. The lockout will limit the number of incorrect logon attempts.
- Password Audits In some cases, to avoid attacks from large password dictionaries, it is recommended to perform regular audits on the passwords.
- Admin Passwords The admin sets the password policy, but who sets the password policy for the admin? Although it is vital to have strong user account policies, it is also a good idea to have a strong Administrator password. These are passwords should be changed at least every six months.
- Use third-party tools An auditing tool such as SolarWinds Server & Application Monitor (SAM), allows you to monitor logons and other events. With SAM you can see the number of failed logon events, the password reset attempts, deleted accounts, users created, and a lot more. You can try a full version of SAM for free for 30 days.
- Another third-party tool to look into for password policy enforcement is ManageEngine ADSelfService Plus. This package is available for Windows Server plus the Azure and AWS platforms. It interfaces with all AD instances, creating a single sign-on environment, and will facilitate the creation and enforcement of a password complexity policy. This service also enables the use of multi-factor authentication. Get a look at this tool with a 30-day free trial.

Final Words
Users are usually the easiest target within a domain network.
The account username and password might be the only security measures protecting their computers.
The username might be easy to guess, but passwords shouldn’t be acceptable to be weak.
They should be complex and difficult to guess.
By default, the Default Password Policy is already configured to protect users from creating easy passwords within an AD domain.
But in some cases, due to regulations or the use of applications, you might be required to adjust this password policy.
If you are going to change the password policy settings, always keep in mind the best practices and recommendations!
Configure Domain Password Policy FAQs
How often should a domain password policy be reviewed and updated?
A domain password policy should be reviewed and updated regularly to ensure that it remains effective and meets changing security needs.
What are the consequences of not having a domain password policy in place?
Not having a domain password policy in place can increase the risk of unauthorized access, data breaches, and other security incidents.
How is a domain password policy enforced?
A domain password policy is enforced by the domain controller, which checks and enforces the policy for all users within the domain.
What are the components of a domain password policy?
Components of a domain password policy include password length, complexity requirements, password history, password expiration, and account lockout policies.



