Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
Best Port Scanning Software & Tools for Windows, Linux and Online
UPDATED: March 21, 2023
I have always been thrilled by Security and the concept of hacking (legally) into a computer or network. Perhaps it has to do with all those movies I watched growing up. I digress. A big part of hacking has to do with vulnerability assessment – finding vulnerabilities (both digital and non-digital) that you can use to gain access to a computer/network.
One of the things you will normally do while carrying out a vulnerability assessment is finding open ports on a device and what services are running on those ports. By doing this, you may find a vulnerability that you can exploit in one of the services running on that device.
Here is our list of the six best port-scanning software and tools for Windows, Linux, and online:
- SolarWinds Open Port Scanner with ET – EDITOR'S CHOICE This tool is part of the Engineer’s Toolset, which is a package of more than 60 network administration tools. The scanner will perform device discovery and then scan each device in a given range to check on port statuses. Runs on Windows Server. Start 14-day free trial of Engineer's Toolset.
- ManageEngine OpUtils – FREE TRIAL A package of network address monitoring and administration tools that includes a port scanner. Runs on Windows Server and Linux. Start a 30-day free trial.
- Nmap A well-respected free utility to identify daemons running on a device by port number. This tool is a command line utility but it can be used with Zenmap to get a graphical user interface.
- Angry IP Scanner A free tool that provides a range of network detection tools including a port scanner. Installs on Windows, macOS, and Linux.
- Netcat An old command line network tool with a free port scanner. This tool has been forked into versions for Windows, macOS, and Linux.
- Online IP Scanning tools A range of websites that are able to scan the ports on a network gateway from a remote location.
In this article, we will be discussing some IP Scanning tools that can help check for open ports on a device and possibly probe for the services running on those ports.
Why would you want to check for open Ports/Services?
As we discussed above, one of the major reasons why you would want to check for open ports and services is while performing a Vulnerability Assessment. This could be done as an external consultant for an organization or in the capacity of the administrator of a network. The goal is to be a step ahead of attackers because whether you like it or not, they will come for you.
Another closely related reason is when performing a Security Audit of your device/network. For example, a router that isn’t managed over the web or terminating VPN connections should not be listening on ports 80 or 443. By performing a port/service scan, you can discover open ports and turn off unnecessary services.
You can also scan the open ports on a computer/server. Some malware (e.g. rootkits) open ports on systems that give attackers access to that system. I remember an organization I consulted for where we found that someone has gained access to a server and was sending a huge amount of data somewhere, eating up all the organization’s bandwidth.
Before we go into the tools that can be used for checking open ports and services, let me sound a note of warning: Port scanning can be deemed illegal and so you should never perform a port scan without authorization (preferably written) from the owner of the computer/network. This is because port scanning can reveal sensitive information about a computer/network that can be misused by an untrusted party.
Here's the Top Port Scanners of 2021:
We will now discuss some IP Scanning tools that can be used for checking for open ports and services. Most of the tools mentioned here have other uses but we will focus on their port scanning ability.
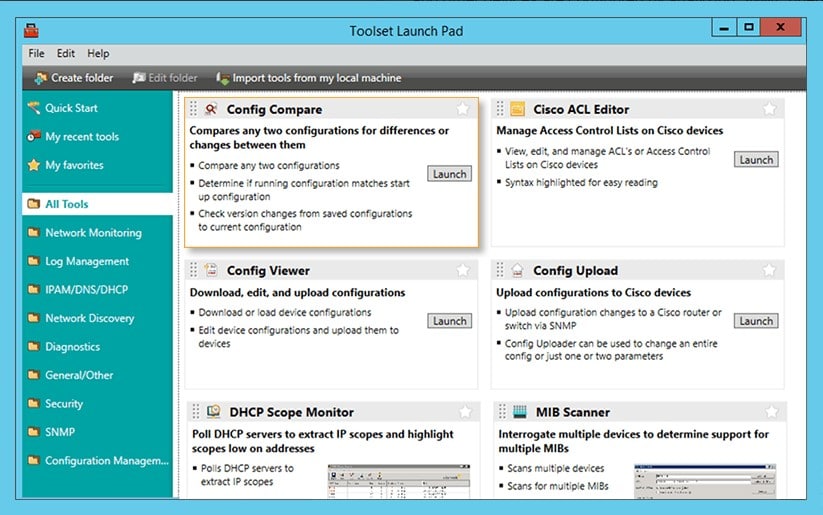
1. SolarWinds Open Port Scanner – FREE TRIAL
The Open Port Scanner from SolarWinds – which is part of the Engineer's Toolset – is a handy utility for discovering IP addresses in use as well as a port scanner. You launch a scan by specifying a range of IP addresses to look for – make that range impossibly wide and you will get all of the IP addresses on your network tested.
