Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
The Best Attack Surface Monitoring Tools
UPDATED: September 21, 2023
Monitor the external surface of your assets and squash vulnerabilities before they become an issue.
With new advances in technology comes new methods for hackers to take advantage of prior technology, so staying ahead of the curve is a vital part of keeping your business secure. While your internal security is vital, protecting your external security means blocking threats before they can exploit any hidden vulnerabilities.
Here is our list of the best attack surface monitoring tools:
- Intruder – EDITOR’S CHOICE A cloud-based service that is accessed off a website and offers monthly or continuous attack surface scanning, internal vulnerability scanning, and dynamic application security testing for Web applications and APIs. Access a 14-day free trial.
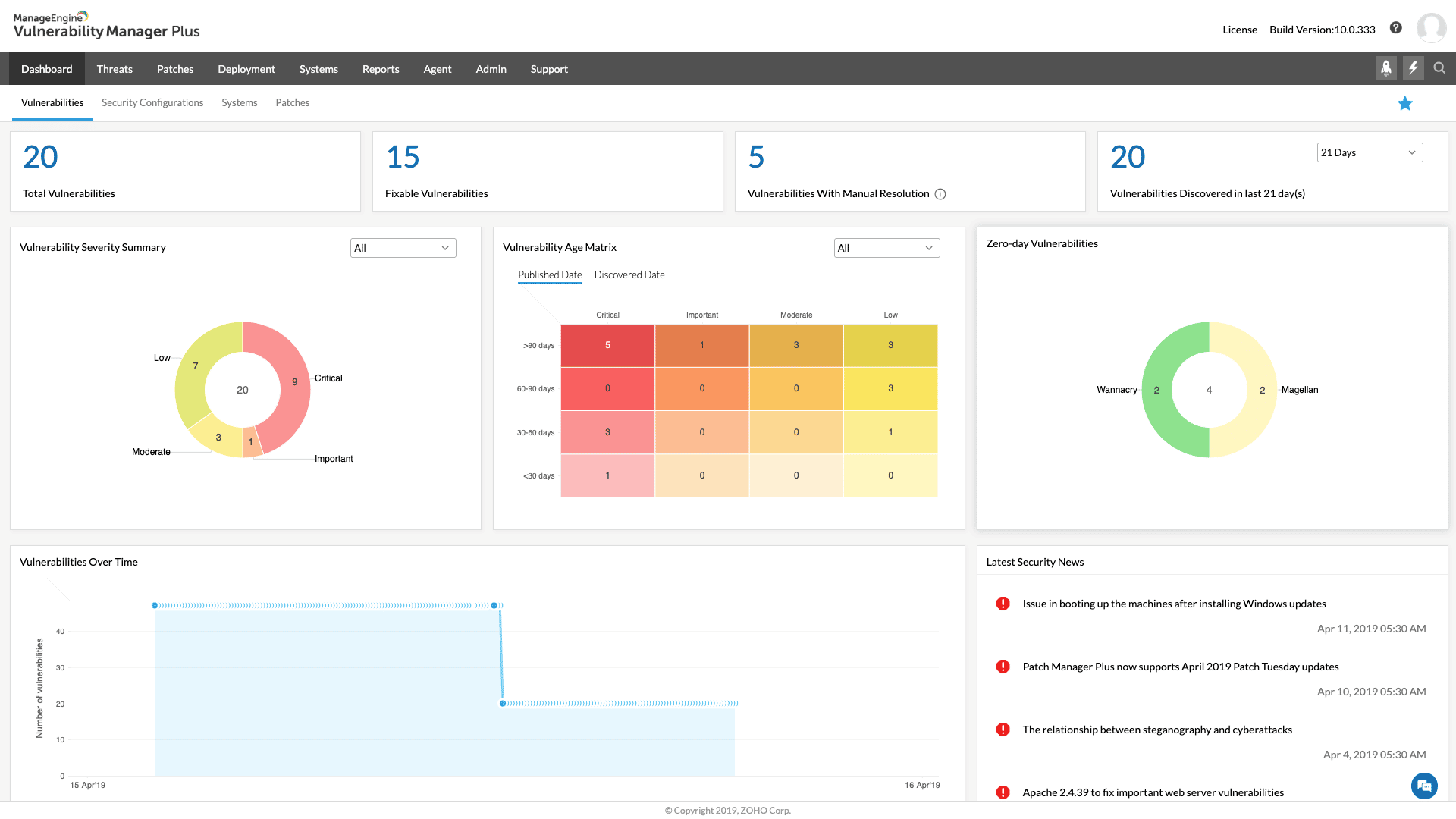
- ManageEngine Vulnerability Manager Plus – FREE TRIAL Aids companies in locating and repairing any flaws in their devices and network. Get a 30-day free trial.
- Rapid7 InsightVM By utilizing an impressive body of security research, Rapid7 presents a phenomenal attack surface monitoring tool that can cover cloud, on-prem, and third-party detection.
