Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
comforte Review and Alternatives

UPDATED: October 13, 2022
Are you looking for a top-notch data security solution tailored for your industry and specific needs? For example, a network’s? A solution that handles data privacy for your customers? Enter comforte.
comforte uses various methods to protect your data, from the traditional long-trusted data security methods like encryption and hashing to the newest and high-performance techniques. They focus on a data-centric approach to security with top-notch end-to-end data security with methods like tokenization, Format Preserving Encryption (FPE), and data masking.
comforte Review and Alternatives: Table of Contents
- Who is comforte?
- comforte’s products and solutions
- comforte’s data security platform
- comforte’s 5-step approach to data-centric security
- comforte’s dashboard
- comforte’s key features.comforte’s support, help, and pricing
- Top Five comforte’s SecureDPS Enterprise Alternatives
1. Who is comforte?
comforte is a German-based data security services and solutions provider founded in 1998. They started with a data-in-transit security solution but soon expanded their product portfolio to data-at-rest security.
Today, their security solution has become one of the market leaders, as it integrates with the major cloud providers and conventional core systems. comforte has also secured a top position due to its data-centric security approach and cloud-native tokenization.
comforte is the top choice for over 500 customers globally, including 15 of the largest banks in the world, three of the largest retailers worldwide, and four of the largest credit card processors.
comforte was awarded as the 2021 Globee Awards Grand winner of the Cyber Security Global Excellence Awards. It also holds other awards like the winner of the 2020 Cyber Security Excellence Awards, the Global Excellence Gold from Info Security Products Guide 2020, and a PCI winner for the award for excellence 2020.
2. comforte’s Products and Solutions
comforte offers software products and solutions that manage and protect third-party data that enterprises are responsible for. This data includes credit card, financial information, and health patients data.
Their products are JPath, CSL, PANfinder, SafePoint, SecurLib/SSL, SecurSSO, SecurTape, TOP, and their flagship product, SecurDPS.
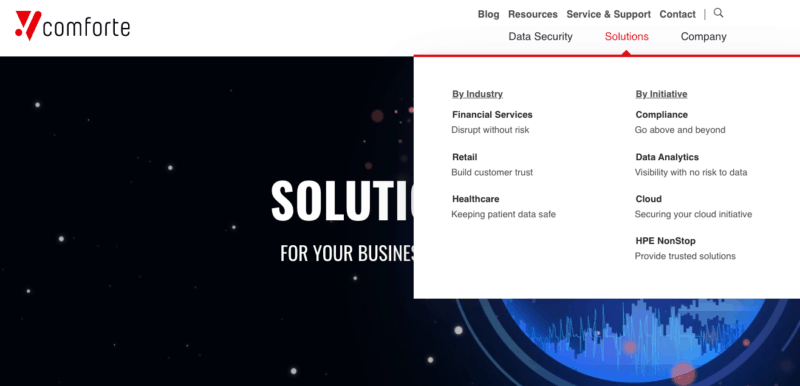
Their solutions are tailored by either industry or initiative.
- Based on the industry. comforte provides tailored solutions to fulfill the demands in specific industries, including Financial, Retail, and Healthcare.
- Compliance: comforte also offers solutions based on compliance like PCI, HIPAA, GDPR, CCPA, and more. A distinguishing feature is that comforte can help you achieve cross-regulatory compliance (i.e. PCI and GDPR).
- Data Analytics. A solution tailored to help organizations gain insights from their collected data and make faster and better decisions. comforte provides a data security solution based on analytics to let you access and analyze high-value assets without compromising security.
- Cloud. comforte data-centric solution protects your data before it goes to a cloud application. For instance, sensitive data is secured as soon as remote workers start uploading or sharing it across clouds.
- HPE Non-stop. comforte has developed solutions for fault-tolerant HPE NonStop computing solutions for more than 20 years. Read more about HPE NonStop Systems and comforte SecurDPS partnership.
3. comforte’s data security platform
As mentioned earlier, comforte’s flagship product is their end-to-end data-centric security platform, SecureDPS, which consists of three integrated software solutions: SecurDPS Discovery & Classification, SecurDPS Enterprise, and SecurDPS Connect.