Key Features:
- Robust toolset for administrators
- Automated and manual scanning
- Detailed port status information
When the tool encounters an IP address that is in use, the service creates a record in the Open Port Scanner screen. This will show the open, closed, and filtered ports on each encountered device. The service will also show whether the port is operating TCP or UDP and you can filter results by that attribute.
The Open Port Scanner is a useful, but small utility. It is one of the many types of tools that you probably use to run your network but you waste time looking for it. The Open Port Scanner is part of a package of tools, called the Engineer’s Toolset. This bundle includes more than 60 useful tools and they are all accessible from the Engineer’s Toolset’s menu. This makes the port scanner easy to find.
Pros:
- A completely free tool
- Helps provide a more user-friendly interface to access features similar to Nmap and port scanning
- A better option for new network technicians
- Provides simple outputs based on what port scanning settings you choose
- A good option for home users and small businesses
Cons:
- Not designed for enterprise use, this tool lacks a few features found in their flagship product – SolarWinds Network Configuration Manager
The Open Port scanner and all of the Engineer’s Toolset run on Windows Server and you can get the package on a 14-day free trial.
EDITOR'S CHOICE
SolarWinds Open Port Scanner is our top pick for a port scanner because it is lightweight and easy to use but still manages to fulfill all of the tasks that you require from a port checker. This system will identify all of the IP addresses in use on your network and then check every port on each of the discovered devices. You can also choose to just scan a section of your network or just one endpoint. This tool is part of the Engineer’s Toolset, which gives you a full set of useful network management utilities.
Download: Start 14-day Free Trial
Official Site: https://www.solarwinds.com/engineers-toolset/registration
OS: Windows Server
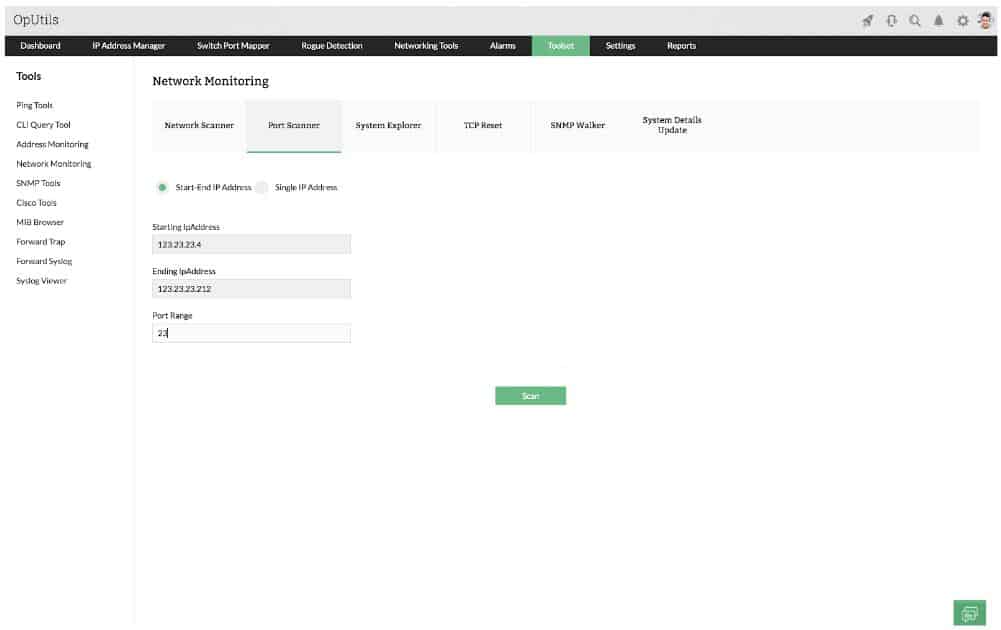
2. ManageEngine OpUtils – FREE TRIAL
ManageEngine OpUtils is a combination of an IP address manager, a switch port mapper, and network utilities. The word “port” in IT has two meanings – one is a hole on a switch that network cable plugs into and the other is an addressing system in the Transmission Control Protocol, which assigns a code number to each of the listeners that can be running on a computer, waiting for data coming in from the network. OpUtils operates with both of these two types of ports.
