Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
The Best Cloud Workload Security Platforms
UPDATED: December 12, 2023
A virtual server instance in a cloud computing environment is referred to as a cloud workload. Cloud workload protection platforms are responsible for ensuring the security of key workloads across multiple cloud platforms. The need for public cloud services is always growing. Most platforms safeguard their own infrastructure to a large extent.
As an outcome, other cloud data vulnerabilities are overlooked. Securing sensitive data and conducting regular compliance audits are both essential. As a result, it is critical to know which cloud security platforms are the best.
Here are a few of the greatest cloud workload security platforms available today. Using a variety of factors, we feel the following cloud security providers can considerably reduce the risk of attacks on your infrastructure.
Here is our list of the best Cloud Workload Security Platforms:
- Datadog Cloud Workload Security Cloud Security for Workloads Identifying and addressing vulnerabilities in your cloud workload across hosts, containers, and kernels is the goal of this tool.
- McAfee Cloud Workload Security Using this platform, you can monitor and secure your whole cloud environment, as well as your on-premises infrastructure.
- CloudGuard Workload Security A cloud-native security solution that provides unified visibility and threat prevention across all your cloud resources.
- Trend Micro A cloud security platform that covers all bases. It also grows with your business and helps you stay on top of regulatory requirements.
- Azure Security monitoring and management for physical servers, virtual machines, and other cloud resources is made easy with Microsoft Azure Security Center.
- VMware VMware's cloud workload protection solution is small and simple to use.
- Prisma Cloud Using this cloud-based security solution, you can monitor and defend all of your cloud resources.
- Armor Anywhere Superior cloud security capabilities have eased the burden somewhat, with this one software.
- Kaspersky Hybrid Cloud Security For virtual desktops and Windows or Linux servers, it is a good option. All physical computers, virtualized workloads, on-premise, in a data center or cloud, are protected against cyber-attacks with the Next Generation protection.
- Lacework Cloud Security Platform A cloud security solution that provides both security and compliance. It's faster to get up and running and allows organizations to automate the scaling of their workloads.
The best Cloud Workload Security Platforms
1. Datadog Cloud Workload Security
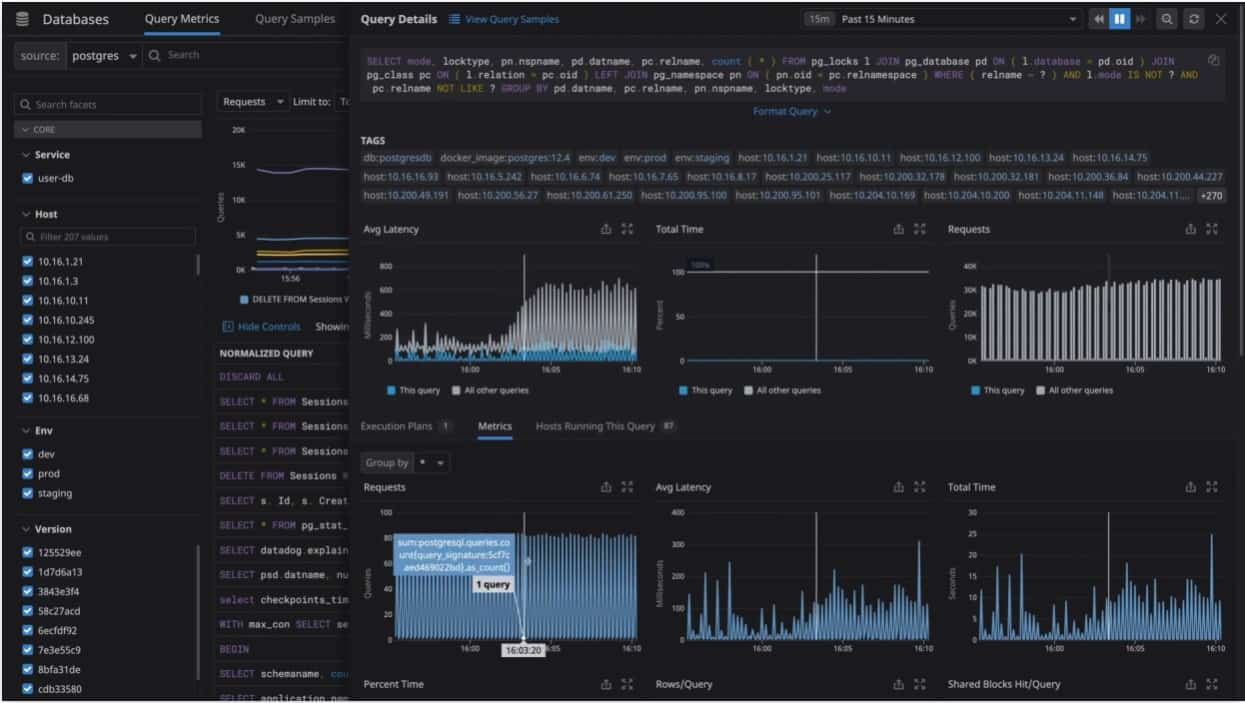
A well-known cloud application security platform with extensive observability is Datadog's Cloud Workload Security Platform. It is faster than other security solutions at detecting, monitoring, and responding to possible threats, and it supports more than 500 integrations. All operational and security logs are accessible through its features. It's easy to scale up and down the security tool.
