Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
The Best Tools for Penetration Testing
UPDATED: October 23, 2023
A penetration test (pen test) can be performed by hiring a certified professional or someone with strong ethical hacking skills to find vulnerabilities and attempt to breach them. The pen tester will assess the security by following the steps: defining the scope, reconnaissance/intelligence, scanning, finding vulnerabilities, gaining access, and reporting.
Every step along this process is executed with the help of a variety of penetration testing tools and a lot of skills.
Here is our list of the twelve best penetration testing tools:
- Intruder Automated Penetration Testing – FREE TRIAL A cloud-based vulnerability scanner that helps automate pen testing for websites and web applications.
- CrowdStrike Penetration Testing Services A consultancy service that provides white hat hackers to perform penetration testing from remote locations, using a range of scenarios. Access a 15-day free trial of Falcon Prevent.
- Indusface Penetration Testing Services A consultancy service that provides a professional team of penetration testers to assess the security of applications, and APOs.
- Invicti Security Scanner A comprehensive vulnerability management solution capable of scanning for web application vulnerabilities (SQL injection, XSS, etc), and integrating with tracking systems and CI/CD pipelines software.
- Acunetix Scanner A web application vulnerability scanner that checks a web application or website and attempts to find vulnerabilities like SQL injection, XSS, or more.
- Nmap and Zenmap CLI and GUI network mappers, capable of scanning the network via simple ping sweeps or intense TCP/UDP scans.
- Wireshark A robust network protocol analyzer capable of providing deep information about network protocols, packet information, etc.
- Metasploit Framework A powerful tool to test the network and server vulnerabilities. It uses pre-packaged exploit code (payload) to attempt to bypass security measures.
- John the Ripper A password-cracking software used for finding weak spots. It can run on brute force or dictionary attack.
- Aircrack -ng A suite of WiFi network security assessment tools. It can monitor, capture packets, test security, and crack passwords.
- Nessus A free and open-source remote vulnerability scanner for servers, network devices, OS, databases, and hypervisors.
- Kali Linux A complete distribution that gives you access to more than 600 tools.
- PLUS – Six Worthy Mentions Other tools that didn’t make it to the top list, but are worthy mentions: BeEF, W3af, THC Hydra, Maltego, SQL Map, and Nikto.
Some manual penetration testing tools require a high level of expertise to use them. But other testing tools are automated vulnerability scanners, which are easier to use and can turn out to be much more efficient for particular scenarios. Combining both types of tools is the best strategy.
On one hand, a security professional with knowledge on how to use these “manual” tools could be able to find the most complex and sophisticated vulnerabilities— where no automation tool is capable of.
But automatic vulnerability scanners can help the pen test to be faster and continuously monitor for vulnerabilities. Automatic vulnerability scanners can also find vulnerabilities such as development mistakes, misconfigurations, etc, much faster.
The Best Tools for Penetration Testing (+Six Worthy Mentions)
1. Intruder Automated Penetration Testing – FREE TRIAL
The Intruder Automated Penetration Testing is an online network vulnerability scanner. It can check for different types of application weaknesses, including SQL Injection, XSS, XML injection, and more. It can also identify infrastructure weaknesses such as remote code execution flaws, and misconfigurations like weaknesses in (or lack of) encryption in SSL/TLS or VPNs.
Key Features:
- With +140,000 security checks available.
- A recommendation engine that helps you reduce risks.
- Updated threat intelligence database.
The tool also performs banner-grabbing or fingerprinting to identify missing patches. When it detects a vulnerability, it creates a comprehensive report with recommendations.
Pros:
- Can perform schedule vulnerability scans automatically
- Offered as a cloud-service, making the platform highly scalable
- Excellent UI – great over high-level insights and detailed breakdowns
- Offers human-powered penetration testing as a service – great for enterprise environments
Cons:
- Is an advanced security platform that can take time to fully explore
Price and trial. There are three licenses, Essential (€78/ mo), Pro (€131/ mo), and Verified (€955/ mo). Subscribe to get a 14-day free trial.
2. CrowdStrike Penetration Testing Services
Although this list is all about penetration testing tools, this entry isn’t a tool but a consultancy service. If you don’t have the confidence to perform penetration testing yourself, use an external team instead. CrowdStrike's flagship tool which this service is attached to is Falcon Prevent.
