Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
The Best Vulnerability Assessment and Penetration Testing (VAPT) Tools

UPDATED: January 25, 2024
Although Vulnerability Assessment (VA) and Penetration Testing (PT) are both processes used to identify weaknesses in systems, networks, or web apps, they do have differences.
First, a Vulnerability Assessment (VA) scans, identifies, and reports known weaknesses. It provides a report with the classification and priority of those discovered vulnerabilities. A Penetration Test (PA), on the other hand, aims to exploit vulnerabilities to determine the level of entry. It evaluates the degree of defense.
A VA is like walking up to a door, classifying it, and analyzing its possible weaknesses. A PT is like bringing chisels, lockpicks, or screwdrivers to work on those weaknesses. VA is usually automated, while a PT is performed by a security professional.
Here is our list of the best VAPT tools:
- Invicti Security Scanner – EDITOR'S CHOICE A robust vulnerability scanner and management solution tailored for enterprises. It can find and exploit weaknesses such as SQL injection and XSS. Download a free demo.
- Acunetix Scanner – GET DEMO A web app vulnerability scanner designed for SMBs, but can also scale for larger enterprises. It can identify SQL injection, XSS, or more. Get a free demo.
- ManageEngine Vulnerability Manager Plus – FREE TRIAL A security tool that helps organizations identify and address potential vulnerabilities in their network and devices. The software uses vulnerability scanning to detect potential vulnerabilities, such as missing patches or insecure configurations, and provides detailed reports on the results. Get a 30-day free trial.
- CrowdStrike Penetration Testing Services A consultancy service that performs white hat hacker attacks on your IT system from within your network and from external locations.
- Intruder An automated online web vulnerability assessment tool, that identifies a wide range of threats.
- Metasploit A robust framework with pre-packaged exploits code. It is supported by the Metasploit project with information on a massive number of vulnerabilities and their exploits.
- Nessus An open-source online vulnerability and configuration scanner for IT infrastructure.
- Burp Suite Pro A powerful bundle of tools for web app security, vulnerability scanning, and penetration testing.
- Aircrack -ng A set of wireless network security assessment tools, to monitor, scan, crack passwords, and attack.
- SQLMap An open-source penetration tool that specializes in exploiting SQL injection flaws.
- W3af A web application, attack, and audit framework. It identifies more than 200 web app vulnerabilities.
- Nikto A powerful vulnerability scanner for web apps, servers, and content management systems.
- Worthy Mentions Other tools that can help in the VAPT process: Nexpose, OpenVAS, Nmap, Wireshark, BeEF, and John the Ripper.
What is a VAPT Tool?
A VAPT tool performs a VA to identify vulnerabilities and a PT to leverage from those vulnerabilities to gain access. For example, a VA might help identify weak cryptography, but the PA will attempt to decode it.
The VAPT tools scan and identify vulnerabilities, generate a PA report, and in some cases execute code or payloads. VAPT tools help achieve compliance like PCI-DSS, GDPR, and ISO27001.
The Best Vulnerability Assessment and Penetration Testing (VAPT) Tools
Our methodology for selecting a vulnerability assessment and penetration testing tool
We reviewed the market for VAPT systems and analyzed options based on the following criteria:
- On-demand vulnerability scans
- Continuous testing option for ongoing vulnerability scanning
- The ability to alter test parameters and save the results
- Attack utilities that are linked to research tools
- Alert on detection of a security weakness
- A free trial or a demo that enables the system to be assessed before buying
- Value for money from a package that doubles up as a vulnerability scanner and a penetration testing tool
With these selection criteria in mind, we identified some interesting VAPT systems – some of the tools on the list are more for automated scanning, while others are suitable for manual penetration testing.