Key Features:
- A suite of port scanning tools and monitors
- Intuitive interface
- Supports both Linux and Windows operating systems
The OpUtils console includes a dazzling array of tools. Don’t be drawn to the Switch Port Mapper option on the top menu of the interface – that’s the other type of port. For a check on the statuses on TCP and UDP ports, go to the Toolset menu option and then select Port Scanner from the submenu that appears.
The service lets you scan all of the ports on one device by entering its IP address., IT is also possible to check the ports on a number of devices in one run be entering a range of IP addresses. The scan launch screen also allows the user to enter a range of port numbers to look through.
Pros:
- Offers a suite of tools that provide WoL, IP address management, and physical switch port mapping
- Gathers hostname, device status, and MAC address alongside IP address scans
- Identifies new machines via autodiscovery, great for larger deployments
- Available for both Windows server as well as Linux
Cons:
- ManageEngine is a large monitoring platform that offers a host of tools and features that may take time to fully explore
OpUtils installs on Windows Server and Linux. ManageEngine offers the system on a 30-day free trial.
Download 30-day Free Trial Now!
3. Nmap
Anyone who has been in the Networking or Security industry for a while will have heard about Nmap. Nmap which is short for “Network Mapper” can be used for a lot of things like network discovery, vulnerability assessment, network inventory, and so on. What’s more? Nmap is free and open source. In fact, a lot of network management tools include Nmap is one form or the other.
Key Features:
- Thoroughly documented
- Simple syntax
- Offers a GUI through sister tool “Zenmap”
Relevant to our discussion is using Nmap to check for open ports and services running on a device. Nmap handles this effortlessly. Not only will Nmap tell us the hosts that are available on the network (i.e. network discovery), it will tell us what services are running on those hosts (with a lot of information), and if you want, it can go as far as attempting to identify the operating system of the host.
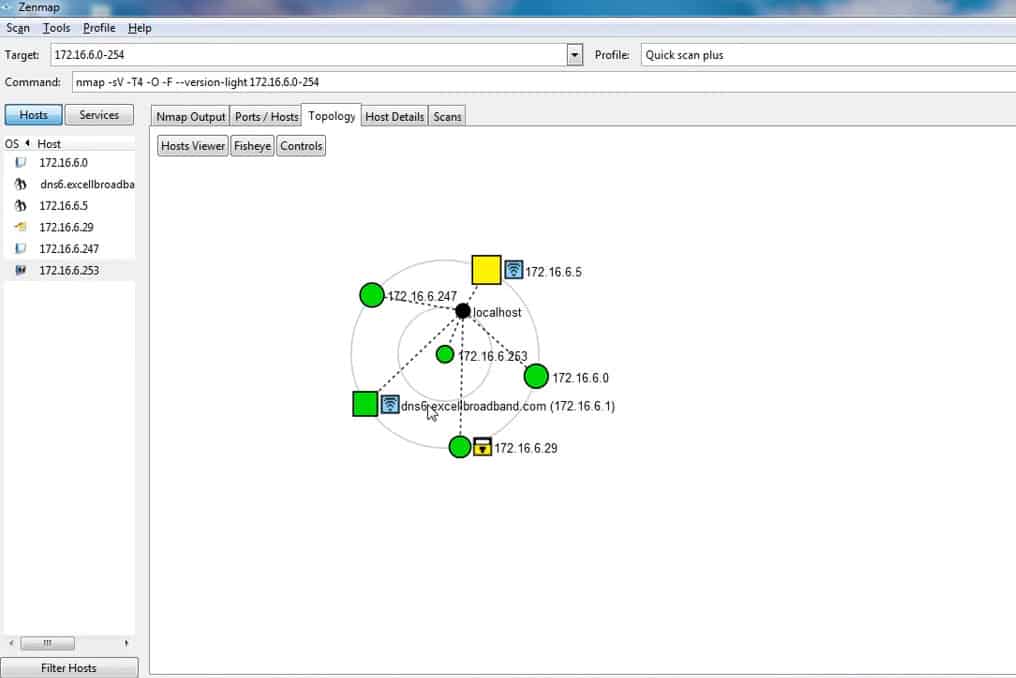
While most people will use Nmap from a terminal window or command prompt, learning how to use Nmap with all its various switches and options can be a daunting task for a new user. Therefore, a new user may want to use Zenmap which is a GUI for Nmap to perform scans and view results, as seen in the screenshots above and below.