- ImmuniWeb Discovery Enterprise-scale threat analysis and surface monitoring tools are presented as a package that focuses on data breach prevention and web monitoring.
- CoalFire Attack Surface Management This attack surface monitoring tool provides fantastic automation and guidance-based support for easy remediation.
- Burp Suite Enterprise Enterprise-scale attack surface monitoring constantly scans the web and your third-party connections for any threats.
- UpGuard BreachSight This solution is focused on simplifying the task of attack surface monitoring by abstracting reams of data into actionable information.
- Bugcrowd Crowdsourced, human-driven attack surface monitoring, is achieved by partnering you with white-hat hackers that do the hard work for you.
- CyCognito Cloud-based security platform that includes several impressive vulnerability detections and attack surface monitoring tools.
- Digital Shadows SearchLight Cyber threat analysis and dark web searching for attack surface monitoring, are all presented in readable form with prioritized remediation goals.
There are several ways to keep your external security tightened, but to even approach the problem of external security, you need to know exactly what your external assets are, and what they look like, to any outsiders. This is where attack surface monitoring tools step in—by effectively producing a ‘map’ of your external surface and identifying any holes that need filling.
There are several attack surface monitoring tools, and this article goes over just nine of them. Attack surface monitoring tools come in a mixture of automated software-driven tools, and human-driven reporting tools—the best attack surface monitoring tools combine elements of both of these approaches.
- Software-driven tools provide instant and perpetual scanning and collect vast amounts of data outside the capabilities of a human team.
- Meanwhile, human-driven tools provide the personalized touch with human-readable reports that take advantage of a human’s ability to spot vulnerabilities that automation overlooks.
Another critical aspect of attack surface monitoring tools is third-party scanning. By non-intrusively performing checks on your third-party connections, these tools can identify threads that take advantage of the tools and services you rely on, to help you make informed decisions about which third-party tools to use.
The best attack surface monitoring tools
This article discusses the top tools with various feature-set and costs. Each of them tends to focus on one particular aspect of attack surface monitoring; such as web monitoring, detection automation; or simplifying data into readable information. Take the time to think about what features you would need for your business, then check out the products that fit the bill—possibly by trying out one of the free trials.
1. Intruder – FREE TRIAL
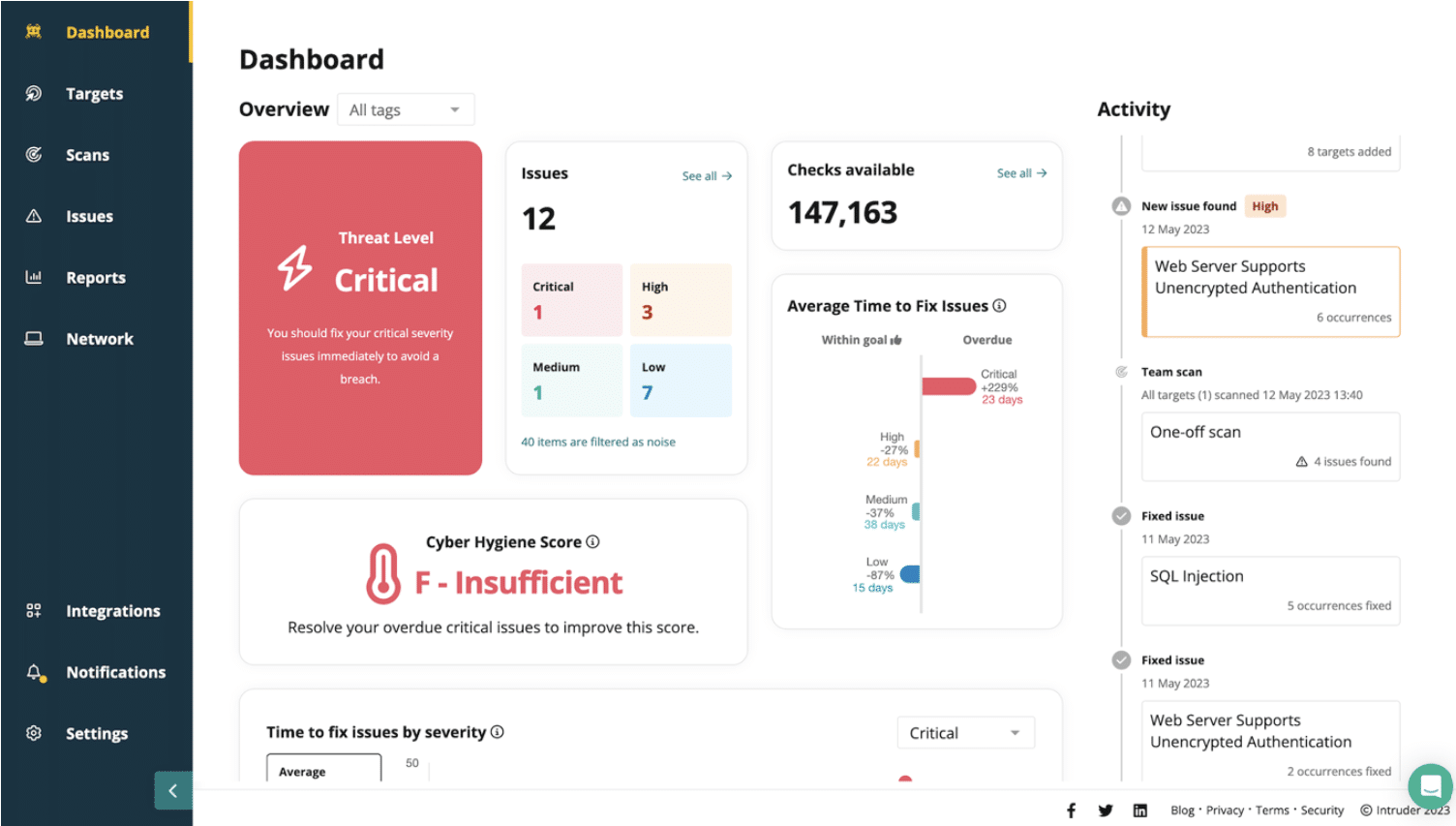
Intruder provides attack surface monitoring by continuously scanning your network, automatically kicking off vulnerability scans when it detects changes in your environment or when it learns about an emerging threat.