Key Features:
- Allows for complete user experience monitoring.
- Threat detection in real-time.
- Controlling the devices and containers connected to a network.
- Workload activities are monitored in great detail.
- Datadog may be set up in a matter of minutes.
- File Integrity Monitoring (FIM) with Datadog Support (FIM).
- Adaptable and provides a wide range of options.
Manage workloads, monitor files and kernel operations, and the trade-off between visibility with Datadog's Cloud Workload Security. Track all incoming threats to production workloads in real-time with Datadog. DevOps and Security teams can also use better reporting and deeper insights to tackle a variety of cybersecurity issues.
The Datadog Agents have been merged, thus no additional resources or new agents are required. Detecting threats that already exist in cloud instances and containers are perfect for this platform.
2. McAfee Cloud Workload Security
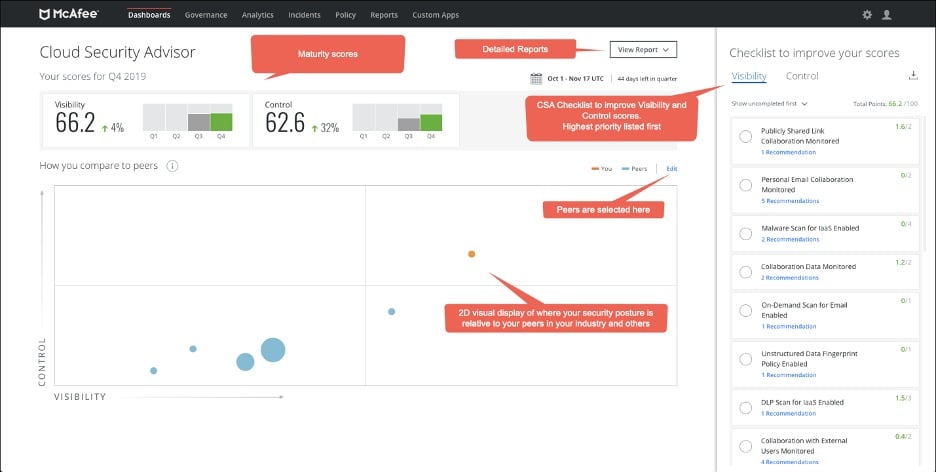
One of the most widely used security platforms for hybrid cloud environments is the McAfee Cloud Workload Security Platform. Security and workload management are handled from on-premises to cloud end-to-end. It eliminates blind spots, provides enhanced threat defense, and simplifies multi-cloud management by automating the detection and defense of elastic workloads and containers.
Key Features:
- Discovery is automated.
- Streamlined Organizational Structure.
- Allows for easy integration with other systems.
- Advanced security measures are employed.
Cloud security management is made easier by this platform. Additionally, it automates workloads and offers contextual information for debugging, making it easier to find the root cause of issues. One-click quarantine and a unified dashboard allow you to set security policies across your physical, virtual, and hybrid cloud environments.
Machine learning, VM-tailored malware, file integrity monitoring, and micro-segmentation are just some of the ways that McAfee utilizes to keep your workload safe. The data center's enhanced threat protection can fend off threats from the outside as well as from within. For virtual instances, it also makes use of workload techniques based on the computer hosting the workload. As a result, any problems with the underlying infrastructure are avoided.
There are various cloud providers that McAfee works with, including Amazon Web Services (AWS), Microsoft Azure (Microsoft), and VMware environments. Chef and shell scripts are also supported for deployment. All of this makes your McAfee platform more customized and extendable for you.
Overall, McAfee's cloud, physical, and hybrid environment security features are among the most advanced available. Its user-friendly interface and easy-to-use management make it a popular choice.