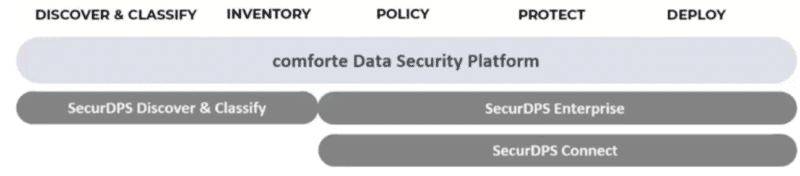
- SecurDPS Discovery & Classification. Automatically find, classify, and analyze data sets. This solution allows you to understand, in real-time, how your data is stored, processed, and shared. Plus, it identifies any potential security risk.
- SecurDPS Enterprise. A tool that integrates and monitors your data. SecurDPS Enterprise is the key software component that includes data-centric technology features such as data access/control policies, data (format-preserving) encryption, tokenization, and data masking.
- SecurDPS Connect: Connect to cloud-based services and applications. SecurDPS Connect protects all data stored in a cloud-service environment, following security and compliance standards.
4. comforte’s 5-step approach to data-centric security
comforte’s data security platform emphasizes on securing the data and its dependability rather than securing applications, servers, or networks. Such an approach is referred to as data-centric security, which aims to protect the data itself and not the perimeters.
comforte follows the common data-centric security processes: Discovery and classification, Inventory, Policy, and Control, Protect, and Deploy.
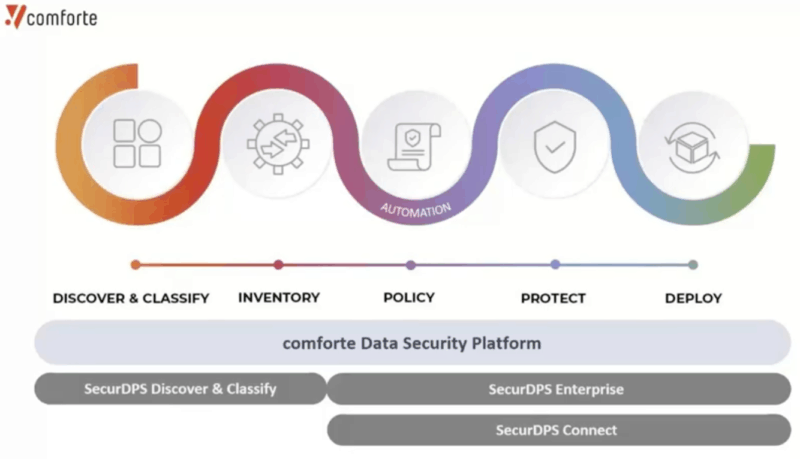
SecurDPS Discover & Classify performs the discovery, classification, and inventorying of data. SecurDPS Enterprise and SecurDPS Connect deal with the policy, protection, and deployment of data.
4.1 Discovery & Classification
comforte provides a policy system and automated AI-based solution that scans and discovers data as a continuous process. It helps you get a broader picture of the location, sensitivity, and data (structured or unstructured). Once, comforte discovers your data, it proceeds to classify and analyze all data sets. Classifying data helps you reduce data sprawl by identifying duplicate and redundant data and also helps improve security, privacy, and data governance. It can help you manage privacy for compliance regulations including GDPR, POPIA, CCPA, LGPD, and more. comforte can also assess the risk in the vulnerable unstructured (or structured) sensitive data and help you create security policies.
4.2 Inventory
Once comforte discovers and classifies your data, it proceeds to create an inventory of the data repository. The platform keeps scanning and discovering data continuously using minimal resources, to keep such inventory up to date. This inventory helps you associate identity data sets with lineage, ownership, compliance risk, and data movements. comforte calls this inventory, the “Master Data Catalog inventory.”
4.3 Access Control Policies
comforte delivers an integrated security policy management that allows you to protect and govern all access to the discovered data. It uses the discovery results to determine which data protection policy to use. The platform allows you to define policies that will determine if certain data is accessible, readable, editable, or blocked by particular users, applications, or locations.