Key Features:
- Monthly, frequent, continuous, or on demand
- Network vulnerability scanning
- Integrations with project planning tools
- DAST for Web applications and APIs
- AWS, Azure, and GCP integrations
The two higher plans offer Tenable from the Intruder platform. This provides scheduled and on-demand attack surface scanning and also internal vulnerability scanning.
You can add dynamic application security testing (DAST) to any edition and that will scan Web applications and APIs. This tool can be integrated into a CI/CD pipeline for use by DevOps teams.
Pros:
- Integrates with collaboration systems, such as Teams and Slack
- CI/CD pipeline integration for DevSecOps services
- Risk reporting for compliance proof
- DAST instances add-ons
- Choose your scanning frequency
Cons:
- More comprehensive features available only on higher level plans
The attack surface scanner is the most straightforward service of the Intruder platform. It doesn’t require any installation and you access the dashboard through the Intruder website. Examine the service with a 14-day free trial.
EDITOR'S CHOICE
Intruder is our top pick for an attack surface monitoring tool because it is very accessible for small businesses. Get the Essential edition for a monthly scan and ensure that your system is properly configured to keep out hackers. Ramp up to the higher plans to get a Tenable service with regular scans on a schedule or an on-demand scanning utility. Those higher plans also give you internal vulnerability scanning and you can add DAST to any plan.
Download: Get a 14-day FREE Trial
Official Site: https://portal.intruder.io/free_trial
OS: Cloud-based
2. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus employs vulnerability scanning to find possible flaws, such as outdated patches or unsafe setups and then presents comprehensive reports on the findings.
Asset management, patch management, and compliance reporting are additional capabilities of Vulnerability Manager Plus that aid enterprises in maintaining the security of their IT infrastructure.
Additionally, the program offers remedial recommendations, including detailed instructions and connections to pertinent resources, to assist companies in addressing vulnerabilities that have been detected.
In general, Vulnerability Manager Plus may assist businesses in proactively identifying and addressing any security gaps, enhancing network and device security as a whole.
Key Features
- Automated remediation
- Detailed compliance reporting
- Integrated asset management
Pros:
- Excellent for continual scanning and patching throughout the life of any device
- Robust reporting can help demonstrate changes following correction
- Runs on Windows, Linux, and Mac
- The most recent threats and vulnerabilities are continuously updated in the backend threat intelligence
- Has a free version, which is excellent for small firms
Cons:
- The ManageEngine ecosystem can take time to explore fully
You can download ManageEngine Vulnerability Manager Plus completely free through a 30-day free trial with all features.