3. CloudGuard Workload Security
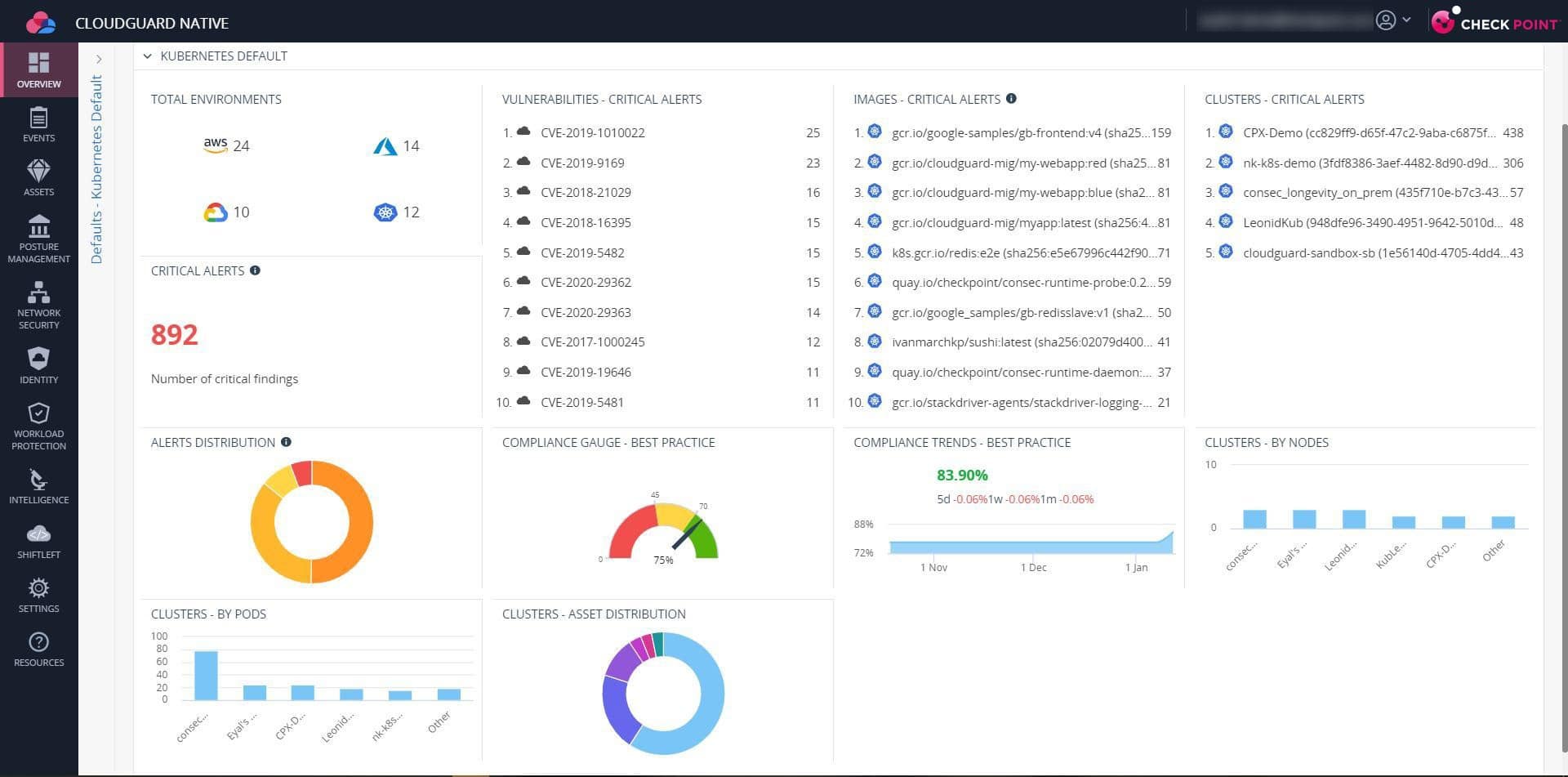
An automated cloud-native workload solution, CloudGuard provides uniform visibility across your cloud infrastructure. It has built-in security features and is fully compliant with all regulations.
Key Features:
- Automatic Security.
- Control of Posture.
- Protection of a Large Workload.
- Comprehensive Reporting.
With CloudGuard Workload Protection, you can be assured that your applications' performance measurements are always in sync with the predefined baselines. An automated cloud-native security solution protects containers and cloud apps.
As a result, all potential dangers are effectively neutralized at the cloud layer level. This allows security and DevOps teams to take a zero-trust approach to this platform. This strategy is certain to boost safety and compliance.
CloudGuard provides comprehensive protection for running workloads. Profiles and monitors the behavior of applications and functions. Additionally, it compares the functionality and data to set baseline values to look for anomalies.
4. Trend Micro Security for Workloads
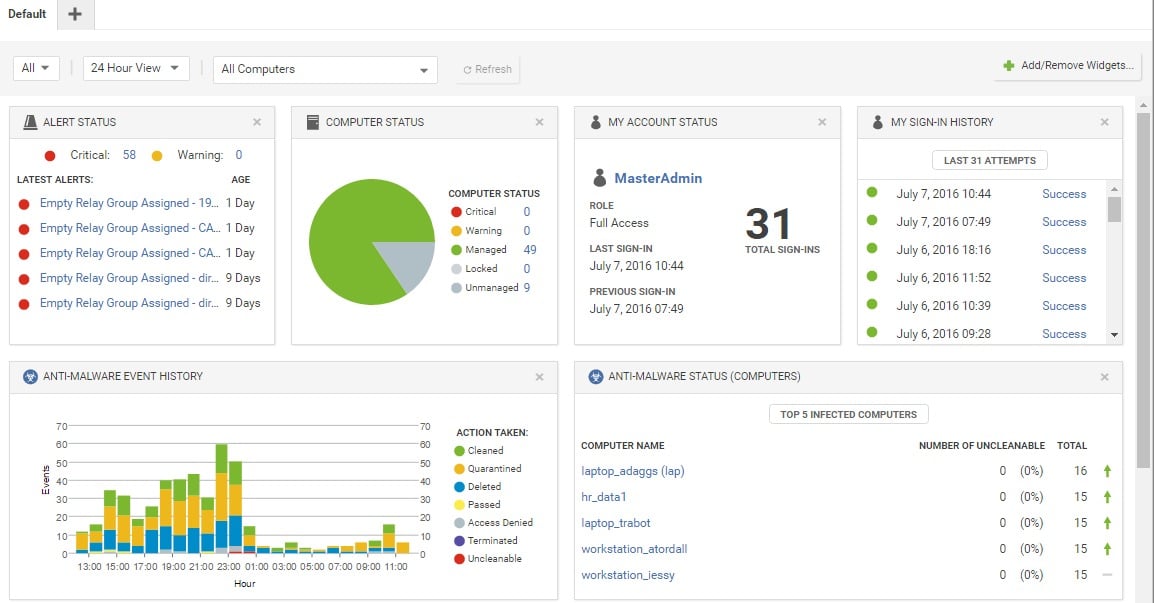
Another well-known Cloud Workload Security Platform, Trend Micro Deep Security, has a comprehensive set of services to assist protect cloud workloads. Malware and other risks are easily detected and avoided with the help of this effective solution. In addition, its extensive security measures and application management capabilities prohibit any illegal software modifications.