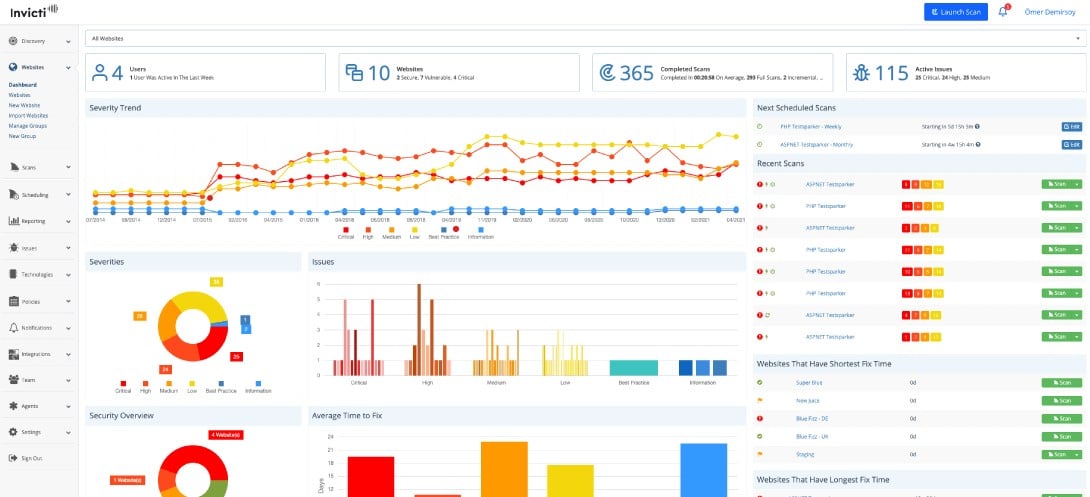
1. Invicti Security Scanner – GET DEMO
Invicti is an advanced VAPT solution. It automatically scans vulnerabilities in web applications, websites, and API. Netsparker uses proprietary Proof-Based Scanning to exploit an identified vulnerability and extract sample data. This process reduces (and sometimes eliminates) false positives.
Key Features
- Accurate vulnerability scanner
- Identify and test SQL injection, XSS, and more
- Automatically evaluates dangerous vulnerabilities and proves a sample exploit
- In-depth vulnerability reporting
- Built-in tools: HTTP request builder, encoding/decoding, ViewState viewer, retesting individual vulnerabilities
- Built-in workflow and vulnerability management along with support for issue tracking systems and CI/CD
Why do we recommend it?
Invicti is capable of scanning thousands of web assets for vulnerabilities on a constant basis thanks to its dynamic and interactive (DAST + IAST) scanning approach. It can even run codes through multiple scenarios and generate streamlined reports with remediation steps.
Who is it recommended for?
DevOps teams and businesses with their individual sites and microservices can make the best use of Invicti Security Scanner. However, home users or businesses who do not have access to any web system will not benefit from this advanced security tool.
Pros:
- Features a highly intuitive and insightful admin dashboard
- Supports any web applications, web service, or API, regardless of framework
- Provides streamlined reports with prioritized vulnerabilities and remediation steps
- Eliminates false positives by safely exploiting vulnerabilities via read-only methods
- Integrates into dev ops easily providing quick feedback to prevent future bugs
Cons:
- Would like to see a trial rather than a demo
Register with Ivicti to download a free demo
EDITOR'S CHOICE
Invicti is our top pick for a vulnerability assessment and penetration testing tool because it can be deployed externally or internally for vulnerability management or for development testing. This adaptable package can be used to test vulnerabilities in Web assets or it can be used as a Dynamic Application Security Testing (DAST) tool in CI/CD pipelines for Web application development. Available as an on-premises software package or as a SaaS platform.
Download: Access Free Demo
Official Site: https://www.invicti.com/get-demo/
OS: Windows Server or Cloud-based
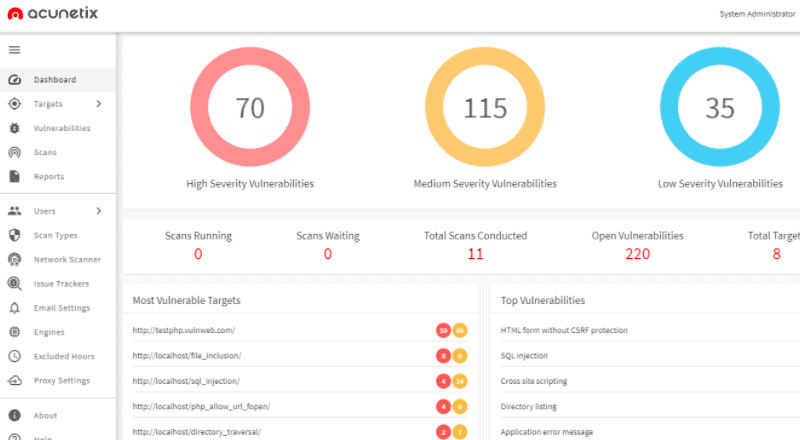
2. Acunetix Scanner – GET DEMO
Acunetix is a robust web vulnerability assessment and management tool. It automatically scans web apps, sites, and APIs, and identifies their vulnerabilities. Acunetix is capable of analyzing web apps developed with JavaScript, AJAX, or Web2.0.
Key Features
- Assess more than 4,500 vulnerability types
- Pentest SQL injection and DOM XSS Threats
- Integrate tests into a company's SecDevOps
- Generate security reports which are compliant with ISO/IEC 27001, HIPAA, and PCI-DSS standards
Why do we recommend it?
Acunetix Scanner is another popular tool similar to Invicti that helps scan and identify 4500+ vulnerabilities and security weaknesses in a website. You can even run a scan on external source code with Acunetix Scanner. Another use for this package in a CI/CD pipeline is as a continuous tester.