3. Rapid7 InsightVM
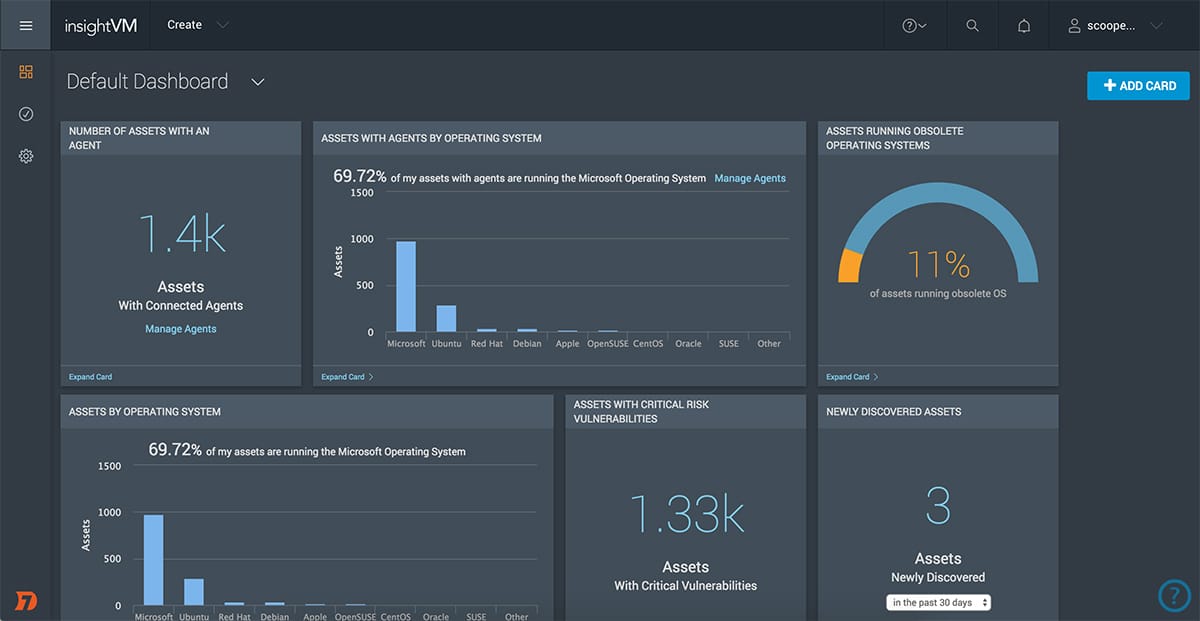
Rapid7 InsightVM is one of the best surface attack monitoring tools on the market, a feat achieved by combining the comprehensive security research and testing performed across Rapid7’s catalog of security-focussed products. Building the best security tools requires a bed of security data to pull from, one that is constantly kept up to date to stay ahead of the curve; and InsightVM meets this demand superbly.
Key Features:
- Cloud/virtual support
- Customizable dashboards with deep insights
- Policy assessment and risk prioritization
- Goals and SLAs
- RESTful API
The system uses a lightweight distributed agent and can be expanded to cover cloud and virtual environments for full security monitoring. Customizable dashboards can feed you important information on the fly, while insight metrics can provide vital data for vulnerability management and better accountability.
In addition to the vast bed of collected security data, InsightVM also shines in the sheer quantity of available integrations. As standard, it can be integrated into over 40 major technology platforms. The inbuilt open RESTful API can also be used to further expand your integration options for maximum security coverage.
InsightVM has a free trial available on the website, as well as a full demo of the software. The product itself is priced based on the number of required assets. For example, 500 assets cost around $1.84/month, but the exact cost will be quoted based on your needs.
4. ImmuniWeb Discovery
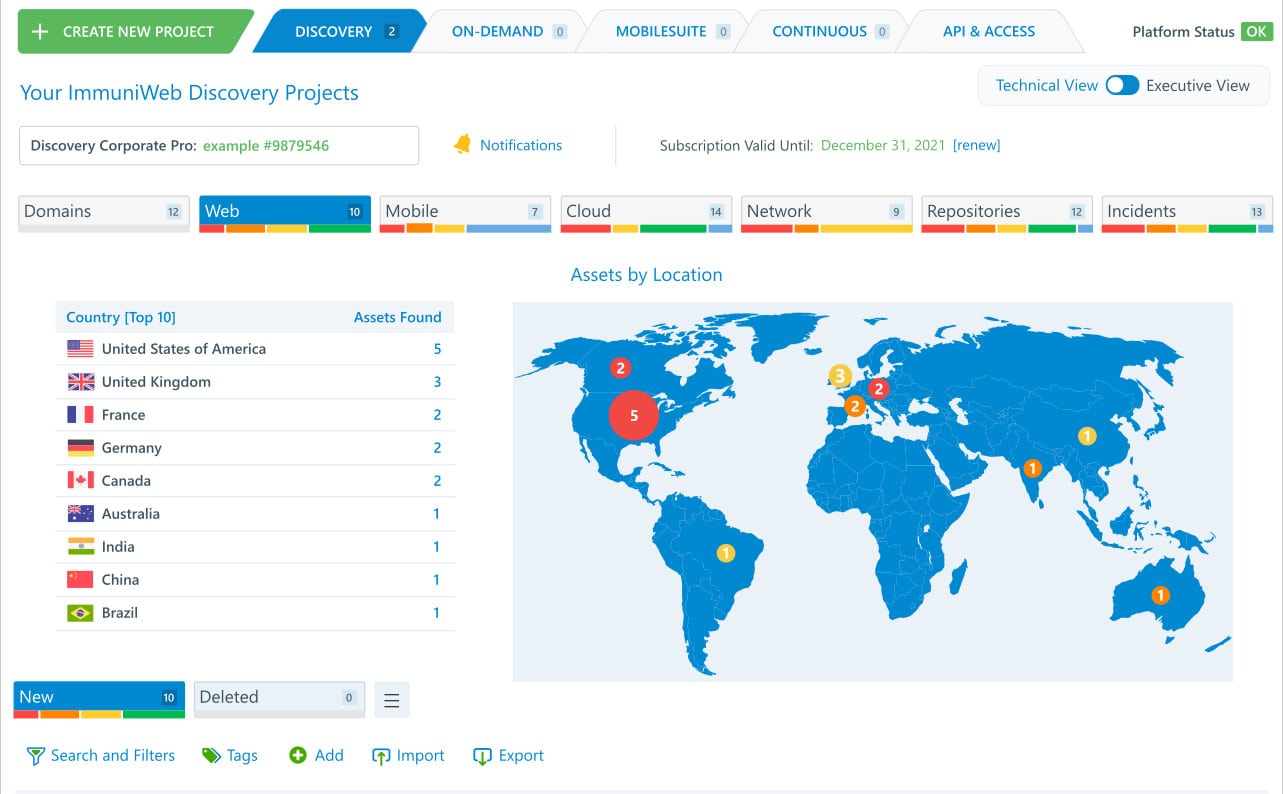