Key Features:
- An examination of behavior and a sandbox.
- Offers context-aware, proactive defense against threats.
- Constantly revised regulations.
- Anti-malware and IPS protections are included.
- Capabilities for application control.
- Improved vulnerability detection and protection.
Integrity monitoring, web reputation service, firewall, behavioral analysis, and sandbox analysis are also supported by Trend Micro Deep Security. DevOps methods may be easily integrated into this application, making it a popular choice among developers. Machine learning and Virtual Patching algorithms used by the security solution enable instance-based protection for new and existing workloads.
Faster incident response and actionable information are provided by Deep Security's easy dashboard. It also ensures that all cloud and container environments are protected by the same level of security.
5. Azure
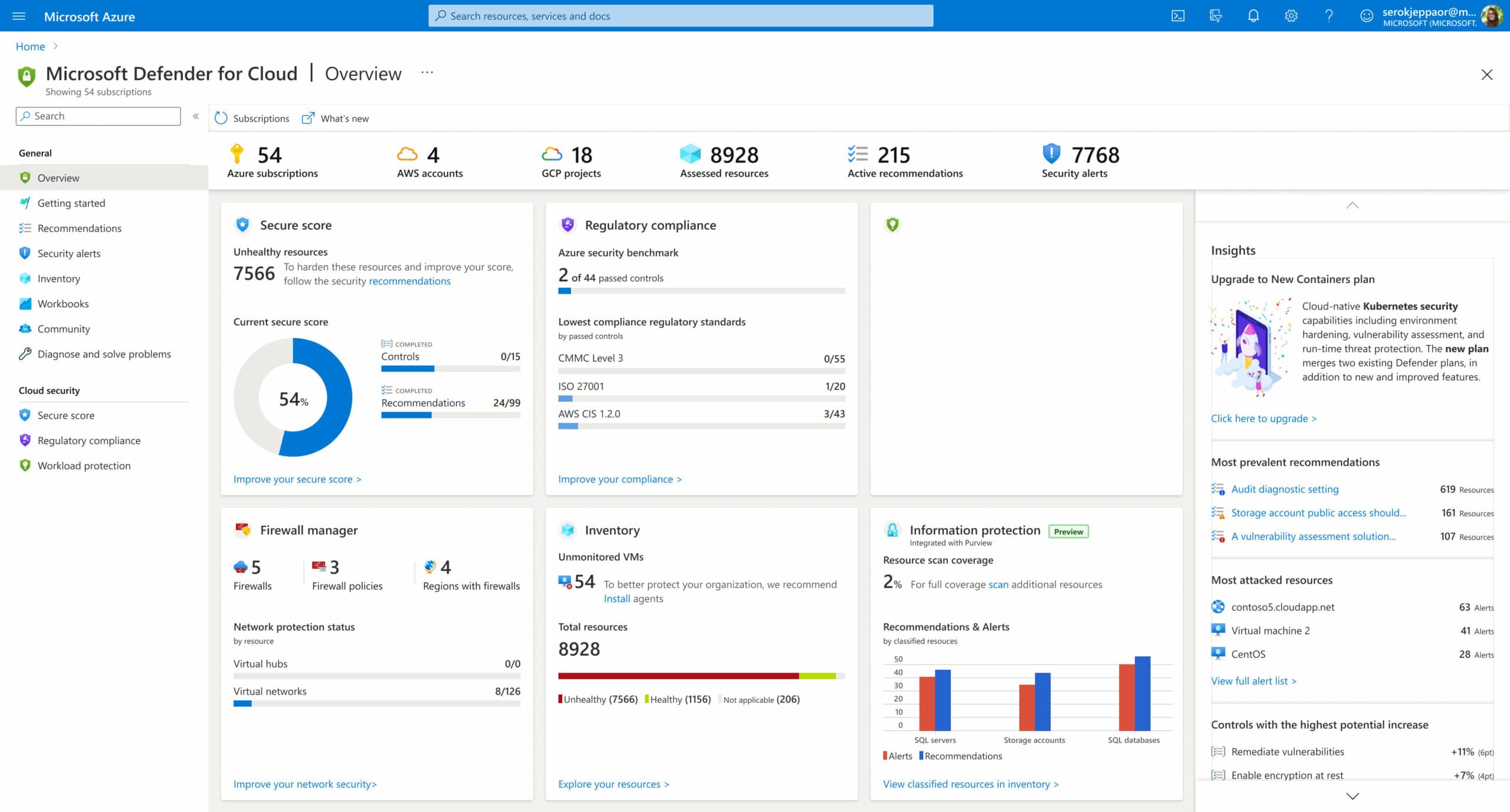
Many well-known enterprises rely on Microsoft Azure Security Center to keep tabs on the safety of their physical servers, virtual machines, and other cloud resources. Vulnerability scanning and Access/Application Control support are all features of this widely used security tool (AAC).
