Our funding comes from our readers, and we may earn a commission if you make a purchase through the links on our website.
What is SNMP? Basic Tutorial on NMS, MIBs, OIDs, Traps & Agents

UPDATED: February 6, 2023
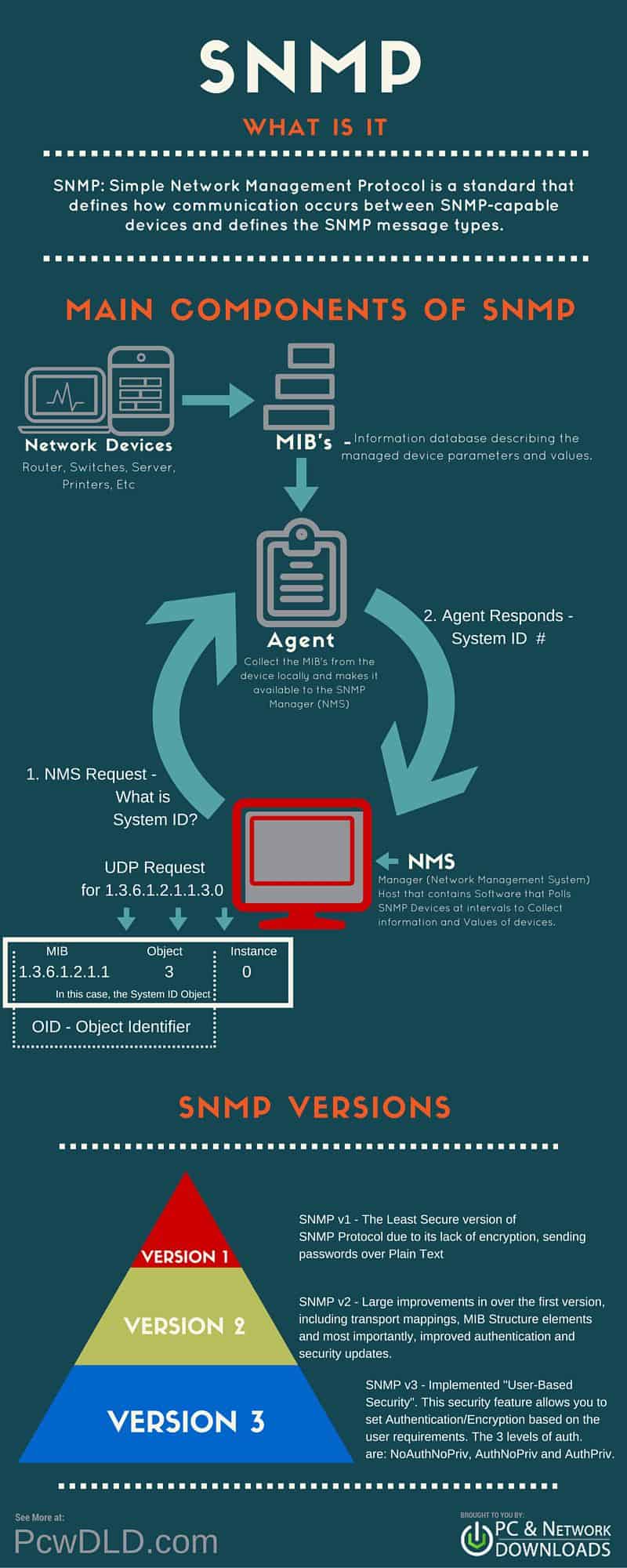
SNMP, which stands for Simple Network Management Protocol, is a communication protocol that lets you monitor managed network devices including Routers, Switches, Servers, Printers and other devices that are IP enabled all through a single management system/software.
If the networked device is SNMP capable, you can enable and configure it to start collecting information and monitor as many network devices as you want from a single point.
What does SNMP do?
- Monitor inbound and outbound Traffic flowing through the device
- Early Detection of faults within network devices along with Alerts/Notifications
- Analyzing data collected from devices over long periods of time to identify bottlenecks and performance issues
- Ability to remotely configure compatible devices
- Access and Control devices remotely that are connected via SNMP
The Basics
There are several components that allow SNMP to work correctly, inlcuding:
- SNMP Manager (Network Management System)
- SNMP Agents
- SNMP Port
- Managed Device (includes Servers, Switches, Routers, and more.)