ImmuniWeb Discovery provides substantial threat analysis and surface monitoring tools and has a particular focus on data breach prevention and web monitoring. It uses OSINT, combined with its AI-driven detection systems to monitor your attack surface through the surface, deep, and dark web. The tool can scan for abandoned or forgotten assets, and boasts instant alerting when vulnerabilities emerge.
Key Features:
- AI-driven OSINT surface monitoring
- Cloud and on-prem analysis
- Instant alerting
- Deep/dark web vulnerability scanning
- Third-party scanning
ImmuniWeb is built from the ground up as an enterprise-scale solution, with a globally reaching scope—while this means the solution is on the pricer side, it also means consistent quality and scalability. Since the system relies on OSINT and is focused on external web threat analysis, it doesn’t require an agent deployment or on-prem support.
The product is broken down into annual subscription packages that range from the Express Pro package which costs around $499 per month, to the Ultimate package which costs $3995 per month. The real draw of the product is the cyber threat analysis which includes deep/dark web detection, but that is only available in the more expensive packages.
5. CoalFire Attack Surface Management
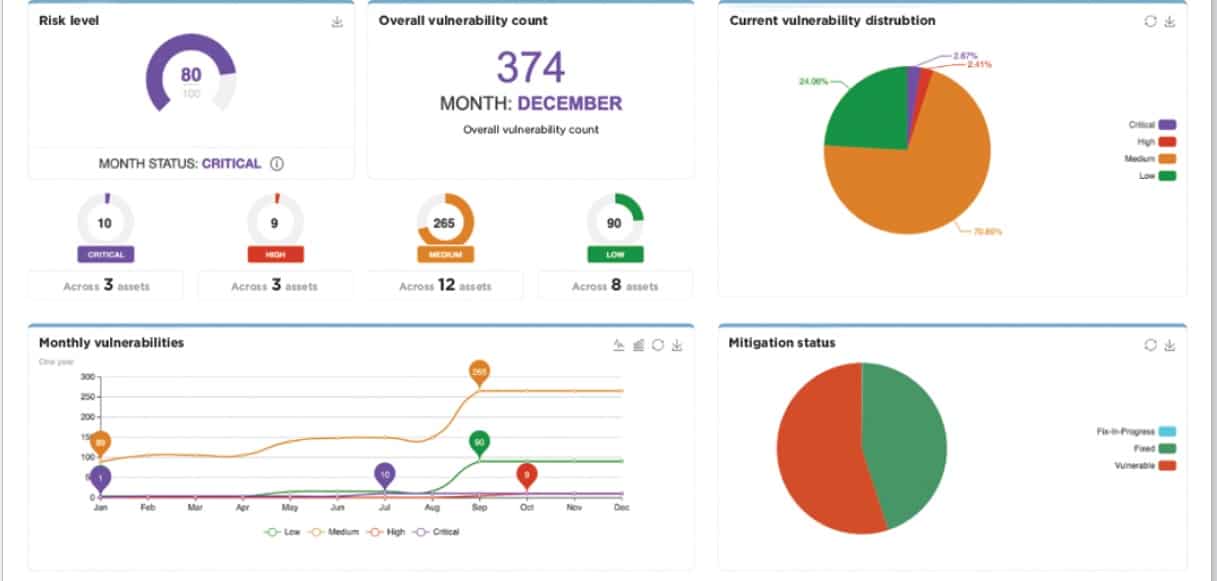
CoalFire Attack Surface Management approaches the problem of attack surface monitoring through fantastic automation and guidance-based support. The solution provides actionable security feedback through risk exposure and pen-testing tools, parsed into usable information with goals and projections on exactly how your DevSec team can remediate the identified issues.