Acunetix uses the proprietary DeepScan to analyze and map the entire website. It also uses AcuSensor Technology to retrieve a list of all the files in the app’s directory. Finally, Acunetix scans vulnerabilities with the Automated Scan Stage tool.
Who is it recommended for?
DevOps teams and businesses that need to show compliance with security standards can invest in Acunetix to scan web assets.
Pros:
- Designed specifically for application security
- Integrates with a large number of other tools such as OpenVAS
- Can detect and alert when misconfigurations are discovered
- Leverages automation to immediately stop threats and escalate issues based on the severity
Cons:
- Would like to see a trial version for testing
The Standard edition of Acunetix is priced at $4,500 and the Premium edition at $7,000 for multiple-year contracts; subscribe to download a free demo!
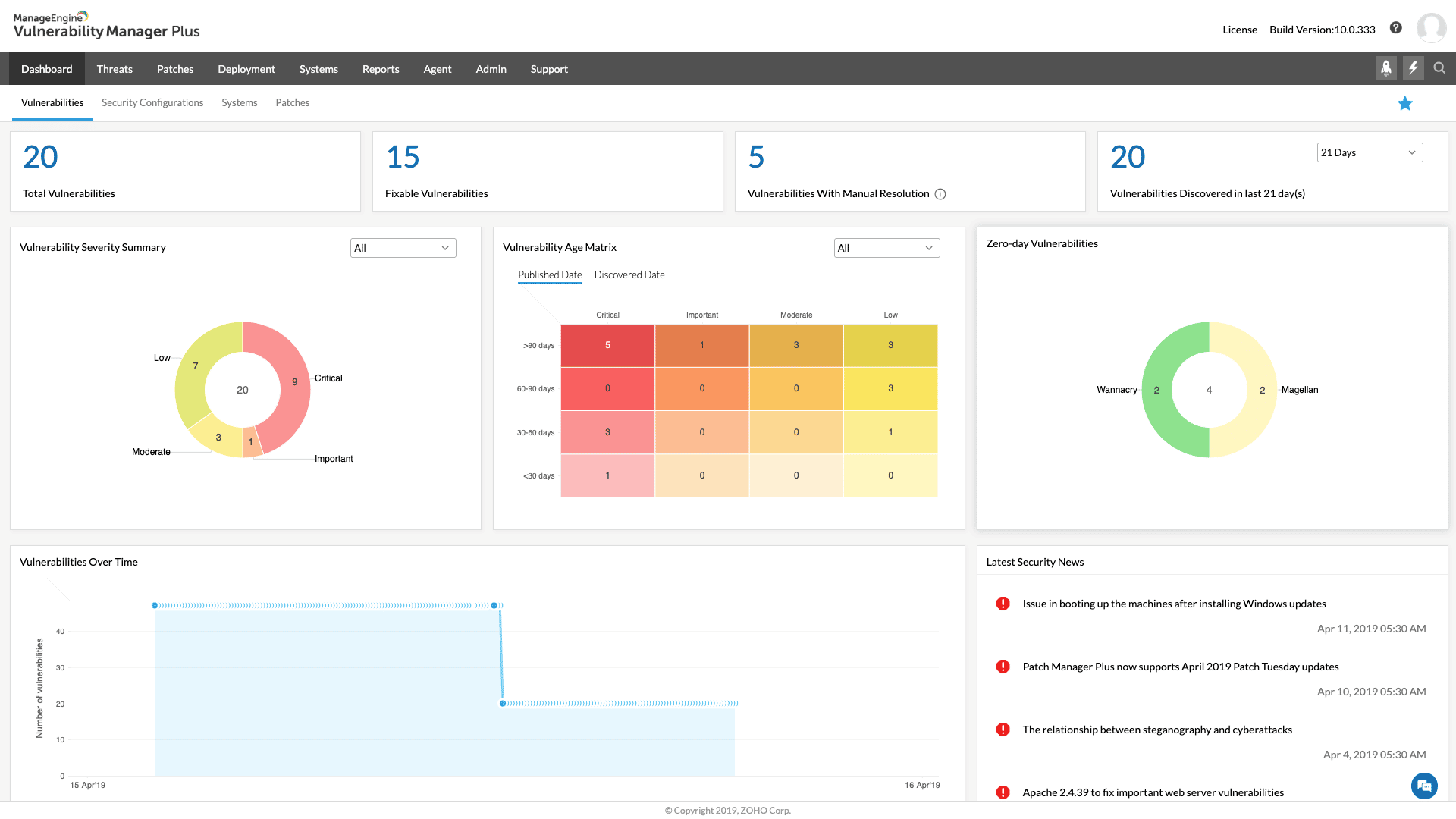
3. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus includes features such as asset management, patch management, and compliance reporting to help organizations maintain the security of their IT infrastructure.