Key Features:
- Internal and external penetration testing
- Testing for Web applications, mobile apps, and APIs
- Insider threat modeling
- An opportunity to watch the intrusion and assess your installed security software
- Detailed assessment reports with recommendations on system hardening
- Tests for wireless networks, WANs, and cloud resources as well as LANs
Consultancy penetration testers can usually perform a better job at probing the security of your system than you or your team can. This is because they approach your system with fresh eyes, they have years of hacking experience, and they don’t have the reservations that you would have about being gentle. They will truly expose your system’s weaknesses.
Pros:
- Excels in hybrid environments (Windows, Linux, Cloud, BYOD, etc)
- Intuitive admin console makes it easy to get started and is accessible in the cloud
- Can track and alert anomalous behavior over time, improves the longer it monitors the network
- Lightweight agents take up little system resources
Cons:
- Would benefit from a longer trial period
Price and trial: CrowdStrike Penetration Testing Services is a consultancy that quotes a price after a consultation over requirements rather than publishing a price list. To figure out your network requirements, you can access a 15-day free trial of CrowdStrike Falcon Prevent.
3. Indusface Penetration Testing Services
Indusface Penetration Testing Services is provided by a team of white hat hackers that will probe your system to discover the types of damage that could be implemented by real hackers. The group will test applications, such as Web applications and mobile apps, and APIs, including microservices.
Key Features:
- A professional team of experienced penetration testers
- A bespoke service
- Research into software hosted by third parties
The idea of hiring an external team of consultants to perform your penetration testing is one that brings greater efficiency and expertise than you could get by having your in-house technicians perform that tests. External testers are objective and have no emotional relationship to the system. This means that they are more likely to model the actions of real-world hackers more closely than your own team would.
Pros:
- Leverages ethical hackers to identify threats missed by automated scans
- Offers a subscription service to perform continuous scans – set it and forget it
- Helps close bugs proactively and prioritize threats for your remediation team
- Ideal for larger organizations or businesses looking to acquire or launch a new digital product
Cons:
- Caters to enterprise networks – not the best fit for smaller environments
Price and trial: As this is a bespoke consultancy service, there is no fixed tariff or menu of services. Instead, you negotiate a price. So, Hire an Expert instead of running your own penetration testing exercise.
4. Invicti Security Scanner
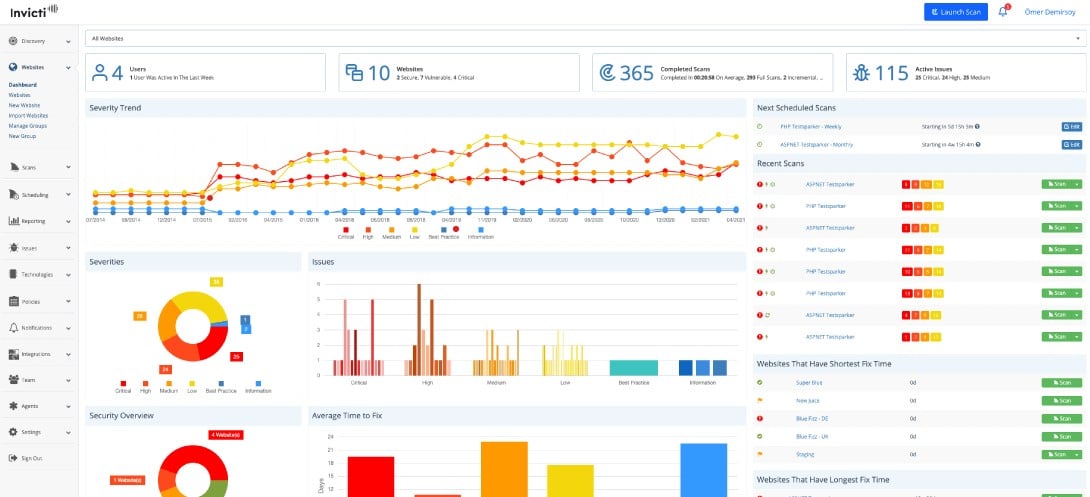
Invicti is a robust vulnerability management solution. It scans web applications, services, and APIs, automatically identifies a broad coverage of different vulnerability types. The tool emulates attacks to test the target’s defenses against SQL Injections, Cross-Site Scripting (XSS), and more.
Key Features:
- Proof-Based Scanning technology to help reduce (or eliminate) false positives.
- Out-of-the-box support of issue-tracking systems such as Jira.
- Integrate scans into the CI/CD pipeline with GitHub.
- In-depth technical reports including recommendations to fix the security flaws.
- Reports to help meet regulatory compliance like PCI DSS and OWASP Top 10.