4.4 Protect
comforte’s SecurDPS Enterprise platform provides various data protection mechanisms, capable of fully safeguarding a single element to auditing entire access controls. The platform offers diverse data protection mechanisms, including Encryption (Format-Preserving Encryption, or FPE), data tokenization, data masking, and hashing. Such mechanisms can be chosen for different use cases.
- Encryption – Can be either asymmetrical or symmetrical. The former is used to protect data-in-transit, while the latter is used to protect data-at-rest, volume-level encryption, or unstructured data encryption (file or device). comforte provides Format Preserving Encryption (FPE), a method that goes beyond traditional encryption.
- Hashing – Classified as Classic Hashing or Format Preserving Hashing (FPH). Classic hashing is used for password protection and validation. FPH, on the other hand, provides a flexible trade-off of data privacy protection and data value preservation for other uses. A use case of FPH is strong password protection for legacy applications.
- Data masking – A technique that replaces several characters of sensitive value with a set of masking characters. Data masking is often used for protecting non-production data or for providing limited data visibility to third parties, or in other words, obfuscating sensitive data. comforte offers either dynamic or static data masking.
- Tokenization – It can be classified as ODRA (On-Demand Random Assignment (ODRA), Static Table-based Tokenization, or Encryption-based tokenization (also referred to as Format Preserving Encryption.) The former, ODRA, can be used for high-value tokens (payment transactions) or Blockchain-based tokens. The other two types of tokenization methods are commonly used for protecting data ranging from PCI, PII, PHI, etc. More on comforte's tokenization features are below.
4.5 Deploy
The last step on comforte’s data-centric security approach is “Deploy.” comforte allows you to deploy data protection on your premises or cloud infrastructure by changing little to no-code. For instance, you can deploy comforte’s discovery instances distributed across different infrastructures so that they can aggregate all data.
5. comforte's dashboard
When you start with comforte, you’ll need to create an account, log in, and add a specific product. comforte comes with its product dashboard for each licensed product you get. So when you log in to your account, you’ll be able to get new or manage all your licensed products.
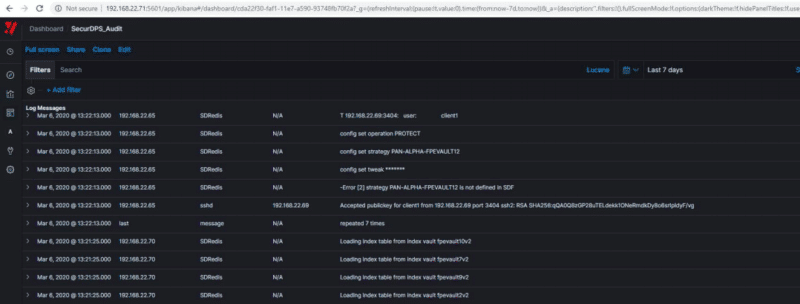
Below is a screenshot from the SecurDPS Audit Console dashboard, displaying log messages retrieved from the central management console.
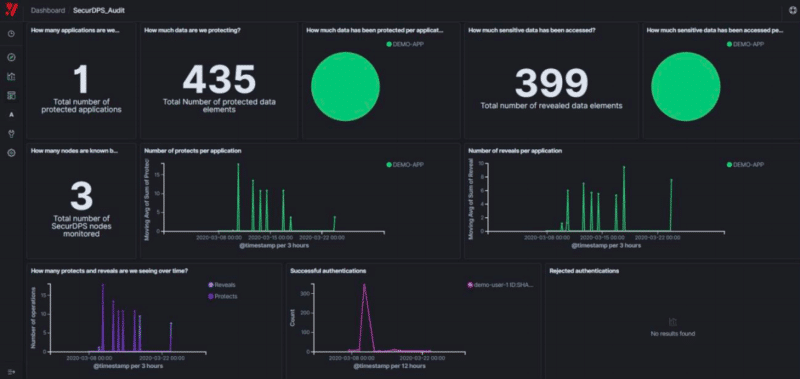
The below dashboard of the SecurDPS Audit also provides a view of the logs but is represented in graph and pie chart format.
6. Key Features
comforte is well known for its data-centric security methods (tokenization and FPE), robust integration mechanisms, and compliance and regulatory support.