Key Features:
- Comprehensive discovery features
- In-depth automation
- External attack surface monitoring
- Actionable data testing
- Remediation support and reporting
The tool can continually search the internet to monitor your external attack surface, producing vulnerability maps and useful dashboard data that you can proactively utilize on your DevSecOps projects, or your own network infrastructure.
CoalFire has a demo available for the software that can be requested from the company website. Still, for pricing, you will need to contact CoalFire directly for a personalized quote on pricing.
6. Burp Suite Enterprise
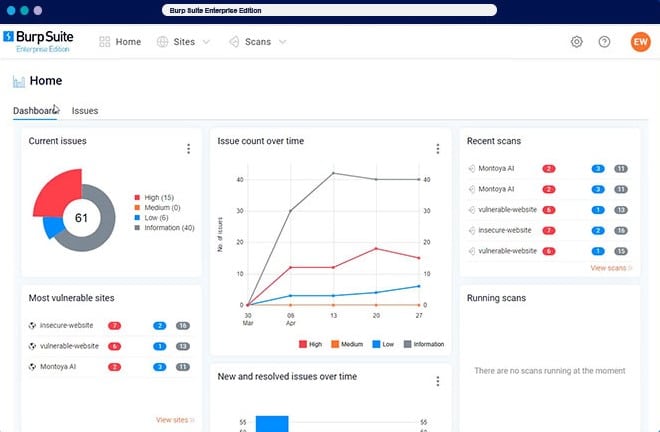
Burp Suite Enterprise Edition is an enterprise-scale vulnerability scanner platform that uses a lightweight deployable agent and a centralized dashboard that can perform thousands of scans. The system can perform web scans to find threats across your attack surface, with in-depth reporting tools, and role-based access.
Key Features:
- Lightweight deployable agent
- Perpetual web scans
- In-depth reporting and dashboarding options
- API and CI/CD pipeline integrations
- Threat prioritization
The system comes fully fitted with a substantial number of out-of-the-box integrations, with native Jira support and an API for customizable integration support. CI/CD plugins expand on your DevSecOps capabilities to ensure your pipeline is free of vulnerabilities. Threat prioritization helps you determine the best path for remediation, while the scanner perpetually checks for new threats and attacks surface vulnerabilities.
Burp Suite has a free trial available for the Enterprise edition. The product itself is divided into three tiers based on the number of required concurrent scans. The Starter version covers 5 concurrent scans and costs around $6,995 per year—the Grow version covers 20 concurrent scans and costs around $14,480 per year. Finally, the Accelerate version covers more than 50+ scans and costs around $29,450 per year.
7. UpGuard BreachSight
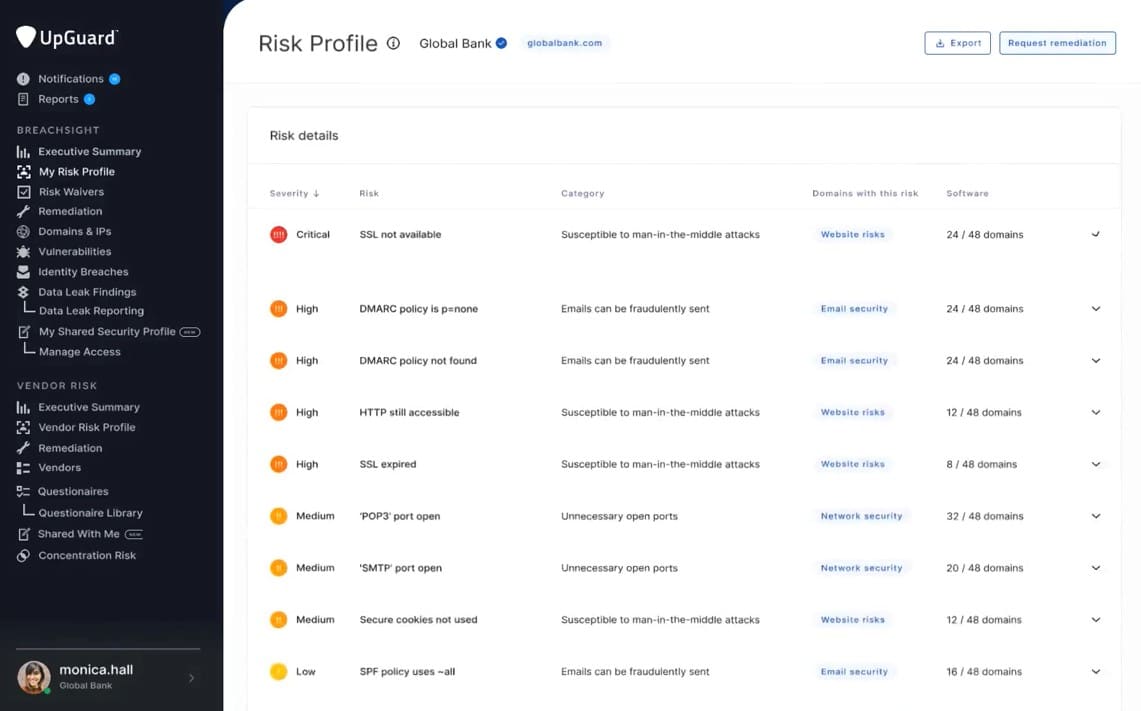
UpGuard BreachSight approaches the task of attack surface management through a modernized and easy-to-use solution, which abstracts complex feedback into usable information and simplified security ratings. This means the solution is best for those who aren’t as knowledgeable about how to remediate their attack surface, and the company's wide body of personalized support supports this approach.