The Invicti web app security scanner can automatically assess between 500-1000 web applications simultaneously. You can also customize the scan with attack settings, authentication, URL rewrite rules, etc.
Pros:
- Features a highly intuitive and insightful admin dashboard
- Supports any web applications, web service, or API, regardless of framework
- Provides streamlined reports with prioritized vulnerabilities and remediation steps
- Eliminates false positives by safely exploiting vulnerabilities via read-only methods
- Integrates into dev ops easily providing quick feedback to prevent future bugs
Cons:
- Would like to see a trial rather than a demo
5. Acunetix Scanner
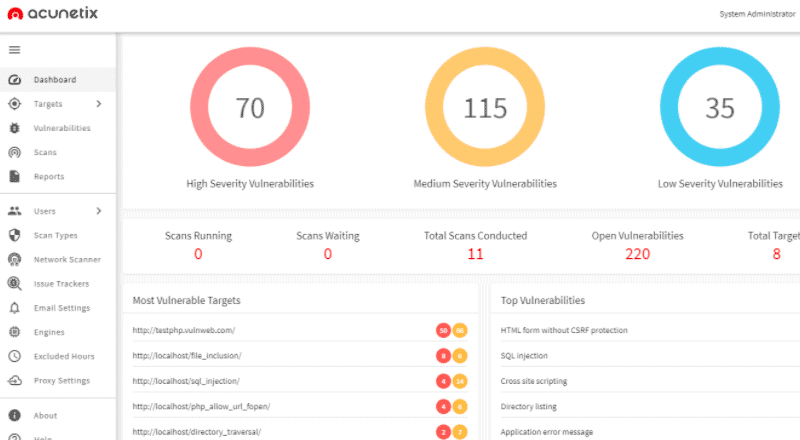
Acunetix Scanner is a dynamic web application security testing solution. It audits web applications, sites, and API, and identifies vulnerabilities such as SQL injection, XSS, weak passwords, misconfigurations, Out-of-Band (OOB) vulnerabilities, and more.
Key Features:
- It can detect +6500 vulnerabilities with a high detention rate.
- Integrate with Jenkins, GitHub, GitLab, TFS, Mantis, and more.
- Acutenix API to connect to more security controls.
- The fast scanning engine is written in C++ with concurrent crawling and incremental scanning.
- Acunetix Scanner engines can run on-premises or on the cloud.
The Acunetix Scanner allows you to integrate your scans into a CD/CD pipeline with automation service tools like Jenkins. Additionally, you can also integrate third-party issue tracking systems, like Jira, GitLab, and GitHub to streamline vulnerability management.
Pros:
- Designed specifically for application security
- Integrates with a large number of other tools such as OpenVAS
- Can detect and alert when misconfigurations are discovered
- Leverages automation to immediately stop threats and escalate issues based on the severity
Cons:
- Would like to see a trial version for testing
Price and trial. Starts at $4,500 for the Standard edition, and $7,000 for the Premium edition, both for up to five websites. The price is based on multi-year contracts.
6. Nmap and Zenmap
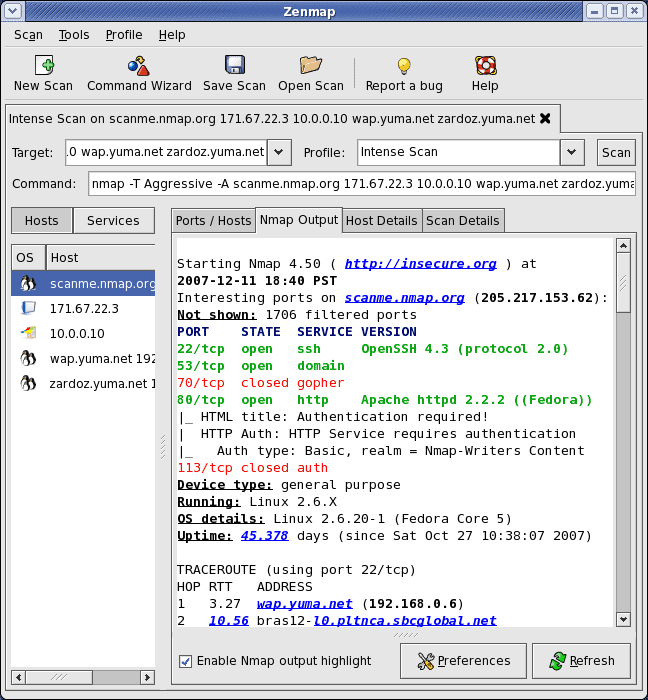
Nmap (Network Mapper) is a powerful CLI-based network mapper. It is the defacto standard for network mapping and port scanning. Nmap can discover hosts within a network by doing a ping sweep, find the services these hosts are offering, and identify their open ports. It can also discover the remote OS by using TCP/IP stack fingerprinting.