Key Features
- Scans the network and devices for potential vulnerabilities, such as missing patches or insecure configurations, and provides detailed reports on the results
- Provides a comprehensive inventory of all devices on the network
- Provides guidance on addressing identified vulnerabilities, including step-by-step instructions and links to relevant resources
Why do we recommend it?
ManageEngine Vulnerability Manager Plus console provides comprehensive coverage, end-to-end visibility, and built-in remediation of threats all in a single place. It even supports running constant scans and patches throughout the device lifecycle.
The software provides remediation guidance to help organizations address identified vulnerabilities, including step-by-step instructions and links to relevant resources. Vulnerability Manager Plus can help organizations proactively identify and address potential vulnerabilities, improving the overall security of their network and devices.
Who is it recommended for?
Small businesses can make the best from ManageEngine Vulnerability Manager Plus thanks to its free version. Also, this package can only be used with Windows Server installed on the system; it will not work with any other operating system. On endpoints running Linux, macOS, and Windows, the patch manager can update software and operating systems.
Pros:
- Great for continuous scanning and patching throughout the lifecycle of any device
- Robust reporting can help show improvements after remediation
- Flexible – can run on Windows, Linux, and Mac
- Backend threat intelligence is constantly updated with the latest threats and vulnerabilities
- Supports a free version, great for small businesses
Cons:
- The ManageEngine ecosystem is very detailed and best suited for enterprise environments
You can download ManageEngine Vulnerability Manager Plus completely free through a 30-day free trial with all features.
4. CrowdStrike Penetration Testing Services
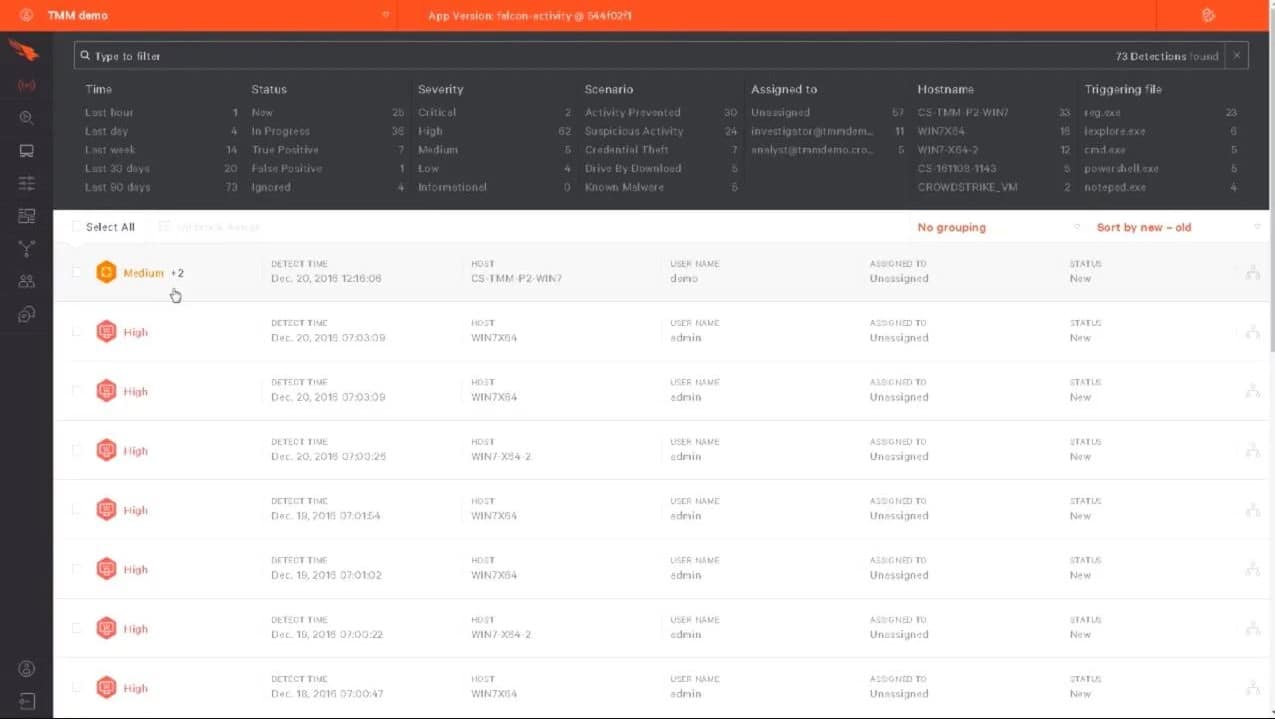
CrowdStrike Penetration Testing Services is a consultancy service that provides a hacker team to test the security of any system. This bespoke service is delivered from numerous locations around the world by a distributed team of white-hat hackers. The flagship product is CrowdStrike Falcon Prevent.