Key Features:
- Identification of potential weak points or openings.
- There must be complete threat prevention for all workloads in various contexts.
- Ensure compliance with applicable laws and regulations.
- Consistent monitoring of the amount of work being done.
- Provides ongoing evaluation of the security of cloud resources.
- Offers useful information.
- Simplifies security management by utilizing a single console.
The primary goal of the Microsoft Azure Security Center is to safeguard cloud data centers from a wide range of potential dangers. It also works with hybrid clouds and simplifies security management by providing a single point of control.
Microsoft's Azure Security Center is a great option for workload security while shifting to the cloud because it delivers actionable insights, alerts in the event of suspicious activity, and threat avoidance recommendations.
6. VMware
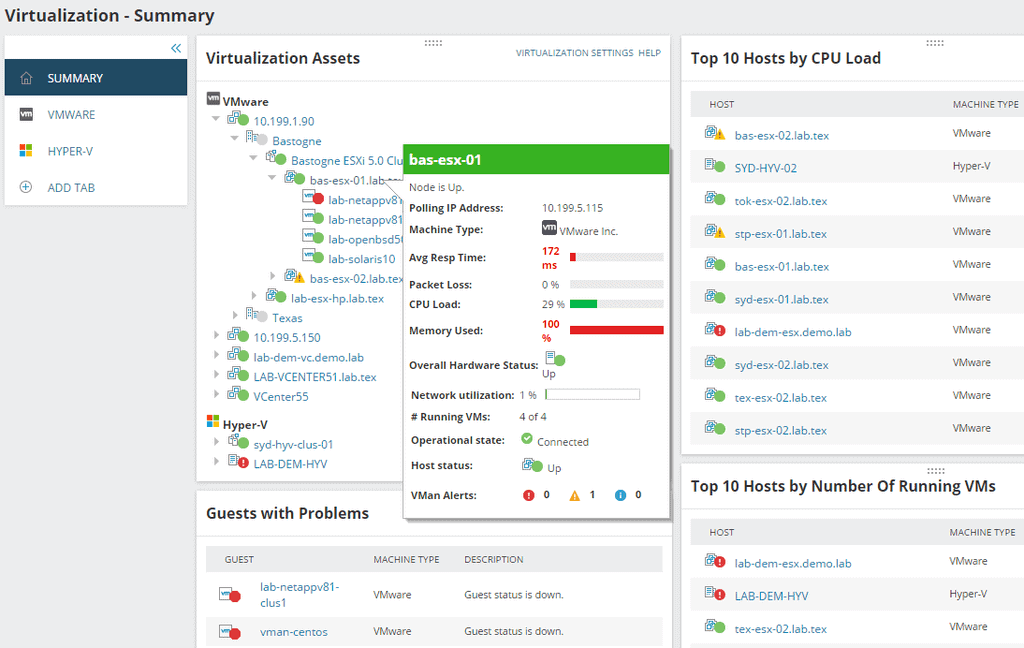
Using VMware's cloud workload protection technology is a simple process. VMware AppDefense encrypts workload-to-workload data while it is in transit. The platform allows for the setting of particular workloads and the handling of any vulnerabilities that may arise.
Key Features:
- Total awareness of all tasks and their statuses
- Nearly limitless configuration options
- Separate the assault surface from the controls
- Simplicity of operation
Some more notable platforms that qualify as good cloud workload protection services, in addition to the top 10, are included below. A cloud workload protection platform should be considered sooner rather than later.
It is possible that your cloud service provider does not cover all aspects of the security of your cloud workloads. The security features included in various cloud service models differ. To access more advanced workload protection features, some companies may provide premium tools, software, and policies in addition to their standard offerings.
Make your data more secure and take back control of the cloud to protect yourself from both internal and external threats and cyber-attacks. Using the latest threat intelligence, VMware Workload Protection enhances company agility and decision-making.