6.1 Tokenization and Format Preserving Encryption
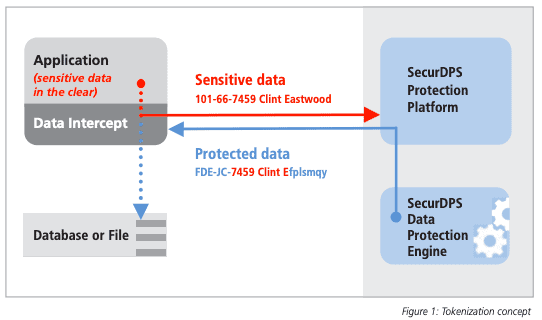
comforte's SecurDPS provides a high-performance, scalable, and fault-tolerant (patented) tokenization and encryption data protection solution. It allows you to configure different protection layers, including classic encryption, tokenization, format-preserving hashing, and masking. You can also combine different protection strategies and properties, like algorithm methods, the format (real characters left in-clear), specific techniques, and more. For instance, you can implement different tokenization methods based on performance, including On Demand Random Assignment-based Tokenization (ODRA), Static Table-based Tokenization, and Encryption-based Tokenization (also known as Format Preserving Encryption, FPE). In addition, comforte offers a unique Virtual Tokenizing File System that enables fast deployment to sophisticated batch and file-based processes.
FPE tokens can be used to protect sensitive structured data that needs to be preserved. This data includes credit card numbers, social security numbers, names, emails, or home addresses.
6.2 Platform Integration
The SecurDPS Enterprise platform comes with a flexible integration framework that allows multi-level data protection for your data in new or existing applications. The framework enables snap-in integration to your existing infrastructure so that the entire data's lifecycle can be protected. You can use comforte’s data protection capabilities to instrument your application, either by changing the configuration or without changing code. For example, with the SecurDPS Connect technology, you can secure traditional databases, cloud, web, SaaS, applications, and more by only using granular controls and without changing the code.
The SecurDPS platform integrates easily into your enterprise applications and cybersecurity infrastructures, such as an existing Security Information and Event Management (SIEM) framework. In addition, SecurDPS also comes with an easy-to-use and robust API and a modern RESP (Reddis standard) to integrate it in any programming language.
6.3 Cross-Regulatory Compliance
Usually, there are different data privacy demands and regulations for specific industries that overlap. For instance, international Payment Service Providers (PSPs) may have to comply with many data protection regulations laws. Although they have the exact core requirements, they differ in many other aspects.
comforte helps you achieve cross-regulatory compliance. comforte is quite famous for its cross-regulatory compliance for the PSPs. Within the payment industry, comforte can help you meet the PCI DSS and the data privacy regulations such as GDPR while still ensuring data privacy and protection. comforte also helps you with the requirements of other rules, including LGPD (Brazil) and the CCPA (State of California).
Pros:
- Enterprise focused security
- Has over 500 different customers including large banks
- Offers a suite of security offerings including SSO, DPS, and managed security services
Cons:
- Only serves enterprise customers
7. comforte’s support, help, and pricing
comforte offers diverse support channels to help you solve inquiries or technical issues. They include a robust ticketing system and a knowledge base. You can open and access support tickets from the web console and search the Knowledge Base from the same place.
How to contact comforte support? comforte offers 24×7 support via telephone or email.
Price?
comforte does not provide pricing plans and details. However, you can contact a comforte’s sales representative near your area or apply and schedule a live demo.
Trial?
If you want to test comforte before buying a license, you can request a trial license, but first, you’ll have to register to comforte.
8. Top Five comforte’s SecureDPS Enterprise Alternatives
There is no one-size-fits-all product and solution when it comes to Database and Big Data Security. Although comforte is one of the best for its data-centric top-notch security, with capabilities like tokenization, Format Preserving Encryption, and data masking, there are other alternatives in the market with diverse offerings for different scenarios.
Below are the top five comforte alternatives that offer similar capabilities.