Key Features
- Internal penetration testing within the network to attempt lateral movement
- External penetration testing is launched from several remote locations to try to force through access protection systems and discover exposed external systems, such as IoT devices
- Mobile app security testing and device hacks
- Web application penetration testing that includes hijacking and corruption techniques, plus classic man-in-the-middle attacks
- Insider threat modeling
- Wireless network penetration testing
Why do we recommend it?
With CrowdStrike Penetration Testing Services, you no longer have to be dependent on log files as it uses a scanning process to defend organizations against sophisticated threats and stop breaches. It is an all-in-one tool that provides endpoint protections and notifies about anomalous behavior in real-time.
A penetration testing exercise from this group can be used to test the strength of your security system as well as for the discovery of actual system security weaknesses.
Who is it recommended for?
Small enterprises might find the tool a bit expensive as penetration testing is done by external consultants. However, large enterprises or businesses with high-value assets can make the best use of this tool to check website weaknesses and prevent threats.
Pros:
- Doesn’t rely on only log files to threat detection, uses process scanning to find threats right away
- Acts as a HIDS and endpoint protection tool all in one
- Can track and alert anomalous behavior over time, improves the longer it monitors the network
- Can install either on-premise or directly into a cloud-based architecture
- Lightweight agents won’t slow down servers or end-user devices
Cons:
- Would benefit from a longer 30-day trial period
The price for the bespoke penetration testing service is negotiable; gain insights into your network requirements with access to their flagship product, CrowdStrike Falcon Prevent.
5. Intruder Automated Penetration Testing
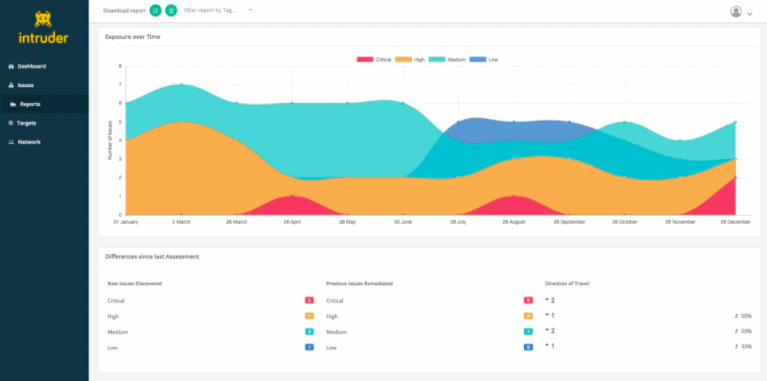
Intruder Automated Penetration Testing is a cloud-based scanner that identifies vulnerabilities in your IT infrastructure. It performs proactive security audits based on databases that contain the latest threats and vulnerabilities.
Key Features
- Managed service: Intruder’s Verified service includes manual evaluation by pen testers
- Wide integrations: Cloud (AWS, Azure, GCP), Slack, Jira, MS Teams, and Zapier
- Automate vulnerability management via Intruders Rest API
Why do we recommend it?
Intruder Automated Penetration Testing allows users to automatically schedule scans for vulnerabilities and weak points in a website using predefined rules and algorithms. It offers a human-powered penetration testing service that helps simulate more complex attacks that may elude automated detection. It even sends recommendations for updating machines running on outdated software.
Who is it recommended for?
Startups, SMBs, and IT Teams with less expertise can invest in Intruder Automated Penetration Testing solutions to identify and mitigate potential risks.
Intruder can assess the security of web assets by performing SQL injection or XSS. Additionally, it can also detect weaknesses such as remote code execution flaws and poor configuration, such as weak encryption and open ports.
Pros:
- Can perform scheduled vulnerability scans automatically
- Can scan all new devices for vulnerabilities and recommended patches for outdated machines
- Excellent UI – great over high-level insights and detailed breakdowns
- Offers human-powered penetration testing as a service
Cons:
- Is an advanced security platform that can take time to fully explore
- No free tier
The price for a Standard license with Intruder starts at $108.00/month, and you can subscribe to download a 30-day free trial.
6. Metasploit
Metasploit is a powerful open-source penetration testing framework. It has become a defacto standard for exploit development and even contains a module for zero-day reports.
Key Features
- Integrates well with third-party tools
- Security Loophole Discovery
- Identifies old hidden vulnerabilities
- Large community support
Why do we recommend it?