Zenmap provides in-built “profiles” that can be used to perform popular scans (e.g. Ping scan, Quick Scan, Intense Scan) without having to know which options to use.
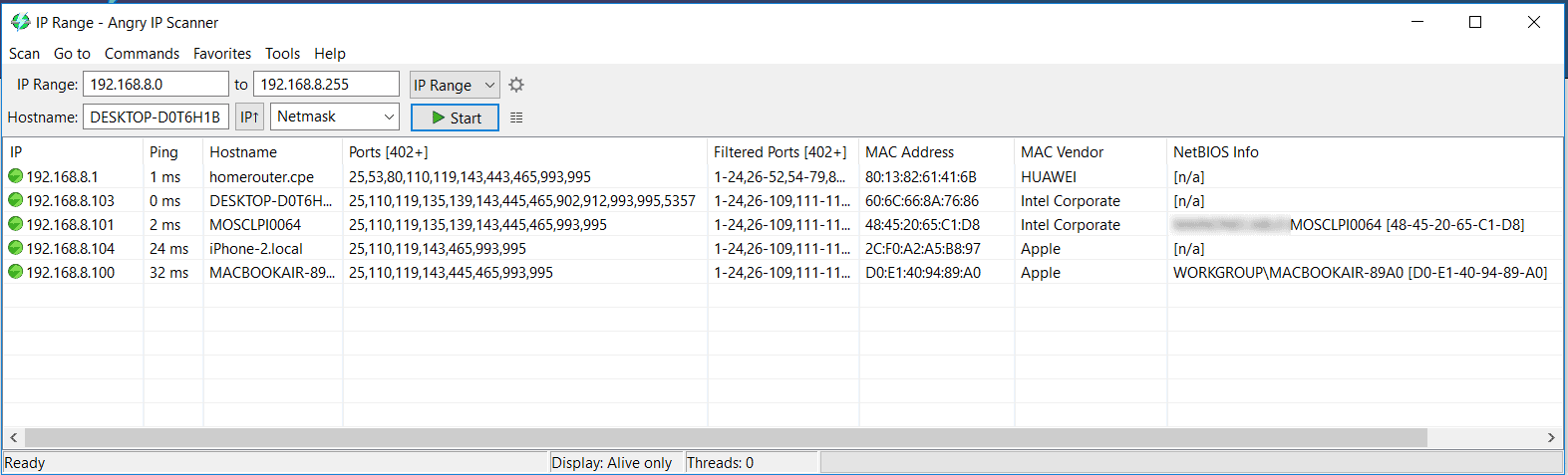
To see how Nmap works, I will scan my home wireless network which is on the 192.168.8.0/24 subnet. There are a couple of devices on this network, from my Macbook to Windows PCs, and also phones.
To start off, I will run a basic Ping Scan to check what hosts are available on that network using the command: nmap -sn 192.168.8.0/24
Starting Nmap 7.60 ( https://nmap.org ) at 2018-02-03 23:47 WAT Nmap scan report for homerouter.cpe (192.168.8.1) Host is up (0.0030s latency). Nmap scan report for 192.168.8.100 Host is up (0.0012s latency). Nmap scan report for 192.168.8.101 Host is up (0.0066s latency). Nmap done: 256 IP addresses (3 hosts up) scanned in 15.60 seconds
As you can see, it discovered that there are 3 hosts available on the network. This does not mean there are no other hosts (because there are); it just means these are the ones that responded to ping.