Key Features and New Nmap7.0 improvements:
- Better support for IPv6.
- New Nmap’s Scripting Engine comes with 171 new scripts and 20 libraries.
- Nsock for faster scanning.
- Improved scanning of TLS/SSL deployments.
Znmap is the GUI-version of Nmap (screenshot above). It is as powerful as Nmap but easier to use. It provides results in a graphical and simpler way.
Pros:
- Doubles as a security tool, allowing administrators to discover open ports, and applications communicating over ports that are suspicious
- A massive open-source community, Nmap is a very popular networking tool
- The syntax is straightforward and not difficult to learn for most users
Cons:
- Lacks a graphical user interface, however, Zenmap is available if needed
Nmap and Zenmap are free and open-source. Download from the official site.
7. Wireshark
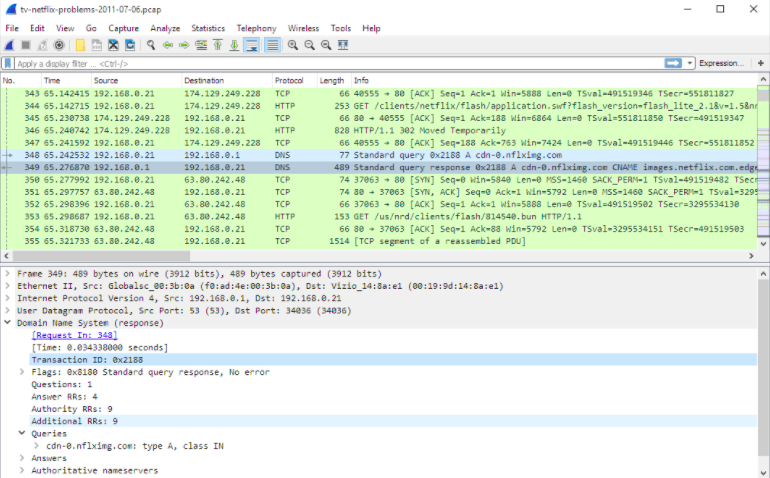
Wireshark, an award-winning network protocol analyzer, and one of the most preferred tools for network engineers, security experts, pen testers, and even hackers. Wireshark captures and analyzes network packets. It captures raw data, structures it according to the protocol, and filters it in the most detailed possible way.
Key Features:
- Live capture and offline traffic analysis.
- Powerful filtering
- Rich VoIP analysis.
- Export output XML, CSV, etc.
Pros:
- Features a large open-source community that continuously improves the tool
- Built by security professionals, for security professionals
- Can save captured packet data for further analysis – ideal for SIEM
Cons:
- Collects a massive amount of data that requires filtering – not the best option for novice users
Wireshark is free and open source. The download is available for Windows, Linux, macOS, Solaris, and FreeBSD.
8. Metasploit
Metasploit is considered the swiss army knife for hackers. It is a robust collection of hacking tools, modules, and plugins. Metasploit automates several phases of a penetration test— from information gathering, gaining access, maintaining access, and even evading detection.
Key Features:
- Integration with recon/scan tools like Nmap and Nessus.
- Access to databases with exploits and vulnerabilities.
- Meterpreter to set the payload.
- Exploitation and post-exploitation tools.
The Metasploit Project is one of the most popular pen testing and hacking frameworks. The project provides information about security vulnerabilities, helps with pen testing and the development of IDS signatures.
Pros:
- One of the most popular security frameworks in use today
- Has over of the largest communities – great for continuous support and up to date add ons
- Available for free as well as a paid commercial tool
- Highly customizable with many open-source applications
Cons:
- Metasploit caters to more technical users, not the best option for novice users
The Metasploit Framework (CLI) is free and open-source. The Metasploit Pro is a GUI-version of Metasploit with the same capabilities.
9. John the Ripper
John the Ripper (JtR) is an open-source password-cracking tool. JtR was initially designed to test the strength of passwords for UNIX-based systems, but now it is supported by many operating systems.
JTR is capable of cracking passwords using any of the following methods:
- Dictionary attack. Feed a list with a vast combination of words, phrases, and possible passcodes.