Metasploit is a reliable penetration testing tool available in both free and paid versions to its users for discovering security loopholes and overseeing vulnerability assessments. Unlike other tools in the list, it does not scan vulnerabilities but is great for defending against large-scale attacks.
Metasploit provides the following modules:
- Exploits
- Payloads
- Auxiliary functions
- Encoders
- Listeners
- Shellcode
- Post-exploitation code
- Nops
Metasploit does not scan for vulnerabilities, it only allows you to choose among exploits and drop payloads to any target. Fortunately, Metasploit integrates with reconnaissance tools such as Nmap (Network mapper), SNMP scanning, and more.
Who is it recommended for?
Many digital security experts and IT specialists have used the free version to find vulnerabilities. However, Metasploit is not a great option for network managers as it is a bit difficult to learn. Organizations with a good budget can try the Metasploit Pro version which comes with more automation features and guidance for testing and scanning vulnerabilities.
Pros:
- One of the most popular security frameworks in use today
- Has over of the largest communities – great for continuous support and up-to-date additions
- Available for free and commercial use
- Highly customizable with many open-source applications
Cons:
- Metasploit caters to more technical users, which increases the learning curve for beginners in the security space
Metasploit is available as a free and open-source tool, but you can also opt for Metasploit Pro, Rapid7's GUI version, which offers the same capabilities as Metasploit plus reporting features.
7. Nessus
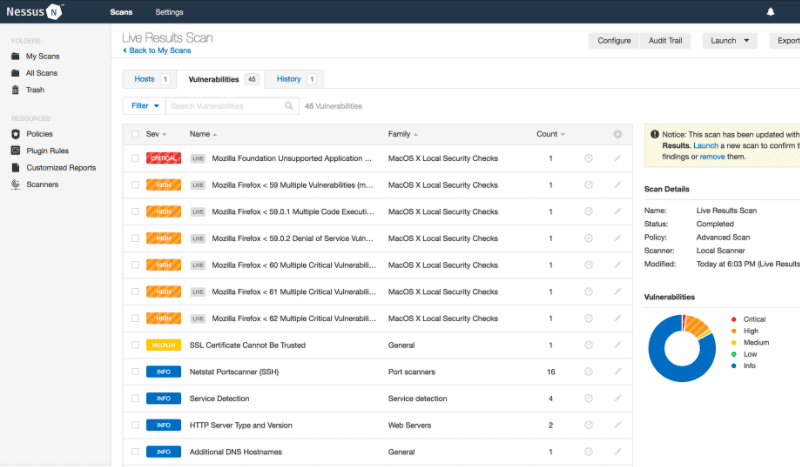
Nessus is an external vulnerability and configuration assessment tool. It scans IT infrastructure, including network devices, computer systems, databases, and hypervisors— and evaluates their vulnerabilities. Nessus detects misconfigurations, weak passwords, and even zero days.
Key Features
- A vulnerability scanner
- Can be integrated into a penetration testing kit
- External scanning and network scanning
Why do we recommend it?
Nessus is free of charge and comes with a wide set of features, such as 450+ templates and vulnerability assessment tools. Additionally, you can integrate Nessus well into penetration testing tools and make the best use of it.
Although Nessus is a vulnerability assessment tool, it can integrate with PT tools Hydra THC. Nessus finds weak passwords and Hydra THC performs dictionary attacks or brute force to crack those passwords. Additionally, you can also perform Nessus scans from within Metasploit.
Who is it recommended for?
Mostly cybersecurity consultancies and large corporations are looking forward to buying this tool as it is a bit costly. It is not a suitable choice for small businesses and startup companies due to its high-cost packages.
Pros:
- Offers a free vulnerability assessment tool
- Simple, easy-to-learn interface
- Little configuration is needed, 450+ templates that support a range of devices and network types
- Includes vulnerability prioritization
Cons:
- Offers limited remediation tools and options
- Could benefit from more integrations into other SIEM platforms
Nessus Essentials offers a free limited version, while Nessus Professional provides a full-featured subscription starting at $2790.00/year.
8. Burp Suite Pro
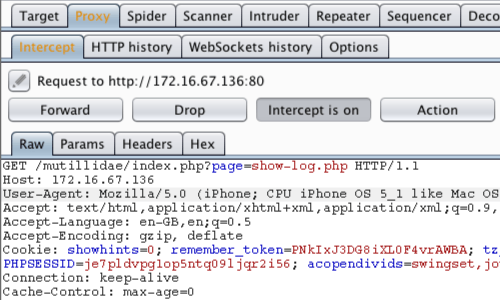
Burp Suite is a bundle of tools designed for web app vulnerability assessment and penetration testing. Its combination of tools from the scanner, proxy, intruder, decoder, etc., makes Burp Suite a robust VAPT tool.