I have noticed that by running the ping scan with elevated privileges (e.g. sudo), I can get more information:
$ sudo nmap -sn 192.168.8.0/24 Starting Nmap 7.60 ( https://nmap.org ) at 2018-02-03 23:49 WAT Nmap scan report for homerouter.cpe (192.168.8.1) Host is up (0.0023s latency). MAC Address: 80:13:82:61:41:6B (Huawei Technologies) Nmap scan report for 192.168.8.101 Host is up (0.074s latency). MAC Address: 48:45:20:65:C1:D8 (Intel Corporate) Nmap scan report for 192.168.8.103 Host is up (0.074s latency). MAC Address: 60:6C:66:8A:76:86 (Intel Corporate) Nmap scan report for 192.168.8.100 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 28.29 seconds
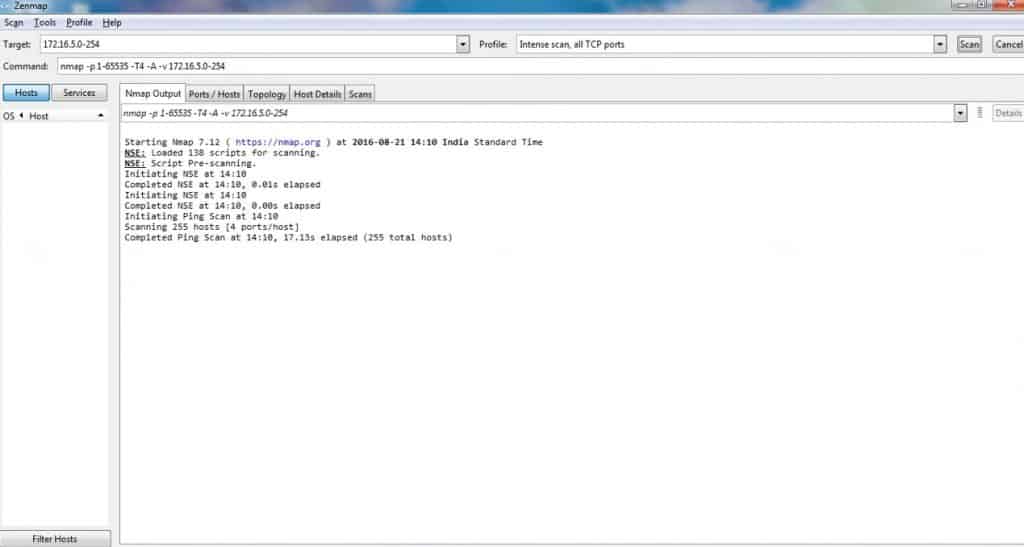
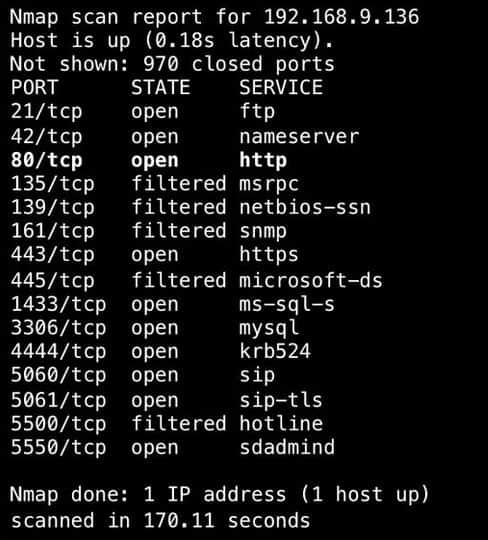
Now that we have discovered the hosts on the network, we can go ahead to probe them further. Let’s take the device with an IP address of 192.168.8.101 as an example. We will run a scan that will perform OS detection, determine open ports, and also probe the open ports for the services running on them. A simple command that will achieve all these is: nmap -A 192.168.8.101
Starting Nmap 7.60 ( https://nmap.org ) at 2018-02-04 00:13 WAT Nmap scan report for 192.168.8.101 Host is up (0.010s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Windows 10 Pro 15063 microsoft-ds (workgroup: <!scrubbed>) Service Info: Host: MOSCLPI0064; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_nbstat: NetBIOS name: MOSCLPI0064, NetBIOS user: <unknown>, NetBIOS MAC: 48:45:20:65:c1:d8 (Intel Corporate) | smb-os-discovery: | OS: Windows 10 Pro 15063 (Windows 10 Pro 6.3) | OS CPE: cpe:/o:microsoft:windows_10::- | Computer name: MOSCLPI0064 | NetBIOS computer name: MOSCLPI0064\x00 | Domain name: <!scrubbed> | Forest name: <!scrubbed> | FQDN: MOSCLPI0064.<!scrubbed> |_ System time: 2018-02-04T00:13:37+01:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2018-02-04 00:13:37 |_ start_date: 2018-01-26 12:15:31 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 29.50 seconds
Note: I had to scrub the data to protect sensitive information. Also, the result would have been more detailed if I had run it with elevated privileges.