7. Prisma Cloud
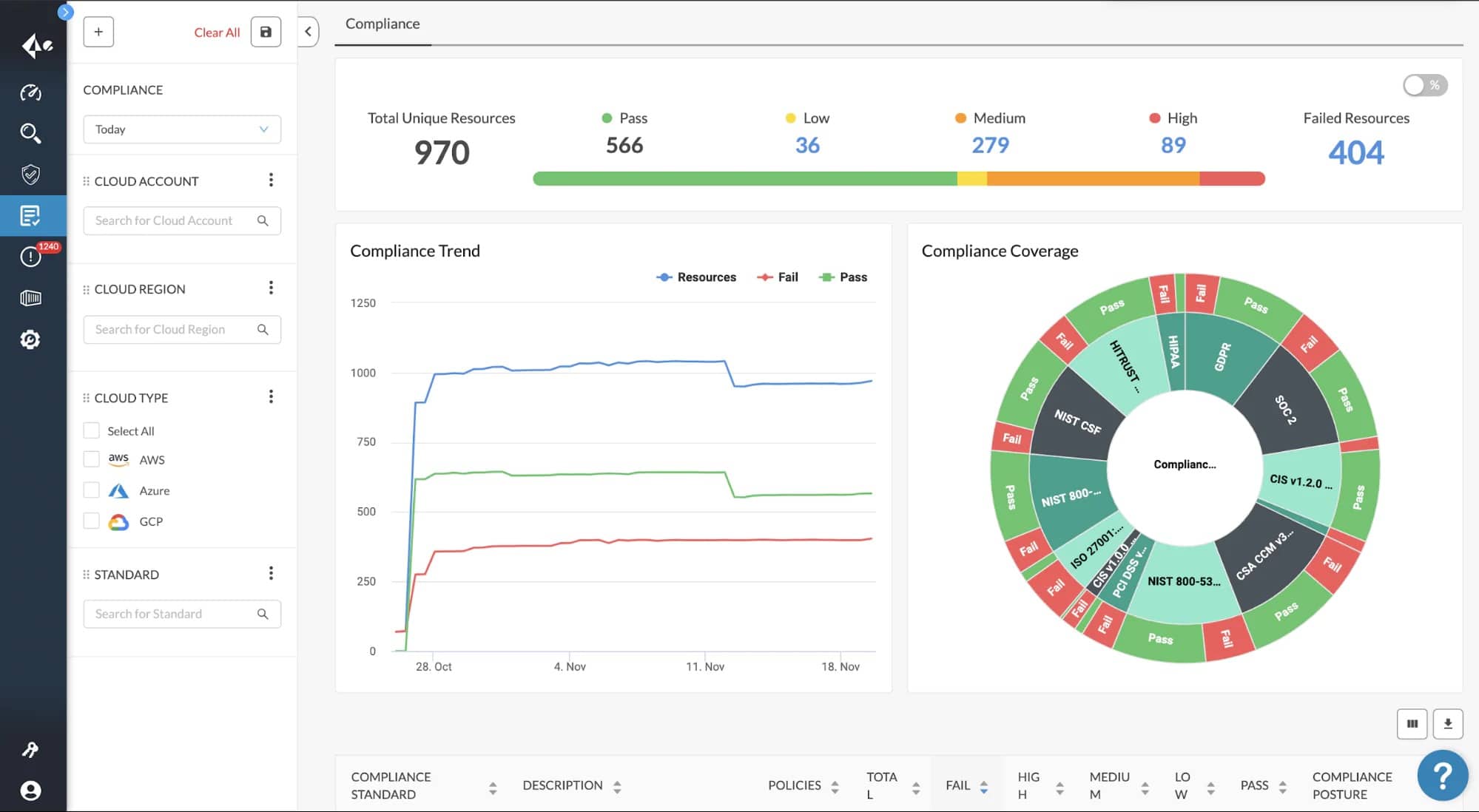
It is possible to use Prisma Cloud on any cloud, including Azure and Google Cloud, and have complete protection during the entire development lifecycle. In addition, a new functionality called container image sandboxing is also available. You can inspect all the files and pre-deployment network activities with this functionality.
Key Features:
- In terms of security and visibility, Prisma Cloud is unrivaled.
- Scanners for the Exfiltration of Network Data.
- Scans IaC templates for vulnerabilities.
- Allows the monitoring of public cloud storage for malicious code.
- Provides runtime protection for the entire stack.
- Monitoring of user and entity behavior.
- Enforces rules of governance.
Another benefit of adopting Prisma cloud is that it eliminates all cloud blind spots and alleviates the load of alert fatigue. Cloud workload protection platforms that provide network visibility, container security, API security, full-stack runtime protection, user and entity behavior monitoring services, and more are becoming increasingly important as more enterprises migrate to the cloud.
Continuous vulnerability management and compliance are key features of the most effective CWPPs in multi- and hybrid-cloud settings. For a holistic picture of cloud risk, it dynamically finds changes in cloud resource configurations and continuously correlates siloed raw data sources such as user activity, resource configuration, network traffic, threat intelligence, and vulnerability feeds.
8. Armor Anywhere
Moving workloads to the cloud typically raises several concerns including privacy, the integrity of data, and regulatory compliance. On the other hand, the cloud security capabilities of Armor Anywhere have helped to alleviate some of the strain.
Key Features:
- Detection of intrusions.
- Monitoring of the integrity of files.
- Protects against malicious software.
- It has a patch monitoring system in place.
- Scalability and rapid deployment.
- Alert activity is tracked and monitored.
- The ability to see and manage everything from a single location.
- Data security and monitoring.