Key Features
- Scan for injections, cache poisoning, serialized objects, and more
- Use Proxy to modify HTTP headers
- Scan for OOB vulnerabilities
- Generate clickjacking attacks
Why do we recommend it?
Burp Suite Pro is also a popular tool a bit similar to Metasploit but it has a user-friendly interface for its free users and supports OOB vulnerability scans. With this tool, users can even map an application's attack surface and examine responses that take place between programs and target servers.
The most popular tool is the Burp Vulnerability Scanner, which automatically crawls web resources and audits a varying degree of vulnerabilities. Burp Intruder is also handy for carrying out automated web app attacks including SQL injections and XSS.
Who is it recommended for?
The tool comes with a wide range of services and paid features that make it a perfect solution for security professionals. Even small businesses can use its basic features and enjoy the free community edition.
Pros:
- A collection of security tools designed specifically for security professionals
- The Community Edition is free – great for small businesses
- Available cross-platform for Windows, Linux, and Mac operating systems
Cons:
- Takes time to explore all the tools available in the suite
Burp Suite Pro is available starting at $399/user/year; subscribe to download a fully-featured trial.
9. Aircrack -ng
Aircrack -ng is a powerful VAPT for wireless networks. It is a suite of tools with a wireless packet sniffer, WPA/WPA2-PSK key cracker, packet injection, and attacks like replays, fake APs, and de-authentication. Aircrack-ng is supported by a wide range of wireless NICs and can capture packets from different WiFi standards.
Key Features
- Capable of cracking WEP & WPA-PSK keys
- Run WiFi security audits
- Supports Packet capturing
Why do we recommend it?
The ability to operate on wireless networks makes it stand out from the rest of the tools. You can track all the transmitting devices and crack weak wireless encryption using this tool.
Aircrack-ng includes:
- Airodump-ng for racket capture of raw 802.11 frames
- Airmon-ng to enable/disable monitor mode.
- Airbase-ng a tool for attacking clients (not APs)
- Aireplay-ng to generate traffic, which can be useful for cracking keys.
- Airtun-ng to create virtual tunnel interfaces
Who is it recommended for?
There is some risk to wireless networks from Aircrack-ng, so penetration testers should use it to see if their systems are open to attacks. Also, Aircrack -ng is free and compatible with all major operating systems.
Pros:
- Focuses heavily on wireless security – great for routine audits or field pen tests
- One of the most widely supported wireless security tools
- Can audit wifi security as well as crack weak wireless encryption
Cons:
- Focuses exclusively on wireless security – not an all-in-one tool
Aircrack-ng is free to download.
10. SQLMap
SQLMap is a popular open-source penetration tool used for identifying and exploiting dangerous SQL injection flaws. It comes with full capabilities tailored to taking control of databases. SQLMap can fingerprint databases, fetch DB data, access file systems, execute commands with Out-of-Band vulnerabilities, and more. SQL offers a fine-grain level of control to perform SQL injections.
Key Features
- Support of a wide range of database management systems
- Six different SQL injection modes
- Directly connect to a database with default credentials
- Powerful enumeration to extract data from databases
- Password cracking via dictionary or automatic recognition of hashes
Why do we recommend it?
The powerful detection engine of SQLMap plays a key role in SQL injection flaw discovery. With the help of these tools, users can directly connect to the database and upload files from the underlying file system of a server.
Who is it recommended for?
All Windows, Linux, Mac OS, and Free BSD users can access the open-source tool for free. SQLMap might have become an outdated tool yet useful for organizations who need to invest in a tool that helps detect and exploit SQL injection vulnerabilities.
Pros:
- Completely free
- Open source transparent project
- Specifically caters to identifying SQL attacks
- Available for Windows, Linux, Mac OS, Free BSD
Cons:
- Is slightly outdated when compared to other VAPT tools
SQLMap is free to download.
11. W3af
W3af (Web application attack and audit framework) is an open-source vulnerability testing framework. W3af is similar to Metasploit but for web applications. It effectively identifies more than 200 web app vulnerabilities including SQL injections, XSS, weak credentials, PHP misconfigurations, and more.
Key Features
- Web application scanning
- Crawl plugin for site mapping with web spiders
- Audit SQL injections and Cross-Site, and more
- Brute-force plugins like file authentication and file brute force
Why do we recommend it?
W3af supports several plugins that can help organizations enhance the features and functionalities of the tool. They can even find out all PHP misconfigurations and SQL injections using the tool.
W3af works via a set of plugins. These plugins are categorized as Audit, Auth, Bruteforce, Crawl, Evasion, Grep, Infrastructure, Mangle, and Output.
Who is it recommended for?
It is highly suitable for penetration testers and cybersecurity consultancies as they can run and perform in-depth audits for cross-site and SQL injection vulnerabilities. It might not be a great option if you are looking to detect vulnerabilities in internal systems.