- MIB (Management Information Base, also know as Management Information Database)
- OID (Object Identifier)
- Traps
- Versions
Manager (NMS)
The Manager component is simply a piece of software that is installed on a machine (which when combined, is called the Network Management System) that polls devices on your network how ever often you specify for information.
The Manager has the correct credentials to access information stored by Agents (which is explained in the next section) and then compiles them in a readable format for the Network Engineer or Administrator to monitor or diagnose for problems or bottlenecks.
Some NMS tools are more complex than others, allowing you to configure Email or SMS messages to alert you of malfunctioning devices on your network, while others simply poll devices for more basic information.
Agents
SNMP Agent is a piece of software that is bundled with the network device (router, switch, server, wifi, etc) that, when enabled and configured, does all the Heavy work for the Manager, by compiling and storing all the data from its given device into a database (MIB).
This database is properly structured to allow the Manager software to easily poll information and even send information to the Manager if an error has occured.
What Port Numbers does SNMP Use?
The manager Software in the previous section polls the agents at regular intervals over Port UDP 161.
SNMP Traps, which you'll read about further down, allows an Agent to send system and device information to the manager over Port UDP 162.
Although UDP is the common protocol used to by SNMP, TCP can also be used as well.
Managed Network Devices
Managed Network Devices, including Routers, Switches, Wifi, Servers (Windows and others), Desktop PC's, Laptops, Printers, UPS's, etc, have agent software built into them that needed to be either enabled and configured or simply configured properly in order to be polled by the NMS.
MIB
In short, MIB files are the set of questions that a SNMP Manager can ask the agent.
Agent collects these data locally and stores it, as defined in the MIB. So, the SNMP Manager should be aware of these standard and private questions for every type of agent.
Agents, as explained above, maintains a organized database of its devices parameters, settings, and more.
The NMS (Network Management system) polls/requests the Agent of a given device, which then shares its organized information from the database its made with the NMS, which then further translates it into alerts, reports, graphs and more.
The database that the Agent shares between the Agent is called the Management Information Base, or MIB.
MIB's contain a set of Values, both statistical and contol, that are defined by the network device. On many occassions, extensions of standard values are defined using a Private MIB by different vendors of networked devices.
To simplify MIB's, think of it like this: MIB files are the set of Questions that an Manager are allowed to ask the agent.
The Agent just collects these questions and stores them locally and serves them to the NMS when requested.
A Simplified Example of how MIB's work: The NMS will ask the network Device a Question, in this case, what is the Answer to Question 2?
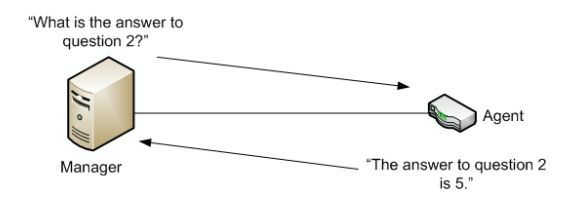
The managed network Devices' Agent then Responds with the Answer to the Question 2. To break this down even further, lets construct another example.
Say we want to know the System Uptime of a Device.
The NMS will send a Request to the Agent requesting the the System Uptime – the request is sent as a number with the MIB and the Object of Interest, along with something called theInstance.
OID = 1.3.6.1.2.1.1.3.0
Breakdown of OID Number
| MIB | Object of Interest | Instance |
|---|---|---|
| 1.3.6.1.2.1.1 | 3 | 0 |
| MIB | SysUptime Object | Instance |
The first 2 parts of the number sent to the Agent (MIB and Object of Interest, which in this case is System Uptime) is called the Object Identifier or OID.
As mentioned above, MIB's are Standard values that a Network Management System already knows about and can poll/request Network Devices about for information.
OID
OID, Object Identifier is a simply a number made up by the MIB, Object of Interest and the Instance. Each identifier is Unique to the device, and when queried will provide information on what has OID has been requested.