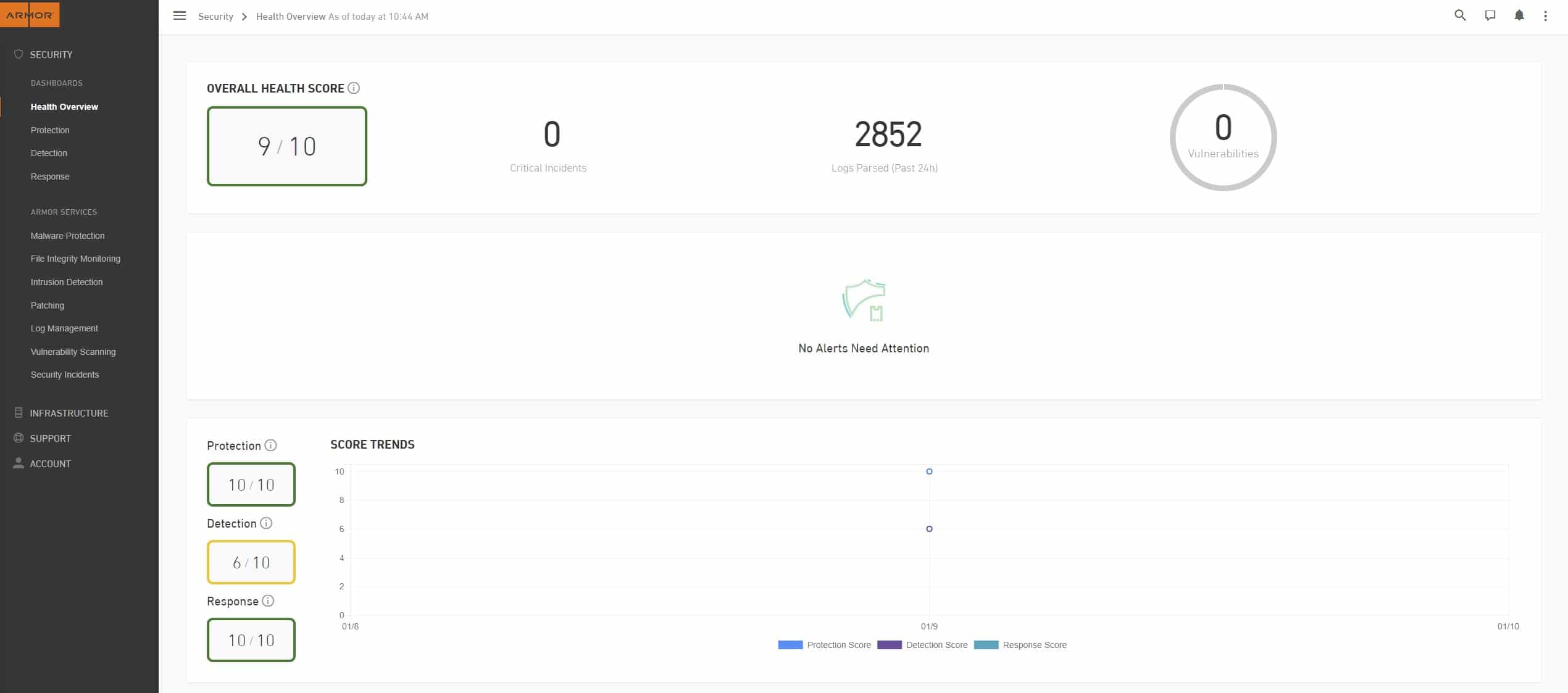
All-time incident response and threat detection are all part of Armor Anywhere's CWPP service. It defends your data centers against cyber-attacks, monitors alert activity, and immediately responds and remediates the situation.
Additionally, it aids in the storage of agent records for 30 days and performs thorough system checks for improved visibility. You can get assistance at any time of the day or night by contacting the well-equipped Security Operations Center (SOC). IT infrastructure data logs and vulnerabilities, as well as threats and health scores are all shown on the dashboard.
Intrusion Prevention, Policy Recommendation Scans, and the ability to toggle security measures on and off are just a few of the new additions. It's been used by a wide range of businesses, allowing them to meet their security requirements.
9. Kaspersky Hybrid Cloud Security
For virtual desktops and Windows and Linux servers, Kaspersky Hybrid Cloud Security was created. For all physical machines, virtualized workloads (in a data center or the cloud), delivers Next Generation protection against cyber-attacks. Today, cloud data security is critical to a company's long-term viability. For this reason, Kaspersky was developed to safeguard corporate data and the digital transition it was undergoing.
Key Features:
- The provisioning of VDI computers is supported.
- Protection against threats in the next generation.
- Security for Linux and Windows Servers with Light Agent.
- All environments are protected by a multi-layered approach.
- For deep visibility, it has a unified orchestration console.
- AWS and Microsoft Azure infrastructures are better protected with this new technology.
The Kaspersky Security Cloud is an all-encompassing protection solution that can be installed on every device you own. It is compatible with all of the major operating systems, such as Windows, iOS, macOS, and Android, and it comes with a wide variety of innovative security tools and technologies, some of which can adapt to your needs in real-time to ensure that you are protected around the clock.
In the cloud, Kaspersky provides continuous security and multi-layered protection. Using Kaspersky, you can ensure the safety of all of your data. In each case, the security tool provides the same level of protection, flexibility, and visibility to users, regardless of where your workloads are operating.