Pros:
- Doubles as a security tool, allowing administrators to discover open ports, and applications communicating over ports that are suspicious
- Massive open-source community is one of the most popular free security tools available
- Offers a GUI version, Zenmap, which lowers the barrier to entry for new users
- Syntax is straightforward and not difficult to learn for most users
Cons:
- Nmap can have a steep learning curve for new users
- Might be overkill for simpler troubleshooting tasks
- More of a security/auditing tool
As you can see, Nmap is an awesome tool and we have barely scratched the surface. You can perform different TCP/UDP scans, and even try to bypass firewalls that block port scanning attempts. Nmap is available on most operating systems including Windows, Mac, and Linux.
Download Nmap/ZenMap from their official Site:
https://nmap.org/download.html
4. Angry IP Scanner
The next tool on the list is Angry IP Scanner. Even though this tool is quite simple, its speed is mind-blowing because it uses multithreading i.e. multiple threads to scan a network.
Key Features:
- Easy-to-use interface
- Fast port scanning and device discovery
- Supports MacOS, Linux, and Windows operating systems
Angry IP Scanner is a GUI-based tool that can detect open and filtered ports, resolve MAC addresses to vendors, provide NetBIOS information, and so on. Unlike Nmap and SolarWinds Port Scanner, it cannot do OS detection, nor does it probe open ports for the services running on those ports.
From the test I ran on my home network, it seems to have more false positives than Nmap because it found open ports that were not really open. However, it correctly listed all the truly open ports on all devices.
Angry IP Scanner can be installed on Windows, Mac, and Linux operating systems. However, it requires Java to run.
Pros:
- Easy to install and use – great for a mobile toolkit
- Better suited for one-off scans of small networks
Cons:
- Lacks advanced features such as DHCP reconciliation and rouge DHCP identification
- Doesn’t scale well in large environments
- Lacks detailed reporting that’s useful in enterprise networks
Download Angry IP Scanner from their Official site here:
5. Netcat
The last tool we will discuss is Netcat. Netcat is an old tool (dates back to 1995!) and is popularly called the “swiss army knife” utility of a network/security engineer. The main purpose of Netcat is to “read and write data across network connections”; however, it also has an inbuilt port scanner. Even though the port scanning feature is not anything fancy, it gets the job done.
Key Features:
- Lightweight
- Robust CLI commands
- Support for various operating systems
Let’s scan the 192.168.8.101 host using netcat. The following command tells netcat to scan TCP ports 1 to 500 on host 192.168.8.101 without sending any data (-z) and timing out after 1 second (-w1): nc -v -z -w1 192.168.8.101 1-500. The -v option enables verbose mode.
MOSCLPI0064 [192.168.8.101] 465 (?) open MOSCLPI0064 [192.168.8.101] 445 (microsoft-ds) open MOSCLPI0064 [192.168.8.101] 143 (imap) open MOSCLPI0064 [192.168.8.101] 139 (netbios-ssn) open MOSCLPI0064 [192.168.8.101] 135 (epmap) open MOSCLPI0064 [192.168.8.101] 119 (nntp) open MOSCLPI0064 [192.168.8.101] 110 (pop3) open MOSCLPI0064 [192.168.8.101] 25 (smtp) open
Note: The open ports on netcat and Angry IP Scanner seem to match.
Pros:
- Available cross-platform for Windows, Linux, and Unix operating systems
- Simple syntax, easy to learn for beginners
- Doubles as a security tool, allowing users to probe endpoints and create backdoors
- Supports file transfer between host and client
Cons:
- NetCat might be overly complicated for users looking for a simple IP scanner
The original version of Netcat is not maintained anymore. However, there are several variants and implementations available and you should be able to get one for Linux, Mac, and Windows operating systems with a good Google search.
Your can find the Original download of Netcat at Sourceforge:
6. Online Tools
While the tools we have discussed so far need to be installed (or executed) on a PC, there are IP and network scanning tools available online for checking ports and services. Of course, these tools will not be able to scan your internal network but they can be used to scan publicly available devices. For example, if you are hosting your own server (e.g. Digitalocean droplet, AWS instance), you can use these tools to audit them.