- Brute force: Provide parameters to help JTR with successful password guessing.
- Rainbow tables: Compares hashed passwords obtained from data leaks with plain-text passwords.
Pros:
- A simple tool for password hardening
- Is extremely lightweight – a great addition to security toolkits
- Allows sysadmin to identify weak passwords in their organization
Cons:
- Lacks a graphical interface for visual reporting
Price and trial. JtR is available in two versions, free (open source) and Pro version with additional capabilities like bigger dictionaries, multiple languages, optimized performance, and more.
10. Aircrack -ng
Aircrack -ng is the most popular suite of WiFi hacking tools. It works with a wide range of wireless NICs as long as they support raw monitor mode. Aircrack-ng is capable of capturing packets from 802.11a, 802.11b, and 802.11g WiFi standards and analyzing their hashes.
Aircrack -ng is armed with:
- Monitoring via a packet sniffer
- WEP and WPA/WPA2-PSK key cracker.
- Perform de-authentication, fake APs, and replay attacks.
- Capture and packet injection.
Pros:
- Focuses heavily on wireless security – great for routine audits or field pen tests
- One of the most widely supported wireless security tools
- Can audit wifi security as well as crack weak wireless encryption
Cons:
- Focuses exclusively on wireless security – not an all in one tool
Download Aircrack-ng for free.
11. Nessus
Nessus developed by Tenable is a powerful vulnerability scanner for infrastructures such as servers, network devices, databases, Operating Systems, and hypervisors. Nessus is capable of finding misconfigurations, default and weak passwords, and DoS risks. It is supported by Windows, Linux, and macOS.
Key Features:
- Reports in text, XML, and HTML.
- Integrates with Hydra THC to perform dictionary attacks and attempt to crack passwords.
- Scan patching levels on Windows computers.
- Support compliance audits.
Pros:
- Offers a free vulnerability assessment tool
- Simple, easy-to-learn interface
- Little configuration needed, 450+ templates that support a range of devices and network types
- Includes vulnerability prioritization
Cons:
- Offers limited remediation tools and options
- Could benefit from more integrations into other SIEM platforms
Price and trial. Nessus is available in a free limited version (download Essentials) and a full-featured paid subscription version (Professional for one year for €3.036,34).
12. Kali Linux
Kali Linux is more than a tool; it is an entire Linux distribution— derived from Debian and designed for penetration testing, ethical hacking, reverse engineering, vulnerability assessment, and advanced forensics.
Key Features:
- Customizable Kali Linux ISO images.
- Kai live mode (image) to test pen tester skills.
- Kali includes more than +600 pen-testing tools.
- Integration with other robust tools like Wireshark and Metasploit.
Kali Linux gives you access to a long list with more than 600 tools, for information gathering, vulnerability analysis, brute-force password cracking, wireless attacks, spoofing, sniffing, and a lot more.
Pros:
- An entire operating system and platform focused on offensive security
- Heavily documented
- Large supportive community
- Includes over 600 tools
Cons:
- Not ideal for automated or continuous testing
Download: Kali Linux is a free and open-source project. Download an image at Kali’s official site.
Six Worthy Mentions
Below are six additional pen-testing tools also loved by security experts.
- BeEF The Browser Exploitation Framework (BeEF) was designed to hook (take control of) web browsers, and launch attacks from there.
- W3af Web application audit and attack framework (W3af) is an open-source Web application security scanner.
- THC Hydra. A fast online password and network logon cracking tool. It can perform dictionary attacks over protocols like FTP, HTTP, HTTPS, SMB, and many more.
- Maltego. A robust tool for graphical link analysis, used for forensics and intelligence gathering. Maltego lets you mine data from open-source and distributed sources and compile it into a graph.
- SQL Map A powerful open-source penetration tool used for detecting and executing SQL injections and taking control of databases.
- Nikto An open-source web scanner for web servers. It tests servers against 6700 potentially dangerous files and programs. It also identifies outdated and problems with specific server versions.
Conclusion
The ten tools in this post cover all the required steps to perform a solid penetration test. Nmap to scan for open ports and map the network, Wireshark to analyze packets, and John the Ripper to crack passwords and gain access. Other tools like Metasploit use pre-packaged exploits to automate several phases. Similarly, Aircrack-ng for several wireless pen test phases.
Automatic security assessment tools such as Invicti, Acunetix, Intruder, and Nessus can help assess either external networks like web applications, websites, and APIs and internal networks such as computers, network devices, etc.