10. Lacework Cloud Security Platform
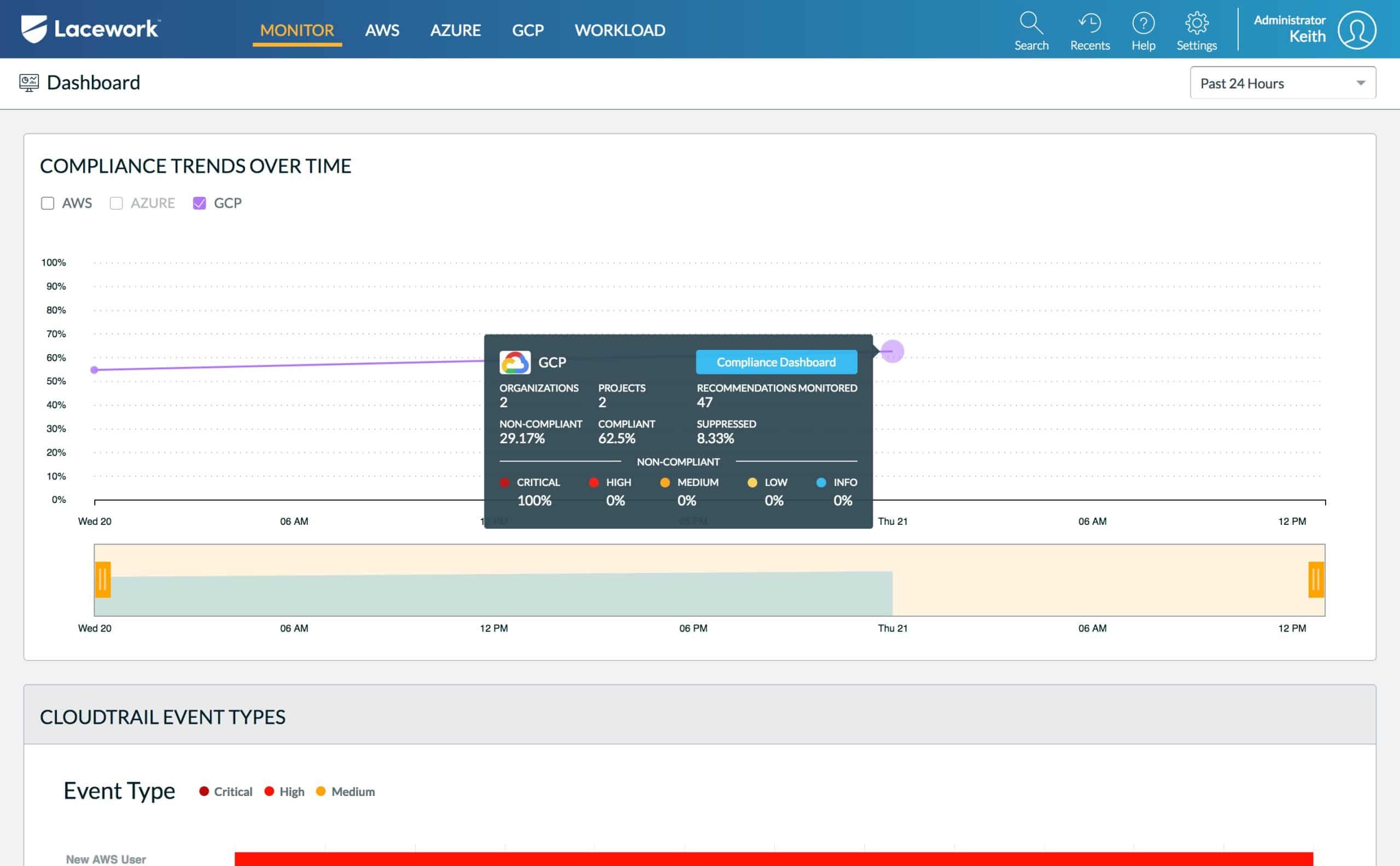
The Lacework Cloud Security Platform provides both cloud security and cloud compliance. Faster deployment and the ability to scale workloads automatically are two of its many benefits. It's simple for programmers to apply machine learning to find, detect, and monitor risks and vulnerabilities in the system.
Key Features:
- Offers a wealth of new information.
- Management of vulnerabilities.
- Has the ability to identify issues with network settings and unexpected behavior.
- Provides comprehensive end-to-end insight.
- Analysis of container and cloud-based workload.
- Configuration monitoring and auditing.
- AWS Security Monitoring with Autonomous AWS.
- All surroundings can be investigated graphically using these tools.
Cloud workload protection platform Lacework has simple principles for operation and maintenance. Contextual data on the latest upgrades, faults, or changes to the configuration is provided by the security tool, which provides deep visibility. Various public clouds, such as Microsoft Azure and Amazon Web Services, are also supported.
There is a lack of vendor support for multi and hybrid cloud computing workloads. Lacework was created to detect security breaches in real-time across all processes, workloads, users, apps, and data centers, and it has proven to be an invaluable tool.
Editor’s Choice
If you're concerned about zero-day and other risks to your cloud infrastructure, a cloud workload security platform is an excellent choice. For compliance and auditing purposes, several of these platforms even include full reporting. These solutions, of course, constantly monitor your cloud infrastructure and give alarms along with context for easy troubleshooting.
Datadog is our first choice from this list as it is a solution that offers a comprehensive approach to the task of collecting, searching, and analyzing traces across fully distributed infrastructures. Because it can automatically trace requests across a wide variety of well-known libraries and frameworks, using it is as easy as adding a client library to your project.