Pros:
- Uses plugins to extend the functionality
- Ideal for in-depth auditing
- Can scan for over 200 vulnerabilities including SQL and XSS attacks
- Features a simple GUI interface
Cons:
- Better suited for security professionals
W3af is open-source and free.
12. Nikto
Nikto is an open-source web application vulnerability scanner. It performs specific vulnerability assessments on servers and discovers dangerous files, outdated software, and other specific problems.
Key Features
- Vulnerability on websites using SSL (HTTPS)
- Check syntax errors in databases and key files
- Create customizable reports for PT in txt, XML, HTML, or CSV
- Export report data to Metasploit
Why do we recommend it?
With Nikto, organizations can discover multiple threats, server misconfigurations, and vulnerabilities. It even supports generating custom reports in multiple formats and exporting the data to other tools like Metasploit.
Nikto can scan a web server against +6700 risky files or programs, +1250 outdated web server versions, and +270 server versions with specific problems. It also fingerprints web servers and software and detects server misconfigurations and HTTP server options.
Who is it recommended for?
Businesses of all sizes can leverage the free tool to scan their web servers and perform vulnerability assessments. If you are looking for a tool that is capable of detecting outdated software as well, you must try this tool.
Pros:
- Completely open source
- Performs comprehensive scans
- Can detect over 6700 threats
Cons:
- Does not support stealth scans
Nikto is free and open source.
13. Worthy Mentions
Below are six worthy mentions that can help in the VAPT process.
- Nexpose A robust vulnerability assessment tool. Some of the highlights of Nexpose are its risk score, remediation reports, and integration with Metasploit.
- OpenVAS An open-source vulnerability assessment and management software. OpenVAS was designed for Linux systems and includes more than 50,000 vulnerability tests.
- Nmap Network Mapper is one of the most popular scanning tools. Nmap can be used for manual VAPT, first because it lets you map the network and find their open ports.
- Wireshark A network protocol analyzer. Wireshark captures packets going through an interface and provides detailed information about those packets.
- BeEF Browser Exploitation Framework Project is designed to exploit web browsers with vulnerabilities and use them to launch attacks.
- John the Ripper An open-source tool that cracks passwords. It can perform dictionary attacks, brute force, or use rainbow tables to attempt to gain access.
Conclusion
The tools in this post help perform Vulnerability Assessment and Penetration Testing (VAPT). Tools like Invicti, Acunetix, and Intruder can assess vulnerabilities and provide a robust Pen Test report. Netsparker goes beyond by automatically evaluating dangerous vulnerabilities and proving a sample exploit.
Metasploit, W3af, Nessus, Burp Suite Pro, and Nikto are fantastic sets of tools that can help with VA and PT at the same time. SQLMap and Aircrack-ng are niche VAPT tools specific to databases and wireless.
Vulnerability Assessment and Penetration Testing (VAPT) FAQs
What is the difference between vulnerability assessment and penetration testing VAPT?
A vulnerability assessment is a scan of IT systems, looking for security weaknesses. The vulnerability scanner has a list of known vulnerabilities to look out for and will list each of the examples of each that it discovers during a system sweep. The relative value of competing vulnerability assessment tools lies in the size of the vulnerability database that each has. Penetration testing is usually a manual process and involves running a test to examine whether a detected vulnerability will actually prove useful to a hacker.
What is a VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) is a suite of tools for discovering and confirming the presence of security weaknesses in a system that can be exploited by hackers. Generally, vulnerability assessment is an automated process that is implemented by a system-wide scan. Penetration testing is usually a manual process that is implemented by white hat hackers.
What is vulnerability in cyber security?
A vulnerability is a system security weakness that can be exploited by hackers and intruders to get access to a system and then attack, destroy, tamper with, or steal resources. A vulnerability is also known as an exploit.
How does a VAPT tool work?
A VAPT tool works by scanning a system or application for known vulnerabilities and attempting to exploit them to simulate a real-world attack.
What is the difference between a vulnerability scanner and a penetration testing tool?
A vulnerability scanner is a tool that automates the process of identifying vulnerabilities, while a penetration testing tool is used to simulate an actual attack and test the security of a system.
What are the common features of a VAPT tool?
Common features of a VAPT tool include: vulnerability scanning, penetration testing, reporting and remediation, and custom scripting and plug-ins.
How do you choose a VAPT tool for your organization?
Choosing a VAPT tool for your organization requires consideration of factors such as your security needs, the size and complexity of your systems, and your budget.
Are VAPT tools easy to use?
The ease of use of VAPT tools varies, but many tools offer intuitive user interfaces and a variety of customization options to meet the needs of different users and organizations.