Key Features:
- Abstracted security ratings for non-technical people
- Third-party security ratings
- Incidents & newsfeed
- Remediation planner and workflows
- Roles and permissions
Through the platform, you can set up customized alerting, with third-party vendor scoring that can notify you when their rating drops below your own designated threshold. There is an up-to-date and human-maintained news feed that updates you on the latest security trends and increases your overall knowledge of external security.
There is a 7-day free trial of the solution available, which isn’t an overly long period to rigorously test the platform, but it should be enough time to determine if the solution is suitable for your business.
Upguard also split its pricing into Small and Medium/Large businesses, with the small business package costing around $5,249 per year, while the Medium/Large packages cost between $15,749 and $83,999 per year.
8. Bugcrowd
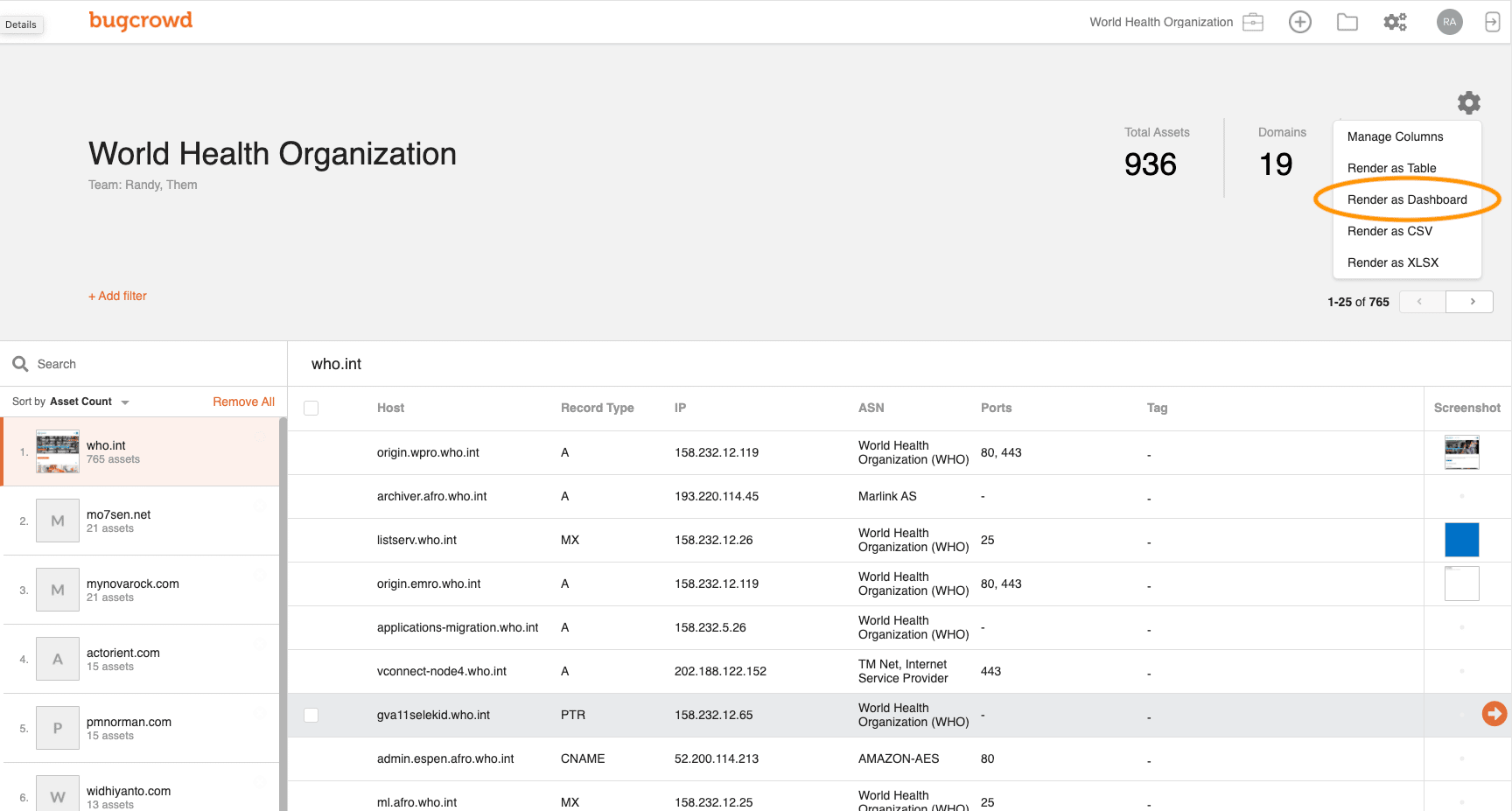
Bugcrowd isn’t a tool as much as it is a human-driven crowd-sourced analysis solution that pairs your business up with specialists that can help you identify and remediate your attack surface. The specialists that the company provides are lauded as expert ‘hackers’ who can turn the tide on vulnerability threats with a personal touch that software cannot provide.