1. Oracle
Oracle provides data security solutions such as Oracle-Data Masking and Subsetting, Oracle Advanced Security, and Oracle Data Safe. You can manage all these solutions from a single platform known as Oracle Enterprise Manager. Although Oracle does not provide the same data-centric security approach as comforte does, it provides ways to collect, manage, and protect data. For instance, Oracle protects data using various mechanisms like IP lists, single sign-on, access control, hashing, data redaction, and encryption for data-at-rest.
Pros:
- Provides data masking, data security, and network security in one platform
- Takes a holistic approach to enterprise security
- Integrates well with other Oracle products
Cons:
- Isn’t as data-centric as competing platforms
Read more on how Oracle can help fulfill your data security demands with additional security measurements.
2. Imperva
Imperva is a leader in security software and services. They develop software to protect data, applications, and edge endpoints. When it comes to data security, Imperva can be deployed to protect your on-premise or cloud data. Their approach to data security is based on different layers:
- Database firewall.
- User rights management.
- Data discovery and classification.
- Data Masking and encryption.
- Data loss prevention.
- Data user behavior analytics.
- Data Privacy.
- Database activity monitoring and alerting.
Imperva also helps with risk and compliance. For instance, the Imperva Database Security allows you to implement security and compliance policies and controls. It also unifies data governance across hybrid scenarios and provides advanced analytics to identify threats.
Pros:
- Combines in-depth audits and compliance tests with breach detection features
- Offers highly technical compliance auditing features, great for enterprise environments
- Available both as a cloud product or on-premise solution
Cons:
- No free trial
- Many features are not applicable to smaller organizations that don’t have to monitor compliance
Download a free trial of Imperva’s Cloud Data Security.
3. IBM (Guardium Data Privacy)
IBM is one of the leaders in the data security market. It provides enterprise data security solutions that can be deployed across multiple environments (on-prem and cloud). These solutions help meet privacy and compliance regulations and simplify the operational complexities.
IBM’s popular solutions are the Data Protection platform, data security services, data privacy, cloud data security, encryption, and cryptography for data protection. For instance, IBM’s Security Guardium helps you manage all your compliance data, discover all sensitive data, encrypt it, monitor, reduce data risk, and respond to threats.
Pros:
- Highly customizable encryption options that support multiple algorithms
- Supports both structured and unstructured data
- Cross compatible with Linux, Windows, and MacOS
- Features built-in compliance management tools
Cons:
- The platform comes with many different options that take time to discover and learn
To know more about the full suite of the IBM Security Guardium products, schedule a consult.
4. Thales Data Security
Thales Group is a multinational company that builds electrical systems and services for aerospace, defense & security, transportation. After acquiring critical players like the Alcatel-Lucent cybersecurity unit, Vormetric, and Gemalto, the group is also in the data security market. Today, Thales provides Data Protection products that compete with IBM, Oracle, and Microsoft.
Thales provides products including Data Discovery and Classification, Data-at-Rest Encryption, Key Management, Data Protection on Demand, General Purpose Hardware Security Modules, Payment Hardware Security Modules, Network Encryptors, and Secure File Sharing.
Pros:
- Focuses on data security – works with large enterprises and governments
- Offers SSO, hardware security, and data at rest encryption
- Helps bridge the gap between security and usability
Cons:
- Only for large enterprise companies
For more information on Thales Data Security’s products and a demo, contact a Thales sales representative.
5. SecuPi
SecuPi is a single centralized platform designed with a data-centric security approach that delivers data protection for compliance regulations (GDPR, CCPA, PCI, etc.) or security reasons. It provides data-flow discovery, real-time monitoring, behavior analytics, and overall protection across on-prem or cloud applications. This platform can also help you protect your applications with low code change to no-code change.
Highlights:
- Discover, classify, and map data.
- Real-time monitoring and auditing of user activity.
- Protect data with methodologies like masking, redacting, and encryption.
- Data access governance.
- Detect malicious activity with a combination of Dynamic Data Masking, Data Activity Monitoring, and User Behavior Analytics
Pros:
- Helps companies adhere to compliance regulations such as GDPR, CCPA, and PCI
- Can assist in discovering and classifying data
- Provides data protection as well as governance across the enterprise
Cons:
- Best for companies with large volumes of data
Schedule a SecuAPI Demo.