There are 2 types of OID's:
- Scalar
- Tabular
Scalar is a Single object Instance – for example, a Device’s vendor name. There can only be a Single vendor name, so this would be a scalar OID.
Tabular on the other hand, can have multiple results for its OID – for example, a Quad Core processor would result in 4 different CPU values.
Traps
Traps are used when the Device needs to alert the Network Management software of an event without being polled.
Traps ensure that the NMS gets information if an certain event occurs on the device that needs to be recorded without being Polled by the NMS first.
Managed network devices will have Trap MIBs with pre-defined conditions built into them.
Its crucial that the Network management system has these MIBs compiled into them to receive any traps sent by the given device/s.
MIBs are number that identify certain characteristics or values of a device, but if the Network Management system does not have a certain MIB that the network device Trap is sending, there is no way to interpret what the MIB is and will not record the event.
Versions (v1, v2c, v3)
This protocol has gone through several revisions over the years, dating back to 1988 starting with Version 1.
We are now up to Version 3, but most Network Network management systems support all versions of the protocol.
Version 1
Version 1 was the first version of the protocol defined in RFCs 1155 and 1157. This version is the simplest of the 3 versions of the protocol, and the most insecure, due to its plain text authentication.
Version 2 (or 2c)
Version 2 of the protocol was introduced in 1993, with large improvements in over the first version, including transport mappings, MIB Structure elements and most importantly, improved authentication and security updates.
Nevertheless, Version 1 and 2/2c had inherant security risks as mentioned above – the Community Strings, which are the equivalent to passwords, where the transmitted over the wire in clear/plain text, enabling anyone sniffing the network to gain access to the string and have the ability to compromise network devices and possibly reconfigure them using SNMP.
Version 3
Version 3 of the protocol made its debut in 1998, made greater strides to securing the protocol suite by implementing what is called “user-based security”.
This security feature allows you to set authentication based on the user requirements.
The 3 levels of authentication are as follows:
- NoAuthNoPriv: Users who use this mode/level have No Authentication and No privacy when they send/receive messages.
- AuthNoPriv: This Level requires the user to Authenticate, but will not Encrypt Sent/Received Messages.
- AuthPriv: Finally, the most secure level, where Authentication is Required and Sent/Received Messages are Encrypted.
Version 3 of the protocol is the most secure of the bunch, but with added security and encryption comes added configuration and complexity of setup and configuration.
But when dealing with higher level networking devices that contain sensitive information, the reward will outweigh the headache of setting it up correctly.
SNMP Infographic
Feel Free to embed this into your Blog or Site using the Embed Code below. (Your Free to use this Infographic on your Site as long as you use our Embed code w/ Link attribution included.)
<a href="http://www.pcwdld.com/what-is-snmp-and-tutorial"><img src="http://www.pcwdld.com/user/pages/what-is-snmp-and-tutorial/What-is-SNMP-Infographic.jpg">What is SNMP</a>
Now that you know What SNMP is and what it does, its time to get your hands dirty.
We recommended downloading a Network Management software and setting up several devices and start collecting SNMP traffic and stats to get a feel for its capabilities and flexibity.
SNMP FAQs
How does SNMP work?
SNMP works by sending management requests to network devices, which then respond with information about their status and configuration.
What are the benefits of using SNMP?
The benefits of using SNMP include: centralized network management, automatic collection of network data, and improved network performance.
What types of information can be collected using SNMP?
SNMP can be used to collect information about a wide range of network-related aspects such as device performance, error rates, and system uptime.
What are the different versions of SNMP?
The different versions of SNMP include SNMPv1, SNMPv2c, and SNMPv3.
How secure is SNMP?
The security of SNMP depends on the version and implementation, with SNMPv3 offering the highest level of security.
Can SNMP be used with different operating systems?
Yes, SNMP can be used with different operating systems, as long as the device has an SNMP agent installed.
How do you configure SNMP on a network device?
The configuration of SNMP on a network device depends on the specific device and manufacturer, but it typically involves enabling SNMP on the device, setting community strings, and configuring the device to send SNMP traps to the management system.
Checkout our related articles:
Traps, Monitoring Tools & Software, SNMPSoft Syslog Watcher Review, How to Enable Microsoft SNMP on Windows 7.