Note: All the tools we have mentioned above can also be used to scan external hosts.
Key Features:
- It doesn’t require installation
- Easy to use
- Can scan networks from the outside
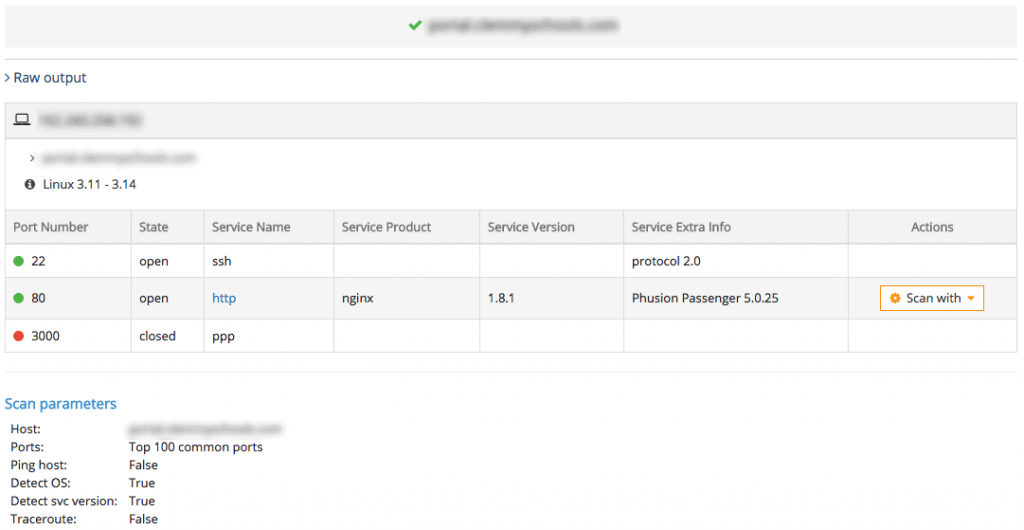
Some online IP scanning tools include TCP Port Scan with Nmap from Pentest-Tools.com, MxToolBox’s Port Scan, IPFingerPrint’s Open Port Checker & Scanner, etc.
Here is a snapshot of the open ports on one of my servers using TCP Port Scan with Nmap from Pentest-Tools.com:
Conclusion
In this article, we have looked at various IP and Port Scanning tools for checking open ports and services. If you are looking for a very fast tool that provides basic port checking, then go for SolarWinds scanning tool.
The SolarWinds Port Scanner is also a good tool with a nice GUI and easy to use and works without any faults or issues whatsoever. The interface and GUI is updated and the tool seems to be updated quite often. If you are a power-user and like to get your hands dirty, then Nmap might be the solution for you due to its array of options, although there may be a bit of learning curve to it. I can tell you it's not nearly as easy to run scans using Nmap (even the GUI) as it is with Angry Ip Scanner and SolarWinds scanner.
Finally, keep in mind that the results you will get when performing a port scan from an internal network will be different from your results when coming from the outside. This is because of the various filtering devices that will block access from the outside.
Also, before using a Port Scanner on a network, make sure you get the proper permissions from the network administrator or engineer, as some of these scanners can throw off some flags in IDS or on their Firewalls!
Port Scanning Software & Tools for Windows, Linux & Online FAQs
How does port scanning software work?
Port scanning software works by sending a series of packets to a target system, and analyzing the response to determine which ports are open and what services are running on those ports.
What are the different types of port scanning software?
There are several types of port scanning software, including basic port scanners, stealth port scanners, version detection scanners, and vulnerability scanners.
What are some common features of port scanning software?
Common features of port scanning software include the ability to scan specific ports, the ability to scan multiple systems simultaneously, and the ability to save and export scan results.
What are some popular port scanning software tools?
Some popular port scanning software tools include Nmap, Angry IP Scanner, and Advanced Port Scanner.
Is port scanning software legal?
The legality of port scanning software depends on the specific circumstances and laws in your jurisdiction. In general, port scanning software can be used for legitimate purposes such as pentesting and security audits. Using port scanning tools on networks you do not own is typically illegal.
What are the potential dangers of using port scanning software?
The potential dangers of using port scanning software include increased security risks, potential legal consequences, and the possibility of causing unintended harm to the target system. It is important to use port scanning software responsibly and with caution.