Key Features:
- Human-driven solution
- Expert hacker specialists
- Asset discovery and management
- Comprehensive risk reporting
- Integrations with bug fixing and pen testing
The specialists provide full attack surface maps to detect forgotten and abandoned assets. They provide comprehensive risk reports, with details on exactly what is identified and what can be done to fix any discovered issues. The focus of the solution prioritizes asset discovery and management.
Bugcrowd offers a demo available on the company website. Since the solution relies on human specialists and isn’t a software tool, you need to speak with the company directly to get a quote for your exact business needs.
9. CyCognito
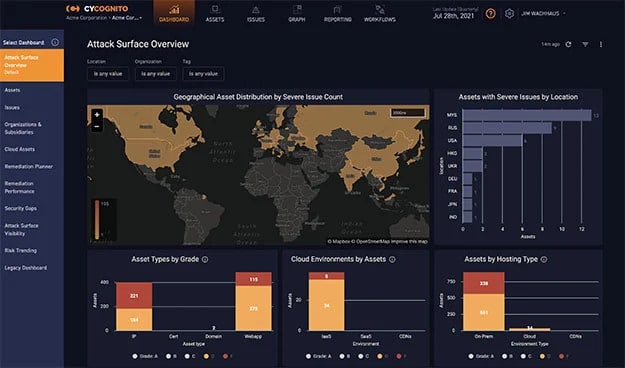
CyCognito presents a whole security platform built around external security, the main feature of which is the attack surface monitoring suite. The software presents several in-depth graphing and relationship discovery tools that help you map your entire external surface from the perspective of attackers. CyCognito also allows you to relate your results to your business context, which helps determine exactly what security vulnerabilities to prioritize.
Key Features:
- Cloud-based security platform
- High-risk prioritization with business context analytics
- In-depth attack surface insights
- Asset relationship graphing
- RESTful API
The solution gives detailed information on security threats in order or priority, so you can identify and secure high-risk targets with immediacy. There are also a vast number of available integrations presented in the platform, and a RESTful API for further customized expansion.
CyCognito presents a full demo of its features and is SaaS-based with customizable scalability requirements. The AWS version costs around $30,000 per year for 250 assets, but it is also available through several resellers.
10. Digital Shadows SearchLight
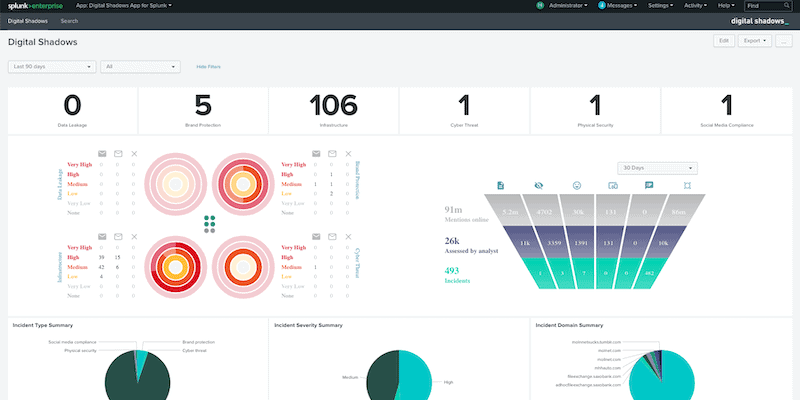
Digital Shadows Searchlight is a threat intelligence suite that provides information on your external security, including elements of your attack surface. Such features include the ability to perform cyber threat analysis and dark web searching to identify vulnerable assets or leaked data. You can also perform non-intrusive checkups on your third-party connections to determine if you have inadvertently exposed yourself to others.
Key Features:
- Intelligently filtered external threat reporting
- Third-party security analysis
- Cyber threat analysis
- Dark web scanning and reporting
- Data leak detection
Digital Shadows Searchlight focuses on filtering through ‘noisy’ external threat reports to give you specific mediation goals. They effectively manually parse through the data they collect and give you the rundown on what is important—saving your team the necessary time to go through the data yourself.
Digital Shadows present a 7-day free trial of their services, which should be enough time to determine if the service suits your exact business needs. After the trial, you can get a personalized quote on the pricing based on your business scale and the number of required